MetaFilter: ☆彡 ☆彡 ☆彡 ☆彡 It was like fireworks. ☆彡 ☆彡 ☆彡
(Note it may take a few seconds for any of the thumbnails to load.) There are a few other Hirayama Fireworks booklets available, also through the Yokohama City Library archives, including an Illustrated Catalog of Day Light Bomb Shells (many of which appear to represent tiny figurines parachuted down from an exploding balloon).
Recent CPAN uploads - MetaCPAN: App-papersway-0.003
PaperWM-like window management for Sway/i3wm
Changes for 0.003 - 2024-04-19T13:26:43+01:00
- README improvements.
MetaFilter: No Tech for Apartheid organizers fired
I was fortunate to speak with Hasan Ibraheem, one of the employees fired as part of the protest and an organizer with No Tech For Apartheid, Thursday afternoon by phone. It was shortly after news broke that more than 100 Columbia students had been arrested by police in riot gear for a pro-Palestine protest. Ibraheem is a Syria-born, West Virginia-raised 23-year-old who worked at Google for one year and eight months. It was his very first job out of college. I asked him about getting arrested, how he found out he got fired, and his personal connection to this cause. (Ibraheem):...This campaign has been going on for about three years now, ever since Project Nimbus was created. And throughout those three years, we had tried basically every avenue possible to try and get the executives to talk to us, at least have some sort of conversation with us, sent petitions. We've exhausted every avenue that we could think of possible. And during that time, we've been building up our supporters in Google—everyone who's become part of No Tech For Apartheid. And then we wanted to do the strongest action we could possibly do because we have been ignored for three years. They wouldn't even give a statement or a conversation with us. So we wanted to make it impossible for them to ignore us. Relatedly, last week Billy Perrigo of Time reported thusly: Google provides cloud computing services to the Israeli Ministry of Defense, and the tech giant has negotiated deepening its partnership during Israel's war in Gaza, a company document viewed by TIME shows. The Israeli Ministry of Defense, according to the document, has its own "landing zone" into Google Cloud—a secure entry point to Google-provided computing infrastructure, which would allow the ministry to store and process data, and access AI services. More coverage from The Register, The Verge, and Democracy Now. Previously in MetaFilter: Comment 1 and comment 2, both from cendawanita in 'Lavender': The AI machine directing Israel's bombing spree in Gaza, a recent post from brundlefly.
Hackaday: NASA’s Ingenuity Mars Helicopter Transitions Into Stationary Testbed

On April 16th NASA announced the formal end to Ingenuity’s days as the first ever Martian helicopter, following its 72nd and final flight mission in January. This flight ended with a rough landing during which the helicopter’s blades got damaged and separated, leaving the plucky flying machine with its wings clipped. During the final meet-up of the Mars Helicopter Team there was cake, but none for Ingenuity as its latest data set was reviewed by the team from 304 million kilometers away. This data confirms the latest software patch allows it to work stand-alone as a data collection platform.
With these latest software changes, Ingenuity will wake up daily, activate its computers and perform a self-check of all its components before collecting sensor data and images. The main goal of this is to collect long-term performance data on the helicopter’s systems, with enough onboard memory to allow for measurements to be stored for around 20 years. This means that although the Perseverance rover will have to trundle on without its flying mission buddy, one day in the future another rover, helicopter or primate will presumably drop by to either communicate with Ingenuity if it’s still alive, or harvest its memory unit for data retrieval.
Thanks to [Mark Stevens] for the tip.
Recent CPAN uploads - MetaCPAN: OpenTelemetry-SDK-0.022
An implementation of the OpenTelemetry SDK for Perl
Changes for 0.022 - 2024-04-19T11:46:54+01:00
- Do not call start on the background function in the batch span processor, this is handled automatically by the loop (GH #13)
Recent additions: warp-tls 3.4.5
HTTP over TLS support for Warp via the TLS package
Recent additions: tls 2.0.4
TLS protocol native implementation
Slashdot: FBI Says Chinese Hackers Preparing To Attack US Infrastructure
Read more of this story at Slashdot.
MetaFilter: Mini rope bridges built in Forest of Dean to help dormice
Additional dormice info: hazel dormice described by the Woodland Trust. The State of Britain's Dormice 2023 (pdf). Gloucestershire Wildlife Trust Dormice in Danger (pdf). And snoring dormouse (MetaFilter).
Open Culture: Discover the Singing Nuns Who Have Turned Medieval Latin Hymns into Modern Hits
We now live, as one often hears, in an age of few musical superstars, but towering ones. The popular culture of the twenty-twenties can, at times, seem to be contained entirely within the person of Taylor Swift — at least when the media magnet that is Beyoncé takes a breather. But look past them, if you can, and you’ll find formidable musical phenomena in the unlikeliest of places. Take the Poor Clares of Arundel, a group of singing nuns from Sussex who, during the COVID-19 pandemic, “smashed all chart records to become not only the highest-charting nuns in history, but also the UK’s best-selling classical artist debut,” reports Classic FM’s Maddy Shaw Roberts.
“Music is at the heart of the nuns’ worship,” writes the Guardian’s Joanna Moorhead, but the idea of putting out an album “came about initially as a bit of a joke.” Not long after receiving a visit from a curious music producer, the singing Poor Clares — skilled and unskilled alike — found themselves in a proper recording studio, laying down tracks.
Roberts describes the resulting debut Light for the World as “a collection of Latin hymns produced for a twenty-first century audience, bringing calm and beauty during a time when so many were separated from their loved ones.” Just a few weeks ago, they released its follow-up May Peace I Give You, the video for whose title track appears at the top of the post.
May Peace I Give You comes from Decca Records, a label famous in part for their rejection, in 1962, of a scruffy rock-and-roll band called the Beatles. Presumably determined not to make the same mistake twice, they’ve since taken chances on all manner of acts, starting with the Rolling Stones; over the decades, they’ve reached beyond the well-trodden spaces in popular and classical music. The success of the Poor Clares goes to show that this practice continues to pay off, and that — like the popular Gregorian chant and gospel booms of decades past — venerable holy music retains its resonance even in our trend-driven, not-especially-religious age. And as the promotion of their new Abbey Road-recorded album proves, even for the monastically disciplined, some temptations are irresistible.
via Classic FM
Related content:
Manuscript Reveals How Medieval Nun, Joan of Leeds, Faked Her Own Death to Escape the Convent
Based in Seoul, Colin Marshall writes and broadcasts on cities, language, and culture. His projects include the Substack newsletter Books on Cities, the book The Stateless City: a Walk through 21st-Century Los Angeles and the video series The City in Cinema. Follow him on Twitter at @colinmarshall or on Facebook.
Hackaday: Build Your Own RGB Fill Light For Photography

Photography is all about light, and capturing it for posterity. As any experienced photographer will tell you, getting the right lighting is key to getting a good shot. To help in that regard, you might like to have a fill light. If you follow [tobychui]’s example, you can build your own!

The build relies on addressable WS2812B LEDs as the core of the design. While they’re not necessarily the fanciest LEDs for balanced light output, they are RGB LEDs, so they can put out a ton of different colors for different stylistic effects. The LEDs are under the command of a Wemos D1, which provides a WiFI connection for wireless control of the light.
[tobychui] did a nice job of building a PCB for the project, including heatsinking to keep the array of 49 LEDs nice and cool. The whole assembly is all put together inside a 3D printed housing to keep it neat and tidy. Control is either via onboard buttons or over the WiFi connection.
Files are on GitHub if you’re seeking inspiration or want to duplicate the build for yourself. We’ve seen some other similar builds before, too. Meanwhile, if you’re cooking up your own rad photography hacks, don’t hesitate to let us know!
Open Culture: Watch Stalker, Andrei Tarkovsky’s Mind-Bending Masterpiece Free Online
“I feel like every single frame of the film is burned into my retina,” said Oscar-winning actress Cate Blanchett about the movie Stalker (1979). “I hadn’t seen anything like it before and I haven’t really seen anything like it since.
Andrei Tarkovsky’s final film in the USSR seems like an unlikely movie to have a devoted, almost cultish, following. It is a dense, multivalent, maddeningly elusive work that has little of the narrative pay-offs of a Hollywood movie. Yet the film is so slippery and so seemingly pliable to an endless number of interpretations that it requires multiple viewings. “I’ve seen Stalker more times than any film except The Great Escape,” wrote novelist and critic Geoff Dyer,” and it’s never quite as I remember. Like the Zone, it’s always changing.”
The movie’s story is simple: a guide, called here a Stalker, takes a celebrated writer and a scientist from a rotting industrial cityscape into a verdant area called The Zone, the site of some undefined calamity which has been cordoned off by rings of razor wire and armed guards. There, one supposedly can have their deepest, darkest desires fulfilled. Yet even if you manage to give the guards a slip, there are still countless subtle traps laid by whatever sentient intelligence that controls the Zone. Rationality is of no help here. One can only progress along a meandering path that can only be followed by intuition.
The Stalker, with his shaved head and a perpetually haunted expression on his face, is a sort of holy fool; a man who is both addicted to the strange energy of the Zone and bound to help his fellow man. His clients’ motives, however, are far less altruistic. Once deep in the room, the three engage in a series of philosophical arguments that quickly turns personal.
The movie’s power, however, is not found in traditional dramatics. Instead it’s a cumulative effect of Tarkovsky’s hypnotic pace, his philosophical commentary and perhaps most of all his imagery. Shot with smudgy, almost completely desaturated colors, the world outside the Zone seems to be a grim, dismal place – as if Tarkovsky were trying to evoke the industrial hellscape of Eraserhead by way of Samuel Beckett. (Stalker was in fact shot in an industrial wasteland outside of Tallinn, Estonia, down river from a chemical plant. Exposure to that plant’s runoff might very well have caused the filmmaker’s death.) Inside the Zone, however, the surroundings are lush and colorful, filled with glimpses of inexplicable wonder and beauty.
Stalker screenwriter Arkady Strugatsky once said that the movie was not “a science fiction screenplay but a parable.” The question is, a parable of what? Religious faith? Art? The cinema itself? Reams of paper have been devoted to this question and I’m not offering any theories. Tarkovsky himself, in his book Sculpting Time, wrote “People have often asked me what The Zone is, and what it symbolizes…The Zone doesn’t symbolize anything, any more than anything else does in my films: the zone is a zone, it’s life.”
Of course, that explanation does little to explain the film’s startling, utterly cryptic final minutes.
Above, you can watch the film online, thanks to Mosfilm. You can also find other Tarkovsky films in the Relateds below.
Related Content:
Watch Andrei Tarkovsky’s Films Free Online: Stalker, The Mirror & Andrei Rublev
Andrei Tarkovsky’s Very First Films: Three Student Films, 1956–1960
Andrei Tarkovsky Answers the Essential Questions: What is Art & the Meaning of Life?
Jonathan Crow is a Los Angeles-based writer and filmmaker whose work has appeared in Yahoo!, The Hollywood Reporter, and other publications. You can follow him at @jonccrow. And check out his blog Veeptopus, featuring lots of pictures of vice presidents with octopuses on their heads. The Veeptopus store is here.
Recent additions: mmzk-typeid 0.6.0.0
A TypeID implementation for Haskell
MetaFilter: Confidence is a preference for the habitual voyeur
Recent additions: tmp-proc 0.6.2.0
Run 'tmp' processes in integration tests
MetaFilter: Friday Itch.io Fun: Neltris
Penny Arcade: Stranger Danger
Slashdot: Northrop Grumman Working With SpaceX On US Spy Satellite System
Read more of this story at Slashdot.
Recent additions: grisette 0.5.0.1
Symbolic evaluation as a library
Hackaday: PC Watercooling Prototype is Pumpless

Watercooling is usually more efficient than air cooling for the same volume of equipment, and — important for many people — it is generally quieter. However, you still have water pump noises to deal with. [Der8auer] got a Wieland prototype cooler that doesn’t use a pump. Instead, it relies on the thermosiphon effect. In simple terms, the heat moves water — possibly boiling it — upwards to a radiator. Once the water is cool, it falls down back to the heat exchanger again.
It looks like any other AIO, but the block is extremely flat compared to normal coolers, which have the pump on top of the plate. As you might expect, orientation matters, and you can’t have tight bends in the hoses. The system also has to be totally airtight to function properly. The test was meant to be against a commercial AIO unit with the same number of fans. However, there was a problem, and the final test was done with a larger radiator with one of its three fans removed.
The prototype performed fine and was quiet. It didn’t do as well as the commercial cooler, but it wasn’t bad. Of course, this is a prototype. Maybe a final product will do better. Around the ten-minute mark, the IR camera came out, and it didn’t show any major unexpected hot spots.
We’ve seen water-cooled printer hotends, and pumping is a problem there. We wondered if this technology might work there. The whole thing reminded us of heat pipes without the internal wick to move cold working fluid. We’ve even seen a water-cooled calculator.
Recent CPAN uploads - MetaCPAN: Finance-Quote-1.61
Get stock and mutual fund quotes from various exchanges
Changes for 1.61 - 2024-04-18T21:34:24-07:00
- SIX.pm - Changed lookup for currency, added lookups for symbol and last. Issue #380
- YahooJSON.pm - URLs to retrieve required cookies and crumbs were changed to allow EU based users to use the module. Issue #373
Recent CPAN uploads - MetaCPAN: App-BPOMUtils-Table-FoodIngredient-0.021
List ingredients in BPOM processed food division
Changes for 0.021 - 2024-04-19
- [ux] Add shorter alias for bpom-list-food-ingredients-rba: bpomfi.
Recent CPAN uploads - MetaCPAN: App-BPOMUtils-Table-FoodAdditive-0.019
List registered food additives in BPOM
Changes for 0.019 - 2024-04-19
- [ux] Add short alias for bpom-list-food-additives: bpomfa.
Slashdot: Reddit Is Taking Over Google
Read more of this story at Slashdot.
Hackaday: Computing Via (Virtual) Dominos

Back in 2012, [Matt Parker] and a team built a computer out of dominos for the Manchester Science Festival. [Andrew Taylor], part of the team that built the original, has built a series of virtual domino puzzles to help explain how the computer worked. He also links to a video from the event, but be warned: the video contains some spoilers for the puzzles. If you are ready for spoilers, you can watch the video below.
The original computer could add two three-bit numbers and provide a four-bit result. We don’t want to give away the answers, but the inverter is quite strange. If you don’t want to puzzle it out, you can press the “reveal answer” to see [Andrew’s] solutions. Press “play” and watch the dominos fall.
Of course, building an adder is a far cry from building a computer, but at 10,000 dominos, a real computer would be difficult, though clearly possible. This is especially true when you consider that these logic gates can only run once, so testing is a bear. The fact that knocking over a domino takes it out of play is exactly how many of the gates work, too, but that’s the only hint we’ll give.
We couldn’t help but think of the Three Body Problem’s human computer. If you prefer your domino logic to be non-interactive, we’ve covered another presentation on the topic.
Slashdot: Ubuntu 24.04 Yields a 20% Performance Advantage Over Windows 11 On Ryzen 7 Framework Laptop
Read more of this story at Slashdot.
Slashdot: Netflix Blows Past Earnings Estimates As Subscribers Jump 16%
Read more of this story at Slashdot.
Colossal: 13 Bronze Figures Reinterpreted from Velázquez’s ‘Las Meninas’ Line Up in a Central Venice Plaza

‘Las Meninas a San Marco’ (2024). All images courtesy of Contini Art Gallery, shared with permission
Thirteen bronze women in wide pannier skirts stand single file in St. Mark’s Square in central Venice. The large-scale installation is the work of Spanish artist Manolo Valdés and on view for the 60th Venice Biennale that opened earlier this month.
Known for recontextualizing the iconic figures, colors, and textures throughout Western art history, Valdés once again pulls from well-known source material for Las Meninas a San Marco as he reinterprets the subjects of Diego Velázquez’s 1656 painting “Las Meninas,” or “The Ladies-in-waiting.” Led by the monumental “Infanta Margarita” who stands at the center of the original painting, the trailing figures are “Reina Mariana,” a nod to the infanta’s mother framed in a portrait in the background of Velzázquez’s work.
Las Meninas a San Marco has come under fire from Italia Nostra-Venezia, an organization that opposes galleries paying for public spaces to stage artworks and what it calls the “‘biennalization’ of the city.”
The project will be on view through June 15, when one of the “Reina Mariana” sculptures will be donated to the city.





Do stories and artists like this matter to you? Become a Colossal Member today and support independent arts publishing for as little as $5 per month. The article 13 Bronze Figures Reinterpreted from Velázquez’s ‘Las Meninas’ Line Up in a Central Venice Plaza appeared first on Colossal.
Hackaday: Remove Wall Plugs Fast With A Custom Tool

The best thing about buying your own home is that you can hang things on the walls. It’s a human right all too often denied to renters the world over. Regardless, five years later, when you’re doing the mandatory minimalist remodel, you’ll be ruing the day you put in all those wall anchors. At that point, consider removing them with this nifty tool from [XDIY with Itzik].
The design aims to remove wall anchors as cleanly as possible. It’s easiest to watch the video to get the idea of how it works.
The tool features a block which holds a bearing. That bearing acts as a rotating stop for a wood screw. The idea is that you place the block against the wall, and use a power drill to drive a wood screw into the anchor at high speed. The screw can’t move forward, so the threads basically yank the plug out of the wall, and relatively neatly at that. Once removed, there’s a little push stopper you can use to hold the old plug in place as you remove the wood screw from the device, ready to go again.
[Itzik] demonstrates the device by removing ten wall plugs in just 40 seconds. If you’ve got a lot to do, or it’s a job you do regularly, you might like to have this tool in your kit.
Oftentimes, having the right tool can make a job ten times faster, and this seems like one of those cases. Video after the break.
ScreenAnarchy: Shudder in May: NIGHTWATCH: DEMONS ARE FOREVER, STOPMOTION And a Lot of TOXIC AVENGER Movies
 We believe it is safe to say that Spring is finally here in North America. Relatively safe. Pretty sure it is safe. Not only will April showers bring May flowers but May also sees the arrival of the new Danish horror flick Nightwatch: Demons Are Forever, and the UK horror flick, Stopmotion. Next month also sees the ongoing live watch parties every other Friday night of The Last Drive-In with Joe Bob Briggs. Four Toxic Avenger films are coming to the repertory programming next month. We don't know if Bob Clark's Deathdream and Buddy Giovinazzo's Combat Shock are considered part of the Namsploitation genre but they're two Nam-era horror flicks to keep an eye out for next month. While we still don't know what...
We believe it is safe to say that Spring is finally here in North America. Relatively safe. Pretty sure it is safe. Not only will April showers bring May flowers but May also sees the arrival of the new Danish horror flick Nightwatch: Demons Are Forever, and the UK horror flick, Stopmotion. Next month also sees the ongoing live watch parties every other Friday night of The Last Drive-In with Joe Bob Briggs. Four Toxic Avenger films are coming to the repertory programming next month. We don't know if Bob Clark's Deathdream and Buddy Giovinazzo's Combat Shock are considered part of the Namsploitation genre but they're two Nam-era horror flicks to keep an eye out for next month. While we still don't know what...
ScreenAnarchy: HANKY PANKY Review: Cheap, Dumb, Delightful
 Lindsey Haun and Nick Roth directed the horror comedy, available April 19 on VOD. "It's a silly movie that just wants to make its audience smile, and it succeeds."
Lindsey Haun and Nick Roth directed the horror comedy, available April 19 on VOD. "It's a silly movie that just wants to make its audience smile, and it succeeds."
Saturday Morning Breakfast Cereal: Saturday Morning Breakfast Cereal - K

Click here to go see the bonus panel!
Hovertext:
SMBC is the 74-almost funniest webcomic.
Today's News:
If you were a patreon subscriber, you would be seeing my magnum opus at this very moment.
ScreenAnarchy: ABIGAIL Review: Ballet Gets Bloody Entertaining
 It's a juggling act to get an entertaining horror film - one that's fun, funny, yet still scary, with a good share of violence and gore, a decent story with snappy dialogue, and a monster that an audience can root for, maybe more than the heros. Radio Silence - directors Matt Bettinelli-Olpin and Tyler Gillett, and producer Chad Villella - have been (mostly) pulling this off, with a particular formula that has worked with slasher and pseudo-slasher films such as Ready or Not and Scream (2022). If it isn't broken, don't fix it, and hence we have Abigail. A solid piece of horror action comedy, a story that moves from crime caper to pseudo-slasher with an engaging monster, it's not without its flaws, but it's...
It's a juggling act to get an entertaining horror film - one that's fun, funny, yet still scary, with a good share of violence and gore, a decent story with snappy dialogue, and a monster that an audience can root for, maybe more than the heros. Radio Silence - directors Matt Bettinelli-Olpin and Tyler Gillett, and producer Chad Villella - have been (mostly) pulling this off, with a particular formula that has worked with slasher and pseudo-slasher films such as Ready or Not and Scream (2022). If it isn't broken, don't fix it, and hence we have Abigail. A solid piece of horror action comedy, a story that moves from crime caper to pseudo-slasher with an engaging monster, it's not without its flaws, but it's...
Colossal: With Few Glimmers of Hope, the World Press Photo Contest Documents War, Migration, and Devastation

“The Two Walls” by Alejandro Cegarra, The New York Times/Bloomberg. A migrant walks atop a freight train known as “The Beast.” Migrants and asylum seekers lacking the financial resources to pay a smuggler often resort to using cargo trains to reach the United States border. This mode of transportation is very dangerous; over the years, hundreds have fallen onto the tracks and have been killed or maimed. Piedras Negras, Mexico, October 8, 2023. All images courtesy of World Press Photos, shared with permission
From Israel’s ongoing assault leaving the people of Gaza in horrific destitution to a record-breaking surge of migrants at the U.S.-Mexico border, the last year has seen incredible devastation around the globe. The 2024 World Press Photo contest gathers a profound and illuminating collection of images that approach myriad crises with compassion and clarity.
This year’s competition garnered 61,062 entries from 3,851 photographers in 130 countries. The winning images include a striking black-and-white shot of a man mid-step as he perilously crosses from one moving train car to the next in Piedras Negras and a portrait of an Afghan woman resting on a couch amid the desolate mountain landscape at a refugee camp near the Pakistan-Afghanistan border.

“Afghanistan on the Edge” by Ebrahim Noroozi, Associated Press. An Afghan refugee rests in the desert next to a camp near the Torkham Pakistan-Afghanistan border, in Torkham, Afghanistan, Friday, November 17, 2023. A huge number of Afghans refugees entered the Torkham border to return home hours before the expiration of a Pakistani government deadline for those who are in the country illegally to leave or face deportation.
One of the few hopeful submissions, Jaime Rojo’s “Saving the Monarchs,” looks up at innumerable butterflies fluttering among the trees of El Rosario sanctuary in Michoacán, Mexico. Due to encroaching industry and a changing climate, the insect population had been in sharp decline since the 1990s, although international efforts have reversed the downturn by more than 80 percent. “This beautiful yet powerful story—a symbol of unity in polarized times—offers a solutions-oriented perspective on environmental change and conservation,” a statement about the series says.
In 2023, 99 journalists and media workers died, about 75 percent of whom were killed in the Israel-Hamas war. It was one of the deadliest years on record, with 2024 already approaching that number. “Work, for a news photographer, can be a dangerous place,” the organization says. “Unlike other journalists, news photographers must be where the story is happening— which might be a war zone, a humanitarian disaster, or somewhere free and open media is not welcomed.” The collection, therefore, is also a stark reminder of the people behind the lens and the risks they take to share essential information.
World Press Photo will bring the winning images to more than 20 cities in the coming months, and if you’re interested in diving deeper into the stories behind the shots, pick up the 2024 yearbook.

“Israeli Airstrikes in Gaza” by Mustafa Hassouna, Anadolu Images. A resident of al-Zahra walks through the rubble of homes destroyed in Israeli airstrikes. The strikes hit around 25 apartment blocks in the university and residential neighborhood. At the time of writing, March 4, 2024, Israel’s attacks on the occupied Palestinian territories during the Israel-Hamas war had killed some 30,000 people and injured more than 70,000. Gaza City, Gaza, October 19, 2023.

“The Edge” by Zishaan A Latif. Bengali-speaking Hindus and Muslims help each other shift shops from the edge of the Brahmaputra river at the Tarabari ferry point. The shifting is done in anticipation of the erosion of land that occurs with each monsoon season, which is often devastating for residents as they are forced to constantly adapt to a changing landmass each year. Tarabari, Bahari constituency, Barpeta district, Lower Assam, India, June 15, 2023.

“Kakhovka Dam: Flood in a War Zone” by Johanna Maria Fritz, Ostkreuz, for Die Zeit. A peony bush submerged in floodwater on an island in the Dnipro River. The city’s proximity to the frontline hampered rebuilding efforts. Kherson, Ukraine, June 7, 2023.

“Saving the Monarchs” by Jaime Rojo for National Geographic. Butterflies stream through the trees in El Rosario, a sanctuary within the Monarch Butterfly Biosphere Reserve in Michoacán, Mexico. Migrating monarchs winter in the same oyamel fir groves that sheltered earlier generations.

“Red Skies, Green Waters” by Adriana Loureiro Fernandez for The New York Times. Neighbors play Animal Lotto under a sky lit by one of the world’s largest gas flares. Punta de Mata, Venezuela, November 5, 2022.

“Fighting, Not Sinking” by Eddie Jim, The Age/Sydney Morning Herald. Kioan Climate Emergency Declaration meetings on Kioa Island, Fiji. Kioa island resident Lotomau Fiafia and his grandson John, Lotomau was born on the island in 1952, he saw the changes of the shoreline in the past decades, picture of him standing in the water roughly where the shoreline used to be when he was young, and now its up to his chest. August 8, 2023.

“Pollution in the Cileungsi River” by Arie Basuki. Residents catch fish on the Cileungsi River, which is polluted by factory waste at Curug Parigi, Bogor, on August 8, 2023. In the dry season, when other areas of the river experience drought, the Cileungsi River has now been polluted with toxic and dangerous industrial waste, which is pitch black, foamy, and smelly. As a result, the supply of clean water, the main water source that comes from the Cileungsi River in the Bekasi area, is disrupted.

“No Man’s Land” by Daniel Chatard. Police and RWE energy company security officers block activists belonging to the Ende Gelände action alliance, who have entered the Hambach open-pit mine. Kerpen, Germany, November 5, 2017.
Do stories and artists like this matter to you? Become a Colossal Member today and support independent arts publishing for as little as $5 per month. The article With Few Glimmers of Hope, the World Press Photo Contest Documents War, Migration, and Devastation appeared first on Colossal.
ScreenAnarchy: Calgary Underground 2024: Curtain Raiser
 The Calgary Underground Film Festival (CUFF) opens its 21st edition today, and runs until April 28th. Western Canada's largest showcase of genre film, offbeat documentaries, and industry events is housed in the two-screen (stacked on top of one another) Globe Cinema in the heart of Calgary. Filmmakers John Waters and Vincenzo Natali are in attendance to discuss their careers (accompanied by multiple retrospective screenings), as well as David Cronenberg's daughter Caitlin debuting her first feature, along with a number of guest filmmakers, industry, and panelists who will be converging on the festival. CUFF's place on the calendar offers a role for the festival to act as a curated catchall of wild, experimental, and indie cinema: a sampler from international festivals, blended in with the work of local filmmakers,...
The Calgary Underground Film Festival (CUFF) opens its 21st edition today, and runs until April 28th. Western Canada's largest showcase of genre film, offbeat documentaries, and industry events is housed in the two-screen (stacked on top of one another) Globe Cinema in the heart of Calgary. Filmmakers John Waters and Vincenzo Natali are in attendance to discuss their careers (accompanied by multiple retrospective screenings), as well as David Cronenberg's daughter Caitlin debuting her first feature, along with a number of guest filmmakers, industry, and panelists who will be converging on the festival. CUFF's place on the calendar offers a role for the festival to act as a curated catchall of wild, experimental, and indie cinema: a sampler from international festivals, blended in with the work of local filmmakers,...
Greater Fool – Authored by Garth Turner – The Troubled Future of Real Estate: The redneck tax
The finance minister, she of The Budget Bomb, owns a couple of rentals with her husband, Graham, in the UK. Makes sense, since he’s a British writer and reporter for the NY Times. She also owns a hunk of a property in Alberta (in partnership). But apparently there’s no family cottage.
Good thing. She just declared war on them.
You may have heard the feds say yesterday, when the punitive capital gains tax was bloated, that just the rich would be affected. “Only 0.13 per cent of Canadians with an average income of $1.42 million are expected to pay more personal income tax on their capital gains in any given year,” said the budget. But that’s a lie. We all know it.
People dumping investment rental properties like hers – because of anti-landlord regulations (which her Renter Bill of Rights encourages) – could be whacked by this change. Family trusts just had the rug pulled out from under them. And many unsuspecting cottage owners, plus their children, could be in for a rude surprise.
First, understand what’s going on in cottage country. It ain’t happy stuff.
Covid, then 6% mortgages, pretty much spanked the recreational property market hard. Sales cratered. Prices followed. For example, a year ago average sale prices in Ontario’s prime Kawartha region crashed 32% year/year – from a crazy $1.24 million all the way down to a still-nuts $855,900.
Since then, no real recovery happened even as mortgage rates trimmed. Sales are running 35% below the 10-year average. The Lakelands real estate cartel reports another 1% drop in prices this year. The benchmark Frankenumber for single-family homes is currently $708,000. The median value of prime waterfront homes is just over nine hundred.
Scarier for people with big cottage mortgages who can’t sell is an increasing default rate in lake country – which pressures prices and encourages vultchers. Now Chrystia is swooping in for the kill, with a shocking change set for the Tuesday prior to the pivotal long Canada Day weekend.
So the tax on capital gains is growing. Instead of including half of an entire gain in income – regardless of the size – now two-thirds of the profit above $250,000 will be taxable. So on that $940,000 waterfront property you paid $300,000 for twenty years ago, the tax goes from $96,000 (if your tax bracket is around 30%) to $115,890.
What to do?
If you’ve been thinking about bailing out of the cottage, sell. But, of course, it’s already too late. There’s probably a zero chance of prepping and listing the place, going to market and eventually finding a buyer then closing the deal in the next eight weeks.
What about gifting it to your kids?
Then hurry. That takes some time, too. And gifting also means you’ll be on the hook for capital gains tax, and at the same rate. (Only principal residences can be passed along without the CRA getting its talons into you.)
Another option, if your kid weirdly doesn’t want the mouse-infested shack in the middle of tick heaven, is to declare the cottage your principal residence once you’re able to snare a buyer. As this blog has explained in the past, you’re allowed to pick a property in any tax year as your PR, and sell without being taxed on the gain. But in order to do that, you must actually occupy the place during a portion of the year, and it knocks your city home out of contention for a tax-free profit.
If you have no intention of selling, accept the cap gains hike is probably going to cost equity. This is a significant negative for the entire recreational property market – cabins, hobby farms, lakefront McMansions or off-grid retreats. And it makes you wonder how long it will be before the Libs (if re-elected in 2025) drop that $250,000 quota and make 67% of all gains taxable at the personal marginal rate. That would also whack everyone with a non-registered portfolio account. Ouch.
But then, we know the federal government does not want you to have a rustic cottage, a bunker or even an F-150 with a gun rack and a thirsty gasoline engine. The future is density. Condos. Urbanity. EVs and fourplexes. That way she can keep an eye on you. Hick.
About the picture: “I’m 33 and live in Toronto in a rent controlled building where I have been for 10 years,” writes Erik. “My rent is a hilarious $1400/month for 2 bedrooms, so I have accepted the fact I should not move anytime soon if I want to save any money for other things. I am content with that after re-wiring my brain (you know… the infamous “but son you gotta have a house” mindset that had to be undone). Here is a picture of my Pup, Iris, because she looks very majestic on this one and she is what keeps me sane these days. Do not let the proper pose fool you, though. She is a complete weirdo generally speaking.”
To be in touch or send a picture of your beast, email to ‘garth@garth.ca’.
ScreenAnarchy: THE GREATEST HITS Interview: Ned Benson, Lucy Boynton, Justin H. Min on Los Angeles and Everchanging Relationships with Music
 In my review of The Greatest Hits, the new sci-fi romance from The Disappearance of Eleanor Rigby writer/director Ned Benson, I mention that it opens with a montage of two young lovers “generally doing things that young, hip couples do in LA.” So, as someone from Los Angeles, I couldn’t help but pick the brains of Benson and stars Lucy Boynton and Justin H. Min about my hometown when I recently had the chance to sit down with them … in Chicago, where I now live. Because The Greatest Hits is a movie about the power of music to literally transport protagonist Harriet (Boynton) back in time, we also talked about music. But less specific artists (though some come up), and more the ways that...
In my review of The Greatest Hits, the new sci-fi romance from The Disappearance of Eleanor Rigby writer/director Ned Benson, I mention that it opens with a montage of two young lovers “generally doing things that young, hip couples do in LA.” So, as someone from Los Angeles, I couldn’t help but pick the brains of Benson and stars Lucy Boynton and Justin H. Min about my hometown when I recently had the chance to sit down with them … in Chicago, where I now live. Because The Greatest Hits is a movie about the power of music to literally transport protagonist Harriet (Boynton) back in time, we also talked about music. But less specific artists (though some come up), and more the ways that...
Colossal: Hadi Rahnaward’s Fraying Rug of Charred and Pristine Matchsticks Crumbles Under Violence

Hadi Rahnaward, “Fragile Balance,” installation view of ‘Dislocations’ at Palais de Tokyo. Photo by Quentin Chevrier. All images shared with permission
Stamped with a footprint and burned patches, Hadi Rahnaward’s matchstick rug at Palais de Tokyo frays at the edges. Titled “Fragile Balance,” the meticulously laid installation is part of the exhibition Dislocations curated in partnership Portes ouvertes sur l’art, a nonprofit supporting artists in exile.
Rahnaward works across film, photography, and installation and is interested in the cycles of violence within his native Afghanistan, particularly concerning Taliban rule. Weaving and rugmaking have long traditions with the region’s nomadic tribes, and the practice today continues both in the country and with refugees who fled during the Soviet-Afghan war. In “Fragile Balance,” innumerable matches cram together, and the combination of pristine, red heads and charred tips creates an ornate motif. Remnants of violence appear to erode such a powerful symbol of value and culture, which splinters and piles up like rubble.
Dislocations is on view through June 30, and you can follow Rahnaward on Instagram.

Photo by Quentin Chevrier

Photo courtesy of the artist

Photo courtesy of the artist

Photo by Quentin Chevrier
Do stories and artists like this matter to you? Become a Colossal Member today and support independent arts publishing for as little as $5 per month. The article Hadi Rahnaward’s Fraying Rug of Charred and Pristine Matchsticks Crumbles Under Violence appeared first on Colossal.
Michael Geist: Debating the Online Harms Act: Insights from Two Recent Panels on Bill C-63

The Online Harms Act has sparked widespread debate over the past six weeks. I’ve covered the bill in a trio of Law Bytes podcast (Online Harms, Canada Human Rights Act, Criminal Code) and participated in several panels focused on the issue. Those panels are posted below. First, a panel titled the Online Harms Act: What’s Fact and What’s Fiction, sponsored by CIJA that included Emily Laidlaw, Richard Marceau and me. It paid particular attention to the intersection between the bill and online hate.
Second, a panel titled Governing Online Harms: A Conversation on Bill C-63, sponsored by the University of Ottawa Centre for Law, Technology and Society that covered a wide range of issues and included Emily Laidlaw, Florian Martin-Bariteau, Jane Bailey, Sunil Gurmukh, and me.
The post Debating the Online Harms Act: Insights from Two Recent Panels on Bill C-63 appeared first on Michael Geist.
Ideas: The "Reconciliation" Generation: Indigenous Youth and the Future for Indigenous People
Indigenous activist Riley Yesno addresses the hopes, disappointments, accomplishments and misuses of ‘reconciliation’ in post-TRC Canada. The Anishnaabe scholar says Indigenous youth who came of age at this time are "meant to be responsible for seeing it through to its next stage."
Open Culture: Beautifully-Preserved Frescoes with Figures from the Trojan War Discovered in a Lavish Pompeii Home

Image via Pompeii Archaeological Park
Imagine visiting the home of a prominent, wealthy figure, and at the evening’s end finding yourself in a room dedicated to late-night entertaining, painted entirely black except for a few scenes from antiquity. Perhaps this wouldn’t sound entirely implausible in, say, twenty-first century Silicon Valley. But such places also existed in antiquity itself: or at least one of them did, as recently discovered in Pompeii. Preserved for nearly two millennia now by the ash of Mount Vesuvius, the ruins of that city give us the clearest and most detailed archaeological insights we have into life at the height of the Roman Empire — but even today, a third of the site has yet to be excavated.

That archaeological dig continues apace, and its latest discovery — more recent than the Pompeiian “snack bar” and “pizza” previously featured here on Open Culture — is “a spectacular banqueting room with elegant black walls, decorated with mythological characters and subjects inspired by the Trojan War,” including such mythological characters as Helen, Paris, Cassandra, and Apollo.
“It provided a refined setting for entertainment during convivial moments, whether banquets or conversations, with the clear aim of pursuing an elegant lifestyle, reflected by the size of the space, the presence of frescoes and mosaics dating to the Third Style.”

Frescoes in that Roman Third Style, explains Hyperallergic’s Rhea Nayyar, feature “small, finely painted figures and subjects that seem to float within monochromatic fields,” designed “to mimic framed works of art or altars through illusions resembling carved beams, shaded pillars, and shining candelabras — all of which were painted on flat walls.”

The color of those walls, in this case, seems to have been chosen to hide the carbon deposits left by oil lamps burning all night long. As reported by BBC Science News, the commissioner of this room, and indeed of the lavish house in which it’s located, may have been Aulus Rustius Verus, a “super-rich” local politician who — assuming decisive archaeological evidence emerges in his favor — also knew how to party.

via Hyperallergic
Related content:
A Newly-Discovered Fresco in Pompeii Reveals a Precursor to Pizza
Take a High Def, Guided Tour of Pompeii
Archaeologists Discover an Ancient Roman Snack Bar in the Ruins of Pompeii
Watch the Destruction of Pompeii by Mount Vesuvius, Re-Created with Computer Animation (79 AD)
Pompeii Rebuilt: A Tour of the Ancient City Before It Was Entombed by Mount Vesuvius
Based in Seoul, Colin Marshall writes and broadcasts on cities, language, and culture. His projects include the Substack newsletter Books on Cities, the book The Stateless City: a Walk through 21st-Century Los Angeles and the video series The City in Cinema. Follow him on Twitter at @colinmarshall or on Facebook.
Open Culture: Creating Your Own Custom AI Assistants Using OpenAI GPTs: A Free Course from Vanderbilt University

Last fall, OpenAI started letting users create custom versions of ChatGPT–ones that would let people create AI assistants to complete tasks in their personal or professional lives. In the months that followed, some users created AI apps that could generate recipes and meals. Others developed GPTs to create logos for their businesses. You get the picture.
If you’re interested in developing your own AI assistant, Vanderbilt computer science professor Jules White has released a free online course called “OpenAI GPTs: Creating Your Own Custom AI Assistants.” On average, the course should take seven hours to complete.
Here’s how he frames the course:
This cutting-edge course will guide you through the exciting journey of creating and deploying custom GPTs that cater to diverse industries and applications. Imagine having a virtual assistant that can tackle complex legal document analysis, streamline supply chain logistics, or even assist in scientific research and hypothesis generation. The possibilities are endless! Throughout the course, you’ll delve into the intricacies of building GPTs that can use your documents to answer questions, patterns to create amazing human and AI interaction, and methods for customizing the tone of your GPTs. You’ll learn how to design and implement rigorous testing scenarios to ensure your AI assistant’s accuracy, reliability, and human-like communication abilities. Prepare to be amazed as you explore real-world examples and case studies, such as:
1. GPT for Personalized Learning and Education: Craft a virtual tutor that adapts its teaching approach based on each student’s learning style, providing personalized lesson plans, interactive exercises, and real-time feedback, transforming the educational landscape.
2. Culinary GPT: Your Personal Recipe Vault and Meal Planning Maestro. Step into a world where your culinary creations come to life with the help of an AI assistant that knows your recipes like the back of its hand. The Culinary GPT is a custom-built language model designed to revolutionize your kitchen experience, serving as a personal recipe vault and meal planning and shopping maestro.
3. GPT for Travel and Business Expense Management: A GPT that can assist with all aspects of travel planning and business expense management. It could help users book flights, hotels, and transportation while adhering to company policies and budgets. Additionally, it could streamline expense reporting and reimbursement processes, ensuring compliance and accuracy.
4. GPT for Marketing and Advertising Campaign Management: Leverage the power of custom GPTs to analyze consumer data, market trends, and campaign performance, generating targeted marketing strategies, personalized messaging, and optimizing ad placement for maximum engagement and return on investment.
You can sign up for the course at no cost here. Or, alternatively, you can elect to pay $49 and receive a certificate at the end.
As a side note, Jules White (the professor) also designed another course previously featured here on OC. It focuses on prompt engineering for ChatPGPT.
Related Content
A New Course Teaches You How to Tap the Powers of ChatGPT and Put It to Work for You
Disquiet: Disquiet Junto Project 0642: Kick from Champagne

Each Thursday in the Disquiet Junto music community, a new compositional challenge is set before the group’s members, who then have five days to record and upload a track in response to the project instructions.
Membership in the Junto is open: just join and participate. (A SoundCloud account is helpful but not required.) There’s no pressure to do every project. The Junto is weekly so that you know it’s there, every Thursday through Monday, when your time and interest align.
Tracks are added to the SoundCloud playlist for the duration of the project. Additional (non-SoundCloud) tracks appear in the lllllll.co discussion thread.
These following instructions went to the group email list (via juntoletter.disquiet.com).
Disquiet Junto Project 0642: Kick from Champagne
The Assignment: Use carbonation to make a beat.
Step 1: Make kick drums from the sound of something carbonated.
Step 2: Make a rhythmic track (think techno, but certainly follow your own muse) using the result of Step 1.
Thanks to the folks in the Echo Chamber Slack whose discussion about techno and kicks informed this week’s project.
Tasks Upon Completion:
Label: Include “disquiet0642” (no spaces/quotes) in the name of your track.
Upload: Post your track to a public account (SoundCloud preferred but by no means required). It’s best to focus on one track, but if you post more than one, clarify which is the “main” rendition.
Share: Post your track and a description/explanation at https://llllllll.co/t/disquiet-junto-project-0642-kick-from-champagne/
Discuss: Listen to and comment on the other tracks.
Additional Details:
Length: The length is up to you.
Deadline: Monday, April 22, 2024, 11:59pm (that is: just before midnight) wherever you are.
About: https://disquiet.com/junto/
Newsletter: https://juntoletter.disquiet.com/
License: It’s preferred (but not required) to set your track as downloadable and allowing for attributed remixing (i.e., an attribution Creative Commons license).
Please Include When Posting Your Track:
More on the 642nd weekly Disquiet Junto project, Kick from Champagne — The Assignment: Use carbonation to make a beat — at https://disquiet.com/0642/
Schneier on Security: Other Attempts to Take Over Open Source Projects
After the XZ Utils discovery, people have been examining other open-source projects. Surprising no one, the incident is not unique:
The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different names and overlapping GitHub-associated emails. These emails implored OpenJS to take action to update one of its popular JavaScript projects to “address any critical vulnerabilities,” yet cited no specifics. The email author(s) wanted OpenJS to designate them as a new maintainer of the project despite having little prior involvement. This approach bears strong resemblance to the manner in which “Jia Tan” positioned themselves in the XZ/liblzma backdoor.
[…]
The OpenJS team also recognized a similar suspicious pattern in two other popular JavaScript projects not hosted by its Foundation, and immediately flagged the potential security concerns to respective OpenJS leaders, and the Cybersecurity and Infrastructure Security Agency (CISA) within the United States Department of Homeland Security (DHS).
The article includes a list of suspicious patterns, and another list of security best practices.
Planet Haskell: Tweag I/O: Cloud Native Computing in 2024—feeling the pulse at Kubecon
Last year, at the end of winter, we wrote our impressions of the trends and evolution of infrastructure and configuration management after attending FOSDEM and CfgMgmtCamp. We’re at it again, but with Kubecon this year, the biggest cloud native computing conference.
If you’ve never heard of cloud native computing before, it has a number of definitions online, but the simplest one is that it’s mostly about Kubernetes.
Kubecon is a huge event with thousands of attendees. The conference spanned several levels of the main convention center in Paris, with a myriad of conference rooms and a whole floor for sponsor booths. FOSDEM already felt huge compared to academic conferences, but Kubecon is even bigger.
Although the program was filled with appealing talks, we ended up spending most of our time chatting with people and visiting booths, something you can’t do as easily online.
Nix for the win
The very first morning, as we were walking around and waiting for the caffeine to kick in, we immediately spotted a Nix logo on someone’s sweatshirt. No better way to start the day than to meet with fellow Nix users!
And Nix was in general a great entry point for conversations at this year’s Kubecon. We expected it to still be an outsider at an event about container-driven technology, but the problems that “containers as a default packaging unit” can’t solve were so present that Nix’s value proposition is attuned to what everyone had on their minds anyway. In other words, Nix is now known enough as to serve as a conversation starter: the company might not use it, but many people have heard about it and were very interested to hear insights from big contributors like Tweag, the Modus Create OSPO.
Cybersecurity
Many security products were represented. Securing cloud-native applications is indeed a difficult matter, as their many layers and components expose a large attack surface.
For one, the schedule included a security track, with a fair share of talks being about SBOMs tying back into the problem of containers that ship an opaque content without inventory. Nix, as a solution to this problem, was a great conversation starter here as well, especially for fellow Nixer Matthias, who can talk for hours about how Nix is the best (and maybe only) technology for automatically deriving complete SBOMs of a piece of software, in a trustworthy manner. Our own NLNet-funded project genealogos, which does exactly that, is recently getting a lot of interest.
Besides the application code and what goes in it, another focus was avoiding misconfiguration of the cloud infrastructure layer, of the Kubernetes cluster, and anything else going into container images. Many companies propose SaaS combinations of static linters scanning the configuration files directly with various policy rules, heuristics and dynamic monitoring of secure cloud native applications. Our configuration language Nickel was very relevant here: one of its raisons d’être is to provide efficient tools (types, contracts and a powerful LSP) to detect and fix misconfigurations as early as possible. We had cool conversations around writing custom security policies as Nickel contracts with the new LSP background contract checking (introduced in 1.5) reporting non-compliance live in the editor — in that light, contracts are basically a lightweight way to program an LSP.
Internal Developer Platforms (IDPs)
IDPs were a hot topic at Kubecon. Tweag’s mission, as the OSPO of a leading software development consultancy, is to improve developer experience across the software lifecycle, which makes IDPs a natural topic for us.
An IDP is a platform - usually a web interface in practice - which glues several developer tools and services together and acts as the central entry point for most developer workflows. It’s centered around the idea of self-service, not unlike the console of cloud providers, but configurable for your exact use case and open to integrate tools across ecosystem boundaries. We already emphasized this emerging new abstraction in last year’s post. Example use cases are routinely deploying new infrastructure with just a few clicks, rather than requiring to sync and to send messages back-and-forth to the DevOps team. IDPs don’t replace other tools but offer a unified interface, usually with customized presets, to interact with repositories, internal data and infrastructure.
Backstage, an open-source IDP developed by Spotify, had its own sub-conference at Kubecon. Several products are built on top of it as well: it’s not really a ready-to-use solution but rather the engine to build a custom IDP for your company, which leaves room for turnkey offers. We feel that such integrated, centralized and simple-to-use services may become a standard in the future: think of how much GitHub (or an equivalent) is a central part of our modern workflow, but also of how many things it frustratingly can’t do (in particular infrastructure).
Cloud & AI
Many Kubernetes-based MLOps companies propose services to make it easy to deploy and manage scalable AI models in the cloud.
In the other direction, with the advent of generative AI, there was no doubt that we would see AI-based products to ease the automation of infrastructure-related tasks. We attended a demo of a multi-agent system which integrates with e.g. Slack, where you can ask a bot to perform end-to-end tasks (which includes interacting with several systems, like deploying something to the cloud, editing a Jira ticket and pushing something to a GitHub repo) or ask high-level questions, such as “which AWS users don’t have MFA enabled”.
It’s hard to tell from a demo how solid this would be in a real production system. I also don’t know if I would trust an AI agent to perform tasks without proper validation from a human (though there is a mode where confirmation is required before applying changes). There are also security concerns around having those agents run somewhere with write access to your infrastructure.
Putting those important questions aside, the demo was still quite impressive. It makes sense to automate those small boring tasks which usually require you to manually interact with several different platforms and are often quite mechanical indeed.
OSPO
We attended a Birds-of-a-Feather session on Open Source Program Offices (OSPO). While the small number of participants was a bit disappointing (between 10 and 15, compared to the size of the conference), the small group discussions were still engrossing, and we were pleased to meet people from other OSPOs as well as engineers wanting to push for an OSPO in their own company.
The generally small size OSPOs (including from very large and influential tech companies) and their low maturity from a strategic point of view was surprising to us. Many OSPOs seem to be stuck in tactical concerns, managing license and IP issues that can occur when developers open up company-owned repos. In such a situation, all OSPO members are fully occupied by the large number of requests they get. But the most interesting questions: how to share benefits and costs by working efficiently with open source communities, how to provide strategic guidance and support, and how to gain visibility in communities of interest were only addressed by few. A general concern seemed to be generally a lack of understanding by upper management about the real strategic power that an OSPO can provide. From that perspective, Tweag, although a pink unicorn as a consulting OSPO, is quite far on the maturity curve with concrete strategical and technical firepower through technical groups, and our open-source portfolio (plus the projects that we contribute to but aren’t ours).
Concluding words
Kubecon was a great experience, and we’re looking forward to the next one. We are excited about the advent of Internal Developer Platforms and the concept of self-serving infrastructure, which are important aspects of developer experience.
On the technological side, the cloud-native world seems to be dominated by Kubernetes with Helm charts and YAML, and Docker, while the technologies we believe in and are actively developing are still outsiders in the space (of course they aren’t a full replacement for what currently exists, but they could fill many gaps). I’m thinking in particular about Nix (and more generally about declarative, hermetic and reproducible builds and deployments) and Nickel (better configuration languages and management tools). But, conversation after conversation, conference after conference, we’re seeing more and more interests in new paradigms, sometimes because those technologies are best equipped - by far - to solve problems that are on everyone’s radar (e.g. software traceability through SBOMs with Nix) thanks to their different approach.
Planet Haskell: Oleg Grenrus: What makes a good compiler warning?
Recently I came up with a criteria for a good warning to have in a compiler:
If compiler makes a choice, or has to deal with some complication, it may well tell about that.
That made me think about warnings I implemented into GHC over the years. They are fine.
Let us first understand the criteria better. It is better explained by an example which triggers few warnings:
First warning is -Wname-shadowing:
Shadow.hs:3:11: warning: [-Wname-shadowing]
This binding for ‘x’ shadows the existing binding
bound at Shadow.hs:2:11
|
3 | let x = 'y' in x
| ^When resolving names (i.e. figuring out what textual identifiers refer to) compilers have a choice what to do with duplicate names. The usual choice is to pick the closest reference, shadowing others. But it's not the only choice, and not the only choice GHC does in similar-ish situations. e.g. module's top-level definition do not shadow imports; instead an ambiguous name error is reported. Also \ x x -> x is rejected (treated as a non-linear pattern), but \x -> \x -> x is accepted (two separate patterns, inner one shadows). So, in a way, -Wname-shadowing reminds us what GHC does.
Another warning in the example is -Wunused-binds:
Shadow.hs:2:11: warning: [-Wunused-local-binds]
Defined but not used: ‘x’
|
2 | foo = let x = 'x' in
| ^This a kind of warning that compiler might figure out in the optimisation passes (I'm not sure if GHC always tracks usage, but IIRC GCC had some warnings triggered only when optimisations are on). When doing usage analysis, compiler may figure out that some bindings are unused, so it doesn't need to generate code for them. At the same time it may warn the user.
More examples
Let go through few of the numerous warnings GHC can emit.
-Woverflowed-literals causes a warning to be emitted if a literal will overflow. It's not strictly a compiler choice, but a choice nevertheless in base's fromInteger implementations. For most types 1 the fromInteger is a total function with rollover behavior: 300 :: Word8 is 44 :: Word8. It could been chosen to not be total too, and IMO that would been ok if fromInteger were used only for desugaring literals.
-Wderiving-defaults: Causes a warning when both DeriveAnyClass and GeneralizedNewtypeDeriving are enabled and no explicit deriving strategy is in use. This a great example of a choice compiler makes. I actually don't remember which method GHC picks then, so it's good that compiler reminds us that it is good idea to be explicit (using DerivingStrategies).
-Wincomplete-patterns warns about places where a pattern-match might fail at runtime. This a complication compiler has to deal with. Compiler needs to generate some code to make all pattern matches complete. An easy way would been to always implicitly default cases to all pattern matches, but that would have performance implications, so GHC checks pattern-match coverage, and as a side-product may report incomplete pattern matches (or -Winaccesible-code) 2.
-Wmissing-fields warns you whenever the construction of a labelled field constructor isn’t complete, missing initialisers for one or more fields. Here compiler needs to fill the missing fields with something, so it warns when it does.
-Worphans gets an honorary mention. Orphans cause so much incidental complexity inside the compiler, that I'd argue that -Worphans should be enabled by default (and not only in -Wall).
Bad warnings
-Wmissing-import-lists warns if you use an unqualified import declaration that does not explicitly list the entities brought into scope. I don't think that there are any complications or choices compiler needs to deal with, therefore I think this warning should been left for style checkers. (I very rarely have import lists for modules from the same package or even project; and this is mostly a style&convenience choice).
-Wprepositive-qualified-module is even more of an arbitrary style check. With -Wmissing-import-lists it is generally accepted that explicit import lists are better for compatibility (and for GHCs recompilation avoidance). Whether you place qualified before or after the module name is a style choice. I think this warning shouldn't exist in GHC. (For the opposite you'd need a style checker to warn if ImportQualifiedPost is enabled anywhere).
Note, while -Wtabs is also mostly a style issue, but the compiler has to make a choice how to deal with them. Whether to always convert tabs to 8 spaces, convert to next 8 spaces boundary, require indentation to be exactly the same spaces&tabs combination. All choices are sane (and I don't know which one GHC makes), so a warning to avoid tabs is justified.
Compatibility warnings
Compatibility warnings are usually good also according to my criteria. Often it is the case that there is an old and a new way of doing things. Old way is going to be removed, but before removing it, it is deprecated.
-Wsemigroup warned about Monoid instances without Semigroup instances. (A warning which you shouldn't be able to trigger with recent GHCs). Here we could not switch to new hierarchy immediately without breaking some code, but we could check whether the preconditions are met for awhile.
-Wtype-equality-out-of-scope is somewhat similar. For now, there is some compatibility code in GHC, and GHC warns when that fallback code path is triggered.
My warnings
One of the warning I added is -Wmissing-kind-signatures. For long time GHC didn't have a way to specify kind signatures until StandaloneKindSignatures were added in GHC-8.10. Without kind signatures GHC must infer kind of a data type or type family declaration. With kind signature it could just check against given kind (which is a technically a lot easier). So while the warning isn't actually implemented so, it could be triggered when GHC notices it needs to infer a kind of a definition. In the implementation the warning is raised after the type-checking phase, so the warning can include the inferred kind. However, we can argue that when inference fails, GHC could also mention that the kind signature was missing. Adding a kind signature often results in better kind errors (c.f. adding a type signature often results in a better type error when something is wrong).
The -Wmissing-poly-kind-signatures warning seems like a simple restriction of above, but it's not exactly true. There is another problem GHC deals with. When GHC infers a kind, there might be unsolved meta-kind variables left, and GHC has to do something to them. With PolyKinds extension on, GHC generalises the kind. For example when inferring a kind of Proxy as in
GHC infers that the kind is k -> Type for some k and with PolyKinds it generalises it to type Proxy :: forall {k}. k -> Type. Another option, which GHC also may do (and does when PolyKinds are not enabled) is to default kinds to Type, i.e. type Proxy :: Type -> Type. There is no warning for kind defaulting, but arguable there should be as defaulted kinds may be wrong. (Haskell98 and Haskell2010 don't have a way to specify kind signatures; that is clear design deficiency; which was first resolved by KindSignatures and finally more elegantly by StandaloneKindSignatures).
There is defaulting for type variables, and (in some cases) GHC warns about them. You probably have seen Defaulting the type variable ‘a0’ to type ‘Integer’ warnings caused by -Wtype-defaults. Adding -Wkind-defaults to GHC makes sense, even only for uniformity between (types of) terms and types; or arguably nowadays it is a sign that you should consider enabling PolyKinds in that module.
About errors
The warning criteria also made me think about the following: the error hints are by necessity imprecise. If compiler knew exactly how to fix an issue, maybe it should just fix it and instead only raise a warning.
GHC has few of such errors. For example when using a syntax guarded by an extension. It can be argued (and IIRC was recently argued in discussions around GHC language editions) that another design approach would be simply accept new syntax, but just warn about it. The current design approach where extensions are "feature flags" providing some forward and backward compatibility is also defendable.
Conversely, if there is a case where compiler kind-of-knows what the issue is, but the language is not powerful enough for compiler to fix the problem on its own, the only solution is to raise an error. Well, there is another: (find a way to) extend the language to be more expressive, so compiler could deal with the currently erroneous case. Easier said than done, but in my opinion worth trying.
An example of above would be -Wmissing-binds . Currently writing a type signature without a corresponding binding is a hard error. But compiler could as well fill it in with a dummy one, That would complement -Wmissing-methods and -Wmissing-fields. Similarly for types, a standalone kind signature tells the compiler already a lot about the type even without an actual definition: the rest of the module can treat it as an opaque type.
Another example is briefly mentioned making module-top-level definitions shadow imports. That would make adding new exports (e.g. to implicitly imported Prelude) less affecting. While we are on topic of names, GHC could also report early when imported modules have ambiguous definitions, e.g.
doesn't trigger any warnings. But if you try to use Lazy.unpack you get an ambiguous occurrence error. GHC already deals with the complications of ambiguous names, it could as well have an option to report them early.
Conclusion
If compiler makes a choice, or has to deal with some complication, it may well tell about that.
Seems like a good criteria for a good compiler warning. As far as I can tell most warnings in GHC pass it; but I found few "bad" ones too. And also identified at least one warning-worthy case GHC doesn't warn about.
With
-XNegativeLiteralsandNatural,fromIntegermay result in run-time error though, for example:↩︎<interactive>:6:1: warning: [-Woverflowed-literals] Literal -1000 is negative but Natural only supports positive numbers *** Exception: arithmetic underflowUsing [
-fmax-pmcheck-models] we could almost turn off GHCs pattern-match coverage checker, which will make GHC consider (almost) all pattern matches as incomplete. So-Wincomplete-patternsis kind of an example of a warning which is powered by an "optional" analysis is GHC.↩︎
Penny Arcade: The Right Hand of The King
With people talking about Fallout now that would never have previously talked about Fallout, it's a great time to direct you to Bethesda's Vault 77 Page, which catalogs the origins of the entity known in the wasteland as The Puppet Man. There's also a lot of other text on the page, what your fifth grade teacher Mrs. Prang might have called a "primary source," which serves to situate the entire affair in that place and time. Bethesda was fully down to clown; it's a canonical vault, with item and holotape support. Seemed like it might be fun to go back.
Colossal: Transforming Fabric into Flesh, Tamara Kostianovsky Fuses Cruelty and Beauty

All images © RX & Slag, shared with permission
If you walked into an exhibition featuring work from Tamara Kostianovsky in recent years, you likely encountered life-sized carcasses dangling from meat hooks. The Argentine-American artist (previously) is perhaps best known for these carnal sculptures of bone and flesh made from patterned fabric scraps. Newer additions include botanical vines winding through ribs and tropical birds perched inside that vacillate between beauty and brutality.
“I see these works in terms of metamorphosis,” Kostianovsky says. “The idea is to transform the image of the carcass from a place of carnage into a matrix where life takes root—in the manner of a utopian environment.”
Some of the carcasses will be on view starting April 23 at the Museum of Hunting and Nature in Paris for The Flesh of the World, Kostianovsky’s latest solo exhibition. Featuring about 30 works including multi-colored tree stumps and wall-based panels, the show brings forth the artist’s enduring fascination with the entangled relationship between bodies and the environment.

Stitching recycled clothing and various textiles into patterns that resemble marbled muscle, skin, and other tissues, she asks viewers to consider their consumption habits and the cyclical nature of life and death. By contrasting such soft, domestic materials with the grotesque qualities of the animal body, the subtle cruelties of slaughter and gluttony many partake in daily become more visceral.
Much of Kostianovsky’s works also address the impacts of colonialism and violence, particularly in her recent Carnal Geographies series. Layering maps, foliage, and patchwork, she visualizes North and South America and Africa, delineating the outer continental borders with flesh-like parts. Dotted with colorful birds, the works confront the historical and continued brutality waged in these places and the potential for new growth and life in a post-colonial world.
See The Flesh of the World through November 3. The artist also has work in two group exhibitions, one on view through April 27 at Chart Gallery in New York City and the other through June 2 at the Whyte Museum of the Canadian Rockies in Banff. You can also peruse an archive of her work on her site and Instagram.







Do stories and artists like this matter to you? Become a Colossal Member today and support independent arts publishing for as little as $5 per month. The article Transforming Fabric into Flesh, Tamara Kostianovsky Fuses Cruelty and Beauty appeared first on Colossal.
Greater Fool – Authored by Garth Turner – The Troubled Future of Real Estate: The big lie
Yesterday the feds said their budget is generationally fair.
And, yup, it is. Fair to the wrinklies. After all, we old farts get enhanced OAS, more free drugs and the benefit of oodles of government spending we’ll never have to pay for. Once again – and more than ever – the Libs have kicked the can down the road. Spending surges. The debt swells historically. Interest charges jump to record levels. Deficits become structural. And nowhere in sight is the day when revenues match expenditures. No balanced budget. Taxes can only increase. The Boomers win again. Do their kids even know what’s coming for them (and their kids)?
What a political, cynical, manipulative, opportunistic thing the PM and his finance minister unleashed. After almost a decade in office, and after having already doubled the country’s debt, they’re buying voters with billions in new spending that will cost hundreds of billions to finance.
The budget is inflationary, adding a ton of fiscal stimulus that might cancel out yesterday’s rosy inflation number. It ensures the tax load will increase more. And if sunny economic projections aren’t met, Canada could have a debt-deficit crisis on its hands when federal borrowing goes nuts, bond yields pop and you will pine for the good old days when houses only cost $1.5 million.
Yikes. Look at what Chrystia Freeland says we’ll be paying to service the existing steamy pile of debt. About $65 billion a year within sixty months. That will be the biggest single taxpayer expense – more than we dump into health care. And this is the best-case scenario.
Our economist pal Derek Holt has this right: “Trudeau and Freeland are ripping off Canada’s youth who will be the ones left to face the bills for many years to come. It’s an insult to portray such a Budget as being in the best interests of Canada’s youth who have fled from the Liberals in droves.”
To deceive the kids, the Libs are telling them to look away from the economy and instead to focus on real estate. Thiry-year mortgages, enhanced RRSP downpayment loans, billions for construction, mortgage and renter’s charters, the first-home tax shelter and no tax on property profits. However, as we all know, it ain’t working. House prices have not dropped appreciably. Mortgage rates are a struggle. The pace of construction has faltered. So building three million new homes in the coming years is fiction.
Meanwhile the coalition government is doing what leftists love. Portraying society as a class struggle between Us and Them, then punishing the most successful and productive among us.
So Ottawa plans on Hoovering about $20 billion in seriously higher capital gains taxes, levied on individuals plus all businesses and trusts. This will affect only the wealthy, they say. But also caught in the web will be those selling investment or secondary properties, long-held cottages or cabins, facing real estate inheritances, dumping rental condos because of onerous regs or families now facing taxable trusts.
Besides, didn’t the Bank of Canada say the other day Canada has a productivity emergency? Our economy has been too obsessed with residential real estate and not feeding economic growth, tech development and entrepreneurs with investment capital. It’s a dangerous thing. We’re falling behind, blinded by selling houses to each other.
And what does the government do?
It raises taxes on investment capital and keeps real estate gains tax-free. Duh. Investors funding corporations, start-ups, businesses that make stuff, invent things, compete and employ workers will think twice about having two-thirds of their profits taxed at a 54% marginal rate – when they can buy an opulent, lavish principal residence and pay nothing on gains when they sell.
Lost on the Libs is the fact that ‘wealthy’ investors hand over half their incomes in taxes, then use the savings that remain to fund companies that pay taxes, and will now be taxed far more heavily on gains when they sell. In other words, why would you do it? Why not buy residential real estate? Or move your capital? Or just leave?
We’re increasing taxes and jeopardizing the country so the government can increase spending for political advantage while pushing the greatest burden upon future taxpayers. Then lying about it.
Oh, and here’s one more thing to fret about.
Some years ago when the Liberals began collecting data on residential real estate transactions, saying it was to spank foreign buyers, this blog warned of a darker reality. Now Derek Holt, chief economist of one of our major banks, in light of Ottawa’s fiscal folly, is voicing it.
“I still worry about how the Trudeau Government began collecting data on home sales with your tax filings starting years ago. They are establishing the infrastructure to maximize future policy flexibility toward the tax treatment of home equity. Would this government, for instance, tax home equity gains on primary residences held by relatively wealthy folks? I wouldn’t trust them.”
So, it’s a new day in our nation. We whack the productive. We punish success. We borrow from the future. We promise the impossible. We feed the house lust. We ignore the threat. We pander for political gain.
This may not end well.
About the picture: “Regular photo contributor and avid reader of your educational and entertaining blog,” writes Robin, on Vancouver Island. “Never miss a daily dose, even during my recent travels to the jungles of Borneo, where I took this pic of this orangutan. Feel free to use the ape photo, if you want to change it up a bit from canines and felines. Thanks for all your free advice and wit.”
To be in touch or send a picture of your beast, email to ‘garth@garth.ca’.
Colossal: Cyrus Kabiru Fashions Elaborate Mixed-Media Masks and Goggles from Found Objects

All images © Cyrus Kabiru, shared with permission
Ranging from mechanical parts and cooking utensils to plastic caps and beads, Kenyan artist Cyrus Kabiru fashions dazzling eyewear and helmets from salvaged and found objects. The futuristic forms often obscure the eyes like an ornamental veil, and motorbike helmets provide a fitting canvas for fins and frills.
Kabiru (previously) originally began making innovative glasses after being denied a pair when he was young. The variety of materials the artist found around his hometown of Nairobi inspired him to create playful versions, bringing joy to those around him. Over time, his creations have grown and become more elaborate, hinting at mysterious technological functions.
Kabiru has recently begun larger standalone sculptures, and you can explore more of his work on Instagram.






Do stories and artists like this matter to you? Become a Colossal Member today and support independent arts publishing for as little as $5 per month. The article Cyrus Kabiru Fashions Elaborate Mixed-Media Masks and Goggles from Found Objects appeared first on Colossal.
Disquiet: More Memory Module Music
Two days ago I posted a preview video I recorded of some virtual synthesizer modules being developed by my friend Mahlen Morris, who does so under the name Stochastic Telegraph. What appears here is a video that Mahlen himself recorded, earlier in the development process, when some of the modules had different names, and at least one of them had fewer features. You can read along in the video as he describes, by typing, what it is that he’s up to in real time. The source audio that he’s working with here is a guitar part that I recorded for him with this delay/buffer approach in mind.
Saturday Morning Breakfast Cereal: Saturday Morning Breakfast Cereal - Nice

Click here to go see the bonus panel!
Hovertext:
Absolute Midden is copyright SMBC Enterprises 2024 all rights reserved.
Today's News:
BOOOOOOOM! – CREATE * INSPIRE * COMMUNITY * ART * DESIGN * MUSIC * FILM * PHOTO * PROJECTS: “Cobalt Blues” by Artist Karen Ösp Pálsdóttir
Artist Bio:Karen Ösp Pálsdóttir (b.1992) received her BFA from the Maryland Institute College of Art (MICA) in 2013. Her paintings have been exhibited in galleries in New York, Baltimore, Washington DC, Boston, Reykjavík, London, Barcelona, and Paris. Karen’s paintings have been featured in various publications such as New American Paintings, Create! Magazine, Tibia Magazine, SFMOMA, Hyperallergic, and El País. Pálsdóttir´s work explores various subjects through a Cobalt Blue lens in her most recent monochromatic oil paintings.
Statement: Inspired by the delicate interplay of elasticity and depth, Karen’s work explores the nuanced language of cobalt blue. Through the range of cobalt blue’s dark, velvety hues and soft zeniths, each composition becomes part of a larger exploration of temporality and impermanence. This “modern, Improved Blue” becomes a tactile experience in monochromatic simplicity and invites the viewer to peer through a singular lens, akin to an optical filter. The Blue Star Fern, a reoccurring collaborator, often emerges as a fusion of transparency and distortion. It stands as a quiet observer of the evolving lucidity of the human condition and the dance between what is and what might be.








Ideas: The history of bombing civilians — and why it’s still a military tactic
The bombing of civilians has been called one of the "great scandals" of modern warfare. So why, despite nearly a century of drafting laws and signing conventions protecting the sanctity of human life, does bombing civilians remain a widespread military tactic?
Planet Haskell: Haskell Interlude: 47: Avi Press
Avi Press is interviewed by Joachim Breitner and Andres Löh. Avi is the founder of Scarf, which uses Haskell to analyze how open source software is used. We’ll hear about the kind of shitstorm telemetry can cause, when correctness matters less than fearless refactoring and how that can lead to statically typed Stockholm syndrome.
Open Culture: An Archive of Vividly Illustrated Japanese Schoolbooks, from the 1800s to World War II

If you want to appreciate Japanese books, it helps to be able to read Japanese books. It helps, but it’s not 100 percent necessary: even if you’ve never learned a single kanji character, you’ve probably marveled at one time or another at the aesthetics of Japan’s print culture. Maybe you’ve even done so here at Open Culture, where we’ve previously featured archives of Japanese books going back to the seventeenth century, a collection of Japanese wave and ripple designs from 1980, a Japanese edition of Aesop’s Fables from 1925, and even a fantastical history of America from 1861 — all of which display a heightened design sensibility not as easily found in other lands.

The same even holds true for Japanese schoolbooks and other educational materials, a digital archive of which you can explore on the web site of Japan’s National Institute for Educational Policy Research. “Ranging from brush painting guides to elementary readers to the geography of Koshi Province — now the Hokuriku region — hundreds of digital scans reveal what students were learning in school more than 100 years ago,” writes Colossal’s Kate Mothes.
Certain publications, like the epistolary 冨士野往来 (“Mount Fuji Comings and Goings”) from 1674, date back much further. But only a couple of centuries later did Japanese books start integrating the colorful artwork that still looks so vivid to us today. You’ll find particularly rich examples of such books in the sections of the archive dedicated to educational pictures, wall charts, and sugoroku, a kind of traditional board game.
Originally produced, for the most part, in the mid-to-late nineteenth century (though with some items as recent as the time of World War II), these provide a look at the worldview that Japan presented to its young students during a period when, not long emerged from more than 200 years of deliberate isolation, the country was taking in foreign influence — and especially Western influence — at a breakneck pace.

But despite a variety of proposed dramatic language reforms (which would later include the wholesale adoption of English), Japan would continue almost exclusively to speak and read Japanese. If you’re interested in learning it yourself, the reading materials in this archive will surely work as well for you as they did for the students of the eighteen-nineties. And even if you’re not, they’re still timeless object lessons in educational illustration and design. Enter the collection here.

via Colossal/Present & Correct
Related content:
Download Classic Japanese Wave and Ripple Designs: A Go-to Guide for Japanese Artists from 1903
Based in Seoul, Colin Marshall writes and broadcasts on cities, language, and culture. His projects include the Substack newsletter Books on Cities, the book The Stateless City: a Walk through 21st-Century Los Angeles and the video series The City in Cinema. Follow him on Twitter at @colinmarshall or on Facebook.
Penny Arcade: The Right Hand of The King
Disquiet: … Day … Groundhog Day … Groundhog …
I wrote about one of my favorite movies of all time for hilobrow.com, as part of a series of 25 pieces on “the topic of ‘offbeat’ movies from the Eighties” (the decade loosely defined). Here’s how it opens:
In 1993, the year Groundhog Day hit theaters, that furry near-term Nostradamus named Punxsutawney Phil gazed into the meteorological future and saw his shadow.
Historical records of this Americana hokum date back to the late 1800s, when Groundhog Day first became an annual ritual at Gobbler’s Knob, an inland Pennsylvania town with the sort of Capraesque name that lends itself to fables mixing homespun moralizing, commercial appeal, and a smidgen of self-awareness.
Groundhog Day legend has it that if Phil sees his shadow, winter will last another six weeks. What Phil — and Phil’s handlers, and the makers of the film Groundhog Day — certainly didn’t see coming was that 1993’s elongated winter wouldn’t hold a candle to the staying power of the movie itself.
On the one hand, this may seem off-topic for me — it even did to me, for a moment. I thought about adding a tag to Disquiet.com for “off-topic” things that I may post occasionally, but then I realized that part of the crux of my description of the movie is as follows: “It’s It’s a Wonderful Life reworked for memories trained on instant replay.” Which isn’t just on-topic; it connects directly to what I wrote about just yesterday, about music-making tools that let one access the recent past through memory buffers.
Other pieces in the Hilobrow series include Annie Nocenti on After Hours, Erik Davis on Repo Man, Susannah Breslin on Man Bites Dog, Dean Haspiel on Sid and Nancy, and Carlo Rotella on Robocop. Several are already up, and others will appear in the coming weeks.
Schneier on Security: Smuggling Gold by Disguising it as Machine Parts
Someone got caught trying to smuggle 322 pounds of gold (that’s about a quarter of a cubic foot) out of Hong Kong. It was disguised as machine parts:
On March 27, customs officials x-rayed two air compressors and discovered that they contained gold that had been “concealed in the integral parts” of the compressors. Those gold parts had also been painted silver to match the other components in an attempt to throw customs off the trail.
Schneier on Security: Backdoor in XZ Utils That Almost Happened
Last week, the Internet dodged a major nation-state attack that would have had catastrophic cybersecurity repercussions worldwide. It’s a catastrophe that didn’t happen, so it won’t get much attention—but it should. There’s an important moral to the story of the attack and its discovery: The security of the global Internet depends on countless obscure pieces of software written and maintained by even more obscure unpaid, distractible, and sometimes vulnerable volunteers. It’s an untenable situation, and one that is being exploited by malicious actors. Yet precious little is being done to remedy it.
Programmers dislike doing extra work. If they can find already-written code that does what they want, they’re going to use it rather than recreate the functionality. These code repositories, called libraries, are hosted on sites like GitHub. There are libraries for everything: displaying objects in 3D, spell-checking, performing complex mathematics, managing an e-commerce shopping cart, moving files around the Internet—everything. Libraries are essential to modern programming; they’re the building blocks of complex software. The modularity they provide makes software projects tractable. Everything you use contains dozens of these libraries: some commercial, some open source and freely available. They are essential to the functionality of the finished software. And to its security.
You’ve likely never heard of an open-source library called XZ Utils, but it’s on hundreds of millions of computers. It’s probably on yours. It’s certainly in whatever corporate or organizational network you use. It’s a freely available library that does data compression. It’s important, in the same way that hundreds of other similar obscure libraries are important.
Many open-source libraries, like XZ Utils, are maintained by volunteers. In the case of XZ Utils, it’s one person, named Lasse Collin. He has been in charge of XZ Utils since he wrote it in 2009. And, at least in 2022, he’s had some “longterm mental health issues.” (To be clear, he is not to blame in this story. This is a systems problem.)
Beginning in at least 2021, Collin was personally targeted. We don’t know by whom, but we have account names: Jia Tan, Jigar Kumar, Dennis Ens. They’re not real names. They pressured Collin to transfer control over XZ Utils. In early 2023, they succeeded. Tan spent the year slowly incorporating a backdoor into XZ Utils: disabling systems that might discover his actions, laying the groundwork, and finally adding the complete backdoor earlier this year. On March 25, Hans Jansen—another fake name—tried to push the various Unix systems to upgrade to the new version of XZ Utils.
And everyone was poised to do so. It’s a routine update. In the span of a few weeks, it would have been part of both Debian and Red Hat Linux, which run on the vast majority of servers on the Internet. But on March 29, another unpaid volunteer, Andres Freund—a real person who works for Microsoft but who was doing this in his spare time—noticed something weird about how much processing the new version of XZ Utils was doing. It’s the sort of thing that could be easily overlooked, and even more easily ignored. But for whatever reason, Freund tracked down the weirdness and discovered the backdoor.
It’s a masterful piece of work. It affects the SSH remote login protocol, basically by adding a hidden piece of functionality that requires a specific key to enable. Someone with that key can use the backdoored SSH to upload and execute an arbitrary piece of code on the target machine. SSH runs as root, so that code could have done anything. Let your imagination run wild.
This isn’t something a hacker just whips up. This backdoor is the result of a years-long engineering effort. The ways the code evades detection in source form, how it lies dormant and undetectable until activated, and its immense power and flexibility give credence to the widely held assumption that a major nation-state is behind this.
If it hadn’t been discovered, it probably would have eventually ended up on every computer and server on the Internet. Though it’s unclear whether the backdoor would have affected Windows and macOS, it would have worked on Linux. Remember in 2020, when Russia planted a backdoor into SolarWinds that affected 14,000 networks? That seemed like a lot, but this would have been orders of magnitude more damaging. And again, the catastrophe was averted only because a volunteer stumbled on it. And it was possible in the first place only because the first unpaid volunteer, someone who turned out to be a national security single point of failure, was personally targeted and exploited by a foreign actor.
This is no way to run critical national infrastructure. And yet, here we are. This was an attack on our software supply chain. This attack subverted software dependencies. The SolarWinds attack targeted the update process. Other attacks target system design, development, and deployment. Such attacks are becoming increasingly common and effective, and also are increasingly the weapon of choice of nation-states.
It’s impossible to count how many of these single points of failure are in our computer systems. And there’s no way to know how many of the unpaid and unappreciated maintainers of critical software libraries are vulnerable to pressure. (Again, don’t blame them. Blame the industry that is happy to exploit their unpaid labor.) Or how many more have accidentally created exploitable vulnerabilities. How many other coercion attempts are ongoing? A dozen? A hundred? It seems impossible that the XZ Utils operation was a unique instance.
Solutions are hard. Banning open source won’t work; it’s precisely because XZ Utils is open source that an engineer discovered the problem in time. Banning software libraries won’t work, either; modern software can’t function without them. For years, security engineers have been pushing something called a “software bill of materials”: an ingredients list of sorts so that when one of these packages is compromised, network owners at least know if they’re vulnerable. The industry hates this idea and has been fighting it for years, but perhaps the tide is turning.
The fundamental problem is that tech companies dislike spending extra money even more than programmers dislike doing extra work. If there’s free software out there, they are going to use it—and they’re not going to do much in-house security testing. Easier software development equals lower costs equals more profits. The market economy rewards this sort of insecurity.
We need some sustainable ways to fund open-source projects that become de facto critical infrastructure. Public shaming can help here. The Open Source Security Foundation (OSSF), founded in 2022 after another critical vulnerability in an open-source library—Log4j—was discovered, addresses this problem. The big tech companies pledged $30 million in funding after the critical Log4j supply chain vulnerability, but they never delivered. And they are still happy to make use of all this free labor and free resources, as a recent Microsoft anecdote indicates. The companies benefiting from these freely available libraries need to actually step up, and the government can force them to.
There’s a lot of tech that could be applied to this problem, if corporations were willing to spend the money. Liabilities will help. The Cybersecurity and Infrastructure Security Agency’s (CISA’s) “secure by design” initiative will help, and CISA is finally partnering with OSSF on this problem. Certainly the security of these libraries needs to be part of any broad government cybersecurity initiative.
We got extraordinarily lucky this time, but maybe we can learn from the catastrophe that didn’t happen. Like the power grid, communications network, and transportation systems, the software supply chain is critical infrastructure, part of national security, and vulnerable to foreign attack. The US government needs to recognize this as a national security problem and start treating it as such.
This essay originally appeared in Lawfare.
Schneier on Security: In Memoriam: Ross Anderson, 1956–2024
Last week, I posted a short memorial of Ross Anderson. The Communications of the ACM asked me to expand it. Here’s the longer version.
EDITED TO ADD (4/11): Two weeks before he passed away, Ross gave an 80-minute interview where he told his life story.
Schneier on Security: US Cyber Safety Review Board on the 2023 Microsoft Exchange Hack
The US Cyber Safety Review Board released a report on the summer 2023 hack of Microsoft Exchange by China. It was a serious attack by the Chinese government that accessed the emails of senior US government officials.
From the executive summary:
The Board finds that this intrusion was preventable and should never have occurred. The Board also concludes that Microsoft’s security culture was inadequate and requires an overhaul, particularly in light of the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations. The Board reaches this conclusion based on:
- the cascade of Microsoft’s avoidable errors that allowed this intrusion to succeed;
- Microsoft’s failure to detect the compromise of its cryptographic crown jewels on its own, relying instead on a customer to reach out to identify anomalies the customer had observed;
- the Board’s assessment of security practices at other cloud service providers, which maintained security controls that Microsoft did not;
- Microsoft’s failure to detect a compromise of an employee’s laptop from a recently acquired company prior to allowing it to connect to Microsoft’s corporate network in 2021;
- Microsoft’s decision not to correct, in a timely manner, its inaccurate public statements about this incident, including a corporate statement that Microsoft believed it had determined the likely root cause of the intrusion when in fact, it still has not; even though Microsoft acknowledged to the Board in November 2023 that its September 6, 2023 blog post about the root cause was inaccurate, it did not update that post until March 12, 2024, as the Board was concluding its review and only after the Board’s repeated questioning about Microsoft’s plans to issue a correction;
- the Board’s observation of a separate incident, disclosed by Microsoft in January 2024, the investigation of which was not in the purview of the Board’s review, which revealed a compromise that allowed a different nation-state actor to access highly-sensitive Microsoft corporate email accounts, source code repositories, and internal systems; and
- how Microsoft’s ubiquitous and critical products, which underpin essential services that support national security, the foundations of our economy, and public health and safety, require the company to demonstrate the highest standards of security, accountability, and transparency.
The report includes a bunch of recommendations. It’s worth reading in its entirety.
The board was established in early 2022, modeled in spirit after the National Transportation Safety Board. This is their third report.
EDITED TO ADD (4/15): Adam Shostack has some good commentary.
Saturday Morning Breakfast Cereal: Saturday Morning Breakfast Cereal - Learn

Click here to go see the bonus panel!
Hovertext:
Sitting in detention for having done nothing wrong is, however, excellent training for service sector work.
Today's News:
Tea Masters: Purple Da Yi 2003 vs loose Gushu from early 2000s
Both have aged dry scents, but storage smells are still more prevalent on the loose puerh, because it has spent less time in my own (relatively) dry Taiwanese storage. The Da Yi smells more woody, while the loose puerh smells more of camphor.
The taste also has lots of similarities, but I find the loose gushu a little bit thicker in taste and more harmonious. So, the Da Yi has some strong points, but the loose gushu still comes on top if your focus is purity and a thick gushu taste. And the price of the loose puerh also makes it a winner!
Planet Haskell: Chris Reade: PenroseKiteDart User Guide
Introduction
PenroseKiteDart is a Haskell package with tools to experiment with finite tilings of Penrose’s Kites and Darts. It uses the Haskell Diagrams package for drawing tilings. As well as providing drawing tools, this package introduces tile graphs (Tgraphs) for describing finite tilings. (I would like to thank Stephen Huggett for suggesting planar graphs as a way to reperesent the tilings).
This document summarises the design and use of the PenroseKiteDart package.
PenroseKiteDart package is now available on Hackage.
The source files are available on GitHub at https://github.com/chrisreade/PenroseKiteDart.
There is a small art gallery of examples created with PenroseKiteDart here.
Index
- About Penrose’s Kites and Darts
- Using the PenroseKiteDart Package (initial set up).
- Overview of Types and Operations
- Drawing in more detail
- Forcing in more detail
- Advanced Operations
- Other Reading
1. About Penrose’s Kites and Darts
The Tiles
In figure 1 we show a dart and a kite. All angles are multiples of (a tenth of a full turn). If the shorter edges are of length 1, then the longer edges are of length
, where
is the golden ratio.

Aperiodic Infinite Tilings
What is interesting about these tiles is:
It is possible to tile the entire plane with kites and darts in an aperiodic way.
Such a tiling is non-periodic and does not contain arbitrarily large periodic regions or patches.
The possibility of aperiodic tilings with kites and darts was discovered by Sir Roger Penrose in 1974. There are other shapes with this property, including a chiral aperiodic monotile discovered in 2023 by Smith, Myers, Kaplan, Goodman-Strauss. (See the Penrose Tiling Wikipedia page for the history of aperiodic tilings)
This package is entirely concerned with Penrose’s kite and dart tilings also known as P2 tilings.
Legal Tilings
In figure 2 we add a temporary green line marking purely to illustrate a rule for making legal tilings. The purpose of the rule is to exclude the possibility of periodic tilings.
If all tiles are marked as shown, then whenever tiles come together at a point, they must all be marked or must all be unmarked at that meeting point. So, for example, each long edge of a kite can be placed legally on only one of the two long edges of a dart. The kite wing vertex (which is marked) has to go next to the dart tip vertex (which is marked) and cannot go next to the dart wing vertex (which is unmarked) for a legal tiling.

Correct Tilings
Unfortunately, having a finite legal tiling is not enough to guarantee you can continue the tiling without getting stuck. Finite legal tilings which can be continued to cover the entire plane are called correct and the others (which are doomed to get stuck) are called incorrect. This means that decomposition and forcing (described later) become important tools for constructing correct finite tilings.
2. Using the PenroseKiteDart Package
You will need the Haskell Diagrams package (See Haskell Diagrams) as well as this package (PenroseKiteDart). When these are installed, you can produce diagrams with a Main.hs module. This should import a chosen backend for diagrams such as the default (SVG) along with Diagrams.Prelude.
module Main (main) where
import Diagrams.Backend.SVG.CmdLine
import Diagrams.PreludeFor Penrose’s Kite and Dart tilings, you also need to import the PKD module and (optionally) the TgraphExamples module.
import PKD
import TgraphExamplesThen to ouput someExample figure
fig::Diagram B
fig = someExample
main :: IO ()
main = mainWith figNote that the token B is used in the diagrams package to represent the chosen backend for output. So a diagram has type Diagram B. In this case B is bound to SVG by the import of the SVG backend. When the compiled module is executed it will generate an SVG file. (See Haskell Diagrams for more details on producing diagrams and using alternative backends).
3. Overview of Types and Operations
Half-Tiles
In order to implement operations on tilings (decompose in particular), we work with half-tiles. These are illustrated in figure 3 and labelled RD (right dart), LD (left dart), LK (left kite), RK (right kite). The join edges where left and right halves come together are shown with dotted lines, leaving one short edge and one long edge on each half-tile (excluding the join edge). We have shown a red dot at the vertex we regard as the origin of each half-tile (the tip of a half-dart and the base of a half-kite).
The labels are actually data constructors introduced with type operator HalfTile which has an argument type (rep) to allow for more than one representation of the half-tiles.
data HalfTile rep
= LD rep -- Left Dart
| RD rep -- Right Dart
| LK rep -- Left Kite
| RK rep -- Right Kite
deriving (Show,Eq)Tgraphs
We introduce tile graphs (Tgraphs) which provide a simple planar graph representation for finite patches of tiles. For Tgraphs we first specialise HalfTile with a triple of vertices (positive integers) to make a TileFace such as RD(1,2,3), where the vertices go clockwise round the half-tile triangle starting with the origin.
type TileFace = HalfTile (Vertex,Vertex,Vertex)
type Vertex = Int -- must be positiveThe function
makeTgraph :: [TileFace] -> Tgraphthen constructs a Tgraph from a TileFace list after checking the TileFaces satisfy certain properties (described below). We also have
faces :: Tgraph -> [TileFace]to retrieve the TileFace list from a Tgraph.
As an example, the fool (short for fool’s kite and also called an ace in the literature) consists of two kites and a dart (= 4 half-kites and 2 half-darts):
fool :: Tgraph
fool = makeTgraph [RD (1,2,3), LD (1,3,4) -- right and left dart
,LK (5,3,2), RK (5,2,7) -- left and right kite
,RK (5,4,3), LK (5,6,4) -- right and left kite
]To produce a diagram, we simply draw the Tgraph
foolFigure :: Diagram B
foolFigure = draw foolwhich will produce the diagram on the left in figure 4.
Alternatively,
foolFigure :: Diagram B
foolFigure = labelled drawj foolwill produce the diagram on the right in figure 4 (showing vertex labels and dashed join edges).
fool without labels and join edges (left), and with (right)When any (non-empty) Tgraph is drawn, a default orientation and scale are chosen based on the lowest numbered join edge. This is aligned on the positive x-axis with length 1 (for darts) or length (for kites).
Tgraph Properties
Tgraphs are actually implemented as
newtype Tgraph = Tgraph [TileFace]
deriving (Show)but the data constructor Tgraph is not exported to avoid accidentally by-passing checks for the required properties. The properties checked by makeTgraph ensure the Tgraph represents a legal tiling as a planar graph with positive vertex numbers, and that the collection of half-tile faces are both connected and have no crossing boundaries (see note below). Finally, there is a check to ensure two or more distinct vertex numbers are not used to represent the same vertex of the graph (a touching vertex check). An error is raised if there is a problem.
Note: If the TilFaces are faces of a planar graph there will also be exterior (untiled) regions, and in graph theory these would also be called faces of the graph. To avoid confusion, we will refer to these only as exterior regions, and unless otherwise stated, face will mean a TileFace. We can then define the boundary of a list of TileFaces as the edges of the exterior regions. There is a crossing boundary if the boundary crosses itself at a vertex. We exclude crossing boundaries from Tgraphs because they prevent us from calculating relative positions of tiles locally and create touching vertex problems.
For convenience, in addition to makeTgraph, we also have
makeUncheckedTgraph :: [TileFace] -> Tgraph
checkedTgraph :: [TileFace] -> TgraphThe first of these (performing no checks) is useful when you know the required properties hold. The second performs the same checks as makeTgraph except that it omits the touching vertex check. This could be used, for example, when making a Tgraph from a sub-collection of TileFaces of another Tgraph.
Main Tiling Operations
There are three key operations on finite tilings, namely
decompose :: Tgraph -> Tgraph
force :: Tgraph -> Tgraph
compose :: Tgraph -> TgraphDecompose
Decomposition (also called deflation) works by splitting each half-tile into either 2 or 3 new (smaller scale) half-tiles, to produce a new tiling. The fact that this is possible, is used to establish the existence of infinite aperiodic tilings with kites and darts. Since our Tgraphs have abstracted away from scale, the result of decomposing a Tgraph is just another Tgraph. However if we wish to compare before and after with a drawing, the latter should be scaled by a factor times the scale of the former, to reflect the change in scale.
fool (left) and decompose fool (right)We can, of course, iterate decompose to produce an infinite list of finer and finer decompositions of a Tgraph
decompositions :: Tgraph -> [Tgraph]
decompositions = iterate decomposeForce
Force works by adding any TileFaces on the boundary edges of a Tgraph which are forced. That is, where there is only one legal choice of TileFace addition consistent with the seven possible vertex types. Such additions are continued until either (i) there are no more forced cases, in which case a final (forced) Tgraph is returned, or (ii) the process finds the tiling is stuck, in which case an error is raised indicating an incorrect tiling. [In the latter case, the argument to force must have been an incorrect tiling, because the forced additions cannot produce an incorrect tiling starting from a correct tiling.]
An example is shown in figure 6. When forced, the Tgraph on the left produces the result on the right. The original is highlighted in red in the result to show what has been added.
Compose
Composition (also called inflation) is an opposite to decompose but this has complications for finite tilings, so it is not simply an inverse. (See Graphs,Kites and Darts and Theorems for more discussion of the problems). Figure 7 shows a Tgraph (left) with the result of composing (right) where we have also shown (in pale green) the faces of the original that are not included in the composition – the remainder faces.
Under some circumstances composing can fail to produce a Tgraph because there are crossing boundaries in the resulting TileFaces. However, we have established that
- If
gis a forcedTgraph, thencompose gis defined and it is also a forcedTgraph.
Try Results
It is convenient to use types of the form Try a for results where we know there can be a failure. For example, compose can fail if the result does not pass the connected and no crossing boundary check, and force can fail if its argument is an incorrect Tgraph. In situations when you would like to continue some computation rather than raise an error when there is a failure, use a try version of a function.
tryCompose :: Tgraph -> Try Tgraph
tryForce :: Tgraph -> Try TgraphWe define Try as a synonym for Either String (which is a monad) in module Tgraph.Try.
type Try a = Either String aSuccessful results have the form Right r (for some correct result r) and failure results have the form Left s (where s is a String describing the problem as a failure report).
The function
runTry:: Try a -> a
runTry = either error idwill retrieve a correct result but raise an error for failure cases. This means we can always derive an error raising version from a try version of a function by composing with runTry.
force = runTry . tryForce
compose = runTry . tryComposeElementary Tgraph and TileFace Operations
The module Tgraph.Prelude defines elementary operations on Tgraphs relating vertices, directed edges, and faces. We describe a few of them here.
When we need to refer to particular vertices of a TileFace we use
originV :: TileFace -> Vertex -- the first vertex - red dot in figure 2
oppV :: TileFace -> Vertex -- the vertex at the opposite end of the join edge from the origin
wingV :: TileFace -> Vertex -- the vertex not on the join edgeA directed edge is represented as a pair of vertices.
type Dedge = (Vertex,Vertex)So (a,b) is regarded as a directed edge from a to b. In the special case that a list of directed edges is symmetrically closed [(b,a) is in the list whenever (a,b) is in the list] we can think of this as an edge list rather than just a directed edge list.
For example,
internalEdges :: Tgraph -> [Dedge]produces an edge list, whereas
graphBoundary :: Tgraph -> [Dedge]produces single directions. Each directed edge in the resulting boundary will have a TileFace on the left and an exterior region on the right. The function
graphDedges :: Tgraph -> [Dedge]produces all the directed edges obtained by going clockwise round each TileFace so not every edge in the list has an inverse in the list.
The above three functions are defined using
faceDedges :: TileFace -> [Dedge]which produces a list of the three directed edges going clockwise round a TileFace starting at the origin vertex.
When we need to refer to particular edges of a TileFace we use
joinE :: TileFace -> Dedge -- shown dotted in figure 2
shortE :: TileFace -> Dedge -- the non-join short edge
longE :: TileFace -> Dedge -- the non-join long edgewhich are all directed clockwise round the TileFace. In contrast, joinOfTile is always directed away from the origin vertex, so is not clockwise for right darts or for left kites:
joinOfTile:: TileFace -> Dedge
joinOfTile face = (originV face, oppV face)Patches (Scaled and Positioned Tilings)
Behind the scenes, when a Tgraph is drawn, each TileFace is converted to a Piece. A Piece is another specialisation of HalfTile using a two dimensional vector to indicate the length and direction of the join edge of the half-tile (from the originV to the oppV), thus fixing its scale and orientation. The whole Tgraph then becomes a list of located Pieces called a Patch.
type Piece = HalfTile (V2 Double)
type Patch = [Located Piece]Piece drawing functions derive vectors for other edges of a half-tile piece from its join edge vector. In particular (in the TileLib module) we have
drawPiece :: Piece -> Diagram B
dashjPiece :: Piece -> Diagram B
fillPieceDK :: Colour Double -> Colour Double -> Piece -> Diagram Bwhere the first draws the non-join edges of a Piece, the second does the same but adds a dashed line for the join edge, and the third takes two colours – one for darts and one for kites, which are used to fill the piece as well as using drawPiece.
Patch is an instances of class Transformable so a Patch can be scaled, rotated, and translated.
Vertex Patches
It is useful to have an intermediate form between Tgraphs and Patches, that contains information about both the location of vertices (as 2D points), and the abstract TileFaces. This allows us to introduce labelled drawing functions (to show the vertex labels) which we then extend to Tgraphs. We call the intermediate form a VPatch (short for Vertex Patch).
type VertexLocMap = IntMap.IntMap (Point V2 Double)
data VPatch = VPatch {vLocs :: VertexLocMap, vpFaces::[TileFace]} deriving Showand
makeVP :: Tgraph -> VPatchcalculates vertex locations using a default orientation and scale.
VPatch is made an instance of class Transformable so a VPatch can also be scaled and rotated.
One essential use of this intermediate form is to be able to draw a Tgraph with labels, rotated but without the labels themselves being rotated. We can simply convert the Tgraph to a VPatch, and rotate that before drawing with labels.
labelled draw (rotate someAngle (makeVP g))We can also align a VPatch using vertex labels.
alignXaxis :: (Vertex, Vertex) -> VPatch -> VPatch So if g is a Tgraph with vertex labels a and b we can align it on the x-axis with a at the origin and b on the positive x-axis (after converting to a VPatch), instead of accepting the default orientation.
labelled draw (alignXaxis (a,b) (makeVP g))Another use of VPatches is to share the vertex location map when drawing only subsets of the faces (see Overlaid examples in the next section).
4. Drawing in More Detail
Class Drawable
There is a class Drawable with instances Tgraph, VPatch, Patch. When the token B is in scope standing for a fixed backend then we can assume
draw :: Drawable a => a -> Diagram B -- draws non-join edges
drawj :: Drawable a => a -> Diagram B -- as with draw but also draws dashed join edges
fillDK :: Drawable a => Colour Double -> Colour Double -> a -> Diagram B -- fills with colourswhere fillDK clr1 clr2 will fill darts with colour clr1 and kites with colour clr2 as well as drawing non-join edges.
These are the main drawing tools. However they are actually defined for any suitable backend b so have more general types
draw :: (Drawable a, Renderable (Path V2 Double) b) =>
a -> Diagram2D b
drawj :: (Drawable a, Renderable (Path V2 Double) b) =>
a -> Diagram2D b
fillDK :: (Drawable a, Renderable (Path V2 Double) b) =>
Colour Double -> Colour Double -> a -> Diagram2D bwhere
type Diagram2D b = QDiagram b V2 Double Anydenotes a 2D diagram using some unknown backend b, and the extra constraint requires b to be able to render 2D paths.
In these notes we will generally use the simpler description of types using B for a fixed chosen backend for the sake of clarity.
The drawing tools are each defined via the class function drawWith using Piece drawing functions.
class Drawable a where
drawWith :: (Piece -> Diagram B) -> a -> Diagram B
draw = drawWith drawPiece
drawj = drawWith dashjPiece
fillDK clr1 clr2 = drawWith (fillPieceDK clr1 clr2)To design a new drawing function, you only need to implement a function to draw a Piece, (let us call it newPieceDraw)
newPieceDraw :: Piece -> Diagram BThis can then be elevated to draw any Drawable (including Tgraphs, VPatches, and Patches) by applying the Drawable class function drawWith:
newDraw :: Drawable a => a -> Diagram B
newDraw = drawWith newPieceDrawClass DrawableLabelled
Class DrawableLabelled is defined with instances Tgraph and VPatch, but Patch is not an instance (because this does not retain vertex label information).
class DrawableLabelled a where
labelColourSize :: Colour Double -> Measure Double -> (Patch -> Diagram B) -> a -> Diagram BSo labelColourSize c m modifies a Patch drawing function to add labels (of colour c and size measure m). Measure is defined in Diagrams.Prelude with pre-defined measures tiny, verySmall, small, normal, large, veryLarge, huge. For most of our diagrams of Tgraphs, we use red labels and we also find small is a good default size choice, so we define
labelSize :: DrawableLabelled a => Measure Double -> (Patch -> Diagram B) -> a -> Diagram B
labelSize = labelColourSize red
labelled :: DrawableLabelled a => (Patch -> Diagram B) -> a -> Diagram B
labelled = labelSize smalland then labelled draw, labelled drawj, labelled (fillDK clr1 clr2) can all be used on both Tgraphs and VPatches as well as (for example) labelSize tiny draw, or labelCoulourSize blue normal drawj.
Further drawing functions
There are a few extra drawing functions built on top of the above ones. The function smart is a modifier to add dashed join edges only when they occur on the boundary of a Tgraph
smart :: (VPatch -> Diagram B) -> Tgraph -> Diagram BSo smart vpdraw g will draw dashed join edges on the boundary of g before applying the drawing function vpdraw to the VPatch for g. For example the following all draw dashed join edges only on the boundary for a Tgraph g
smart draw g
smart (labelled draw) g
smart (labelSize normal draw) gWhen using labels, the function rotateBefore allows a Tgraph to be drawn rotated without rotating the labels.
rotateBefore :: (VPatch -> a) -> Angle Double -> Tgraph -> a
rotateBefore vpdraw angle = vpdraw . rotate angle . makeVPSo for example,
rotateBefore (labelled draw) (90@@deg) gmakes sense for a Tgraph g. Of course if there are no labels we can simply use
rotate (90@@deg) (draw g)Similarly alignBefore allows a Tgraph to be aligned using a pair of vertex numbers before drawing.
alignBefore :: (VPatch -> a) -> (Vertex,Vertex) -> Tgraph -> a
alignBefore vpdraw (a,b) = vpdraw . alignXaxis (a,b) . makeVPSo, for example, if Tgraph g has vertices a and b, both
alignBefore draw (a,b) g
alignBefore (labelled draw) (a,b) gmake sense. Note that the following examples are wrong. Even though they type check, they re-orient g without repositioning the boundary joins.
smart (labelled draw . rotate angle) g -- WRONG
smart (labelled draw . alignXaxis (a,b)) g -- WRONGInstead use
smartRotateBefore (labelled draw) angle g
smartAlignBefore (labelled draw) (a,b) gwhere
smartRotateBefore :: (VPatch -> Diagram B) -> Angle Double -> Tgraph -> Diagram B
smartAlignBefore :: (VPatch -> Diagram B) -> (Vertex,Vertex) -> Tgraph -> Diagram Bare defined using
restrictSmart :: Tgraph -> (VPatch -> Diagram B) -> VPatch -> Diagram BHere, restrictSmart g vpdraw vp uses the given vp for drawing boundary joins and drawing faces of g (with vpdraw) rather than converting g to a new VPatch. This assumes vp has locations for vertices in g.
Overlaid examples (location map sharing)
The function
drawForce :: Tgraph -> Diagram Bwill (smart) draw a Tgraph g in red overlaid (using <>) on the result of force g as in figure 6. Similarly
drawPCompose :: Tgraph -> Diagram Bapplied to a Tgraph g will draw the result of a partial composition of g as in figure 7. That is a drawing of compose g but overlaid with a drawing of the remainder faces of g shown in pale green.
Both these functions make use of sharing a vertex location map to get correct alignments of overlaid diagrams. In the case of drawForce g, we know that a VPatch for force g will contain all the vertex locations for g since force only adds to a Tgraph (when it succeeds). So when constructing the diagram for g we can use the VPatch created for force g instead of starting afresh. Similarly for drawPCompose g the VPatch for g contains locations for all the vertices of compose g so compose g is drawn using the the VPatch for g instead of starting afresh.
The location map sharing is done with
subVP :: VPatch -> [TileFace] -> VPatchso that subVP vp fcs is a VPatch with the same vertex locations as vp, but replacing the faces of vp with fcs. [Of course, this can go wrong if the new faces have vertices not in the domain of the vertex location map so this needs to be used with care. Any errors would only be discovered when a diagram is created.]
For cases where labels are only going to be drawn for certain faces, we need a version of subVP which also gets rid of vertex locations that are not relevant to the faces. For this situation we have
restrictVP:: VPatch -> [TileFace] -> VPatchwhich filters out un-needed vertex locations from the vertex location map. Unlike subVP, restrictVP checks for missing vertex locations, so restrictVP vp fcs raises an error if a vertex in fcs is missing from the keys of the vertex location map of vp.
5. Forcing in More Detail
The force rules
The rules used by our force algorithm are local and derived from the fact that there are seven possible vertex types as depicted in figure 8.

Our rules are shown in figure 9 (omitting mirror symmetric versions). In each case the TileFace shown yellow needs to be added in the presence of the other TileFaces shown.
Main Forcing Operations
To make forcing efficient we convert a Tgraph to a BoundaryState to keep track of boundary information of the Tgraph, and then calculate a ForceState which combines the BoundaryState with a record of awaiting boundary edge updates (an update map). Then each face addition is carried out on a ForceState, converting back when all the face additions are complete. It makes sense to apply force (and related functions) to a Tgraph, a BoundaryState, or a ForceState, so we define a class Forcible with instances Tgraph, BoundaryState, and ForceState.
This allows us to define
force :: Forcible a => a -> a
tryForce :: Forcible a => a -> Try aThe first will raise an error if a stuck tiling is encountered. The second uses a Try result which produces a Left string for failures and a Right a for successful result a.
There are several other operations related to forcing including
stepForce :: Forcible a => Int -> a -> a
tryStepForce :: Forcible a => Int -> a -> Try a
addHalfDart, addHalfKite :: Forcible a => Dedge -> a -> a
tryAddHalfDart, tryAddHalfKite :: Forcible a => Dedge -> a -> Try aThe first two force (up to) a given number of steps (=face additions) and the other four add a half dart/kite on a given boundary edge.
Update Generators
An update generator is used to calculate which boundary edges can have a certain update. There is an update generator for each force rule, but also a combined (all update) generator. The force operations mentioned above all use the default all update generator (defaultAllUGen) but there are more general (with) versions that can be passed an update generator of choice. For example
forceWith :: Forcible a => UpdateGenerator -> a -> a
tryForceWith :: Forcible a => UpdateGenerator -> a -> Try aIn fact we defined
force = forceWith defaultAllUGen
tryForce = tryForceWith defaultAllUGenWe can also define
wholeTiles :: Forcible a => a -> a
wholeTiles = forceWith wholeTileUpdateswhere wholeTileUpdates is an update generator that just finds boundary join edges to complete whole tiles.
In addition to defaultAllUGen there is also allUGenerator which does the same thing apart from how failures are reported. The reason for keeping both is that they were constructed differently and so are useful for testing.
In fact UpdateGenerators are functions that take a BoundaryState and a focus (list of boundary directed edges) to produce an update map. Each Update is calculated as either a SafeUpdate (where two of the new face edges are on the existing boundary and no new vertex is needed) or an UnsafeUpdate (where only one edge of the new face is on the boundary and a new vertex needs to be created for a new face).
type UpdateGenerator = BoundaryState -> [Dedge] -> Try UpdateMap
type UpdateMap = Map.Map Dedge Update
data Update = SafeUpdate TileFace
| UnsafeUpdate (Vertex -> TileFace)Completing (executing) an UnsafeUpdate requires a touching vertex check to ensure that the new vertex does not clash with an existing boundary vertex. Using an existing (touching) vertex would create a crossing boundary so such an update has to be blocked.
Forcible Class Operations
The Forcible class operations are higher order and designed to allow for easy additions of further generic operations. They take care of conversions between Tgraphs, BoundaryStates and ForceStates.
class Forcible a where
tryFSOpWith :: UpdateGenerator -> (ForceState -> Try ForceState) -> a -> Try a
tryChangeBoundaryWith :: UpdateGenerator -> (BoundaryState -> Try BoundaryChange) -> a -> Try a
tryInitFSWith :: UpdateGenerator -> a -> Try ForceStateFor example, given an update generator ugen and any f:: ForceState -> Try ForceState , then f can be generalised to work on any Forcible using tryFSOpWith ugen f. This is used to define both tryForceWith and tryStepForceWith.
We also specialize tryFSOpWith to use the default update generator
tryFSOp :: Forcible a => (ForceState -> Try ForceState) -> a -> Try a
tryFSOp = tryFSOpWith defaultAllUGenSimilarly given an update generator ugen and any f:: BoundaryState -> Try BoundaryChange , then f can be generalised to work on any Forcible using tryChangeBoundaryWith ugen f. This is used to define tryAddHalfDart and tryAddHalfKite.
We also specialize tryChangeBoundaryWith to use the default update generator
tryChangeBoundary :: Forcible a => (BoundaryState -> Try BoundaryChange) -> a -> Try a
tryChangeBoundary = tryChangeBoundaryWith defaultAllUGenNote that the type BoundaryChange contains a resulting BoundaryState, the single TileFace that has been added, a list of edges removed from the boundary (of the BoundaryState prior to the face addition), and a list of the (3 or 4) boundary edges affected around the change that require checking or re-checking for updates.
The class function tryInitFSWith will use an update generator to create an initial ForceState for any Forcible. If the Forcible is already a ForceState it will do nothing. Otherwise it will calculate updates for the whole boundary. We also have the special case
tryInitFS :: Forcible a => a -> Try ForceState
tryInitFS = tryInitFSWith defaultAllUGenEfficient chains of forcing operations.
Note that (force . force) does the same as force, but we might want to chain other force related steps in a calculation.
For example, consider the following combination which, after decomposing a Tgraph, forces, then adds a half dart on a given boundary edge (d) and then forces again.
combo :: Dedge -> Tgraph -> Tgraph
combo d = force . addHalfDart d . force . decomposeSince decompose:: Tgraph -> Tgraph, the instances of force and addHalfDart d will have type Tgraph -> Tgraph so each of these operations, will begin and end with conversions between Tgraph and ForceState. We would do better to avoid these wasted intermediate conversions working only with ForceStates and keeping only those necessary conversions at the beginning and end of the whole sequence.
This can be done using tryFSOp. To see this, let us first re-express the forcing sequence using the Try monad, so
force . addHalfDart d . forcebecomes
tryForce <=< tryAddHalfDart d <=< tryForceNote that (<=<) is the Kliesli arrow which replaces composition for Monads (defined in Control.Monad). (We could also have expressed this right to left sequence with a left to right version tryForce >=> tryAddHalfDart d >=> tryForce). The definition of combo becomes
combo :: Dedge -> Tgraph -> Tgraph
combo d = runTry . (tryForce <=< tryAddHalfDart d <=< tryForce) . decomposeThis has no performance improvement, but now we can pass the sequence to tryFSOp to remove the unnecessary conversions between steps.
combo :: Dedge -> Tgraph -> Tgraph
combo d = runTry . tryFSOp (tryForce <=< tryAddHalfDart d <=< tryForce) . decomposeThe sequence actually has type Forcible a => a -> Try a but when passed to tryFSOp it specialises to type ForceState -> Try ForseState. This ensures the sequence works on a ForceState and any conversions are confined to the beginning and end of the sequence, avoiding unnecessary intermediate conversions.
A limitation of forcing
To avoid creating touching vertices (or crossing boundaries) a BoundaryState keeps track of locations of boundary vertices. At around 35,000 face additions in a single force operation the calculated positions of boundary vertices can become too inaccurate to prevent touching vertex problems. In such cases it is better to use
recalibratingForce :: Forcible a => a -> a
tryRecalibratingForce :: Forcible a => a -> Try aThese work by recalculating all vertex positions at 20,000 step intervals to get more accurate boundary vertex positions. For example, 6 decompositions of the kingGraph has 2,906 faces. Applying force to this should result in 53,574 faces but will go wrong before it reaches that. This can be fixed by calculating either
recalibratingForce (decompositions kingGraph !!6)or using an extra force before the decompositions
force (decompositions (force kingGraph) !!6)In the latter case, the final force only needs to add 17,864 faces to the 35,710 produced by decompositions (force kingGraph) !!6.
6. Advanced Operations
Guided comparison of Tgraphs
Asking if two Tgraphs are equivalent (the same apart from choice of vertex numbers) is a an np-complete problem. However, we do have an efficient guided way of comparing Tgraphs. In the module Tgraph.Rellabelling we have
sameGraph :: (Tgraph,Dedge) -> (Tgraph,Dedge) -> BoolThe expression sameGraph (g1,d1) (g2,d2) asks if g2 can be relabelled to match g1 assuming that the directed edge d2 in g2 is identified with d1 in g1. Hence the comparison is guided by the assumption that d2 corresponds to d1.
It is implemented using
tryRelabelToMatch :: (Tgraph,Dedge) -> (Tgraph,Dedge) -> Try Tgraphwhere tryRelabelToMatch (g1,d1) (g2,d2) will either fail with a Left report if a mismatch is found when relabelling g2 to match g1 or will succeed with Right g3 where g3 is a relabelled version of g2. The successful result g3 will match g1 in a maximal tile-connected collection of faces containing the face with edge d1 and have vertices disjoint from those of g1 elsewhere. The comparison tries to grow a suitable relabelling by comparing faces one at a time starting from the face with edge d1 in g1 and the face with edge d2 in g2. (This relies on the fact that Tgraphs are connected with no crossing boundaries, and hence tile-connected.)
The above function is also used to implement
tryFullUnion:: (Tgraph,Dedge) -> (Tgraph,Dedge) -> Try Tgraphwhich tries to find the union of two Tgraphs guided by a directed edge identification. However, there is an extra complexity arising from the fact that Tgraphs might overlap in more than one tile-connected region. After calculating one overlapping region, the full union uses some geometry (calculating vertex locations) to detect further overlaps.
Finally we have
commonFaces:: (Tgraph,Dedge) -> (Tgraph,Dedge) -> [TileFace]which will find common regions of overlapping faces of two Tgraphs guided by a directed edge identification. The resulting common faces will be a sub-collection of faces from the first Tgraph. These are returned as a list as they may not be a connected collection of faces and therefore not necessarily a Tgraph.
Empires and SuperForce
In Empires and SuperForce we discussed forced boundary coverings which were used to implement both a superForce operation
superForce:: Forcible a => a -> aand operations to calculate empires.
We will not repeat the descriptions here other than to note that
forcedBoundaryECovering:: Tgraph -> [Tgraph]finds boundary edge coverings after forcing a Tgraph. That is, forcedBoundaryECovering g will first force g, then (if it succeeds) finds a collection of (forced) extensions to force g such that
- each extension has the whole boundary of
force gas internal edges. - each possible addition to a boundary edge of
force g(kite or dart) has been included in the collection.
(possible here means – not leading to a stuck Tgraph when forced.) There is also
forcedBoundaryVCovering:: Tgraph -> [Tgraph]which does the same except that the extensions have all boundary vertices internal rather than just the boundary edges.
Combinations
Combinations such as
compForce:: Tgraph -> Tgraph -- compose after forcing
allCompForce:: Tgraph -> [Tgraph] -- iterated (compose after force) while not emptyTgraph
maxCompForce:: Tgraph -> Tgraph -- last item in allCompForce (or emptyTgraph)make use of theorems established in Graphs,Kites and Darts and Theorems. For example
compForce = uncheckedCompose . force which relies on the fact that composition of a forced Tgraph does not need to be checked for connectedness and no crossing boundaries. Similarly, only the initial force is necessary in allCompForce with subsequent iteration of uncheckedCompose because composition of a forced Tgraph is necessarily a forced Tgraph.
Tracked Tgraphs
The type
data TrackedTgraph = TrackedTgraph
{ tgraph :: Tgraph
, tracked :: [[TileFace]]
} deriving Showhas proven useful in experimentation as well as in producing artwork with darts and kites. The idea is to keep a record of sub-collections of faces of a Tgraph when doing both force operations and decompositions. A list of the sub-collections forms the tracked list associated with the Tgraph. We make TrackedTgraph an instance of class Forcible by having force operations only affect the Tgraph and not the tracked list. The significant idea is the implementation of
decomposeTracked :: TrackedTgraph -> TrackedTgraphDecomposition of a Tgraph involves introducing a new vertex for each long edge and each kite join. These are then used to construct the decomposed faces. For decomposeTracked we do the same for the Tgraph, but when it comes to the tracked collections, we decompose them re-using the same new vertex numbers calculated for the edges in the Tgraph. This keeps a consistent numbering between the Tgraph and tracked faces, so each item in the tracked list remains a sub-collection of faces in the Tgraph.
The function
drawTrackedTgraph :: [VPatch -> Diagram B] -> TrackedTgraph -> Diagram Bis used to draw a TrackedTgraph. It uses a list of functions to draw VPatches. The first drawing function is applied to a VPatch for any untracked faces. Subsequent functions are applied to VPatches for the tracked list in order. Each diagram is beneath later ones in the list, with the diagram for the untracked faces at the bottom. The VPatches used are all restrictions of a single VPatch for the Tgraph, so will be consistent in vertex locations. When labels are used, there is also a drawTrackedTgraphRotated and drawTrackedTgraphAligned for rotating or aligning the VPatch prior to applying the drawing functions.
Note that the result of calculating empires (see Empires and SuperForce ) is represented as a TrackedTgraph. The result is actually the common faces of a forced boundary covering, but a particular element of the covering (the first one) is chosen as the background Tgraph with the common faces as a tracked sub-collection of faces. Hence we have
empire1, empire2 :: Tgraph -> TrackedTgraph
drawEmpire :: TrackedTgraph -> Diagram BFigure 10 was also created using TrackedTgraphs.
7. Other Reading
Previous related blogs are:
- Diagrams for Penrose Tiles – the first blog introduced drawing
Pieces andPatches (without using Tgraphs) and provided a version of decomposing for Patches (decompPatch). - Graphs, Kites and Darts intoduced Tgraphs. This gave more details of implementation and results of early explorations. (The class
Forciblewas introduced subsequently). - Empires and SuperForce – these new operations were based on observing properties of boundaries of forced Tgraphs.
- Graphs,Kites and Darts and Theorems established some important results relating
force,compose,decompose.
Greater Fool – Authored by Garth Turner – The Troubled Future of Real Estate: The age bomb
Inflation stats this morning. Budget excess in the afternoon. Once the gory details are known, we’ll tell you what it means and what to do about it. Meanwhile we need to discuss the Elephant in the room.
Of all the ‘isms’ in society, only one is still acceptable. In fact, it’s everywhere. Ageism. It’s cool to dis and dismiss people just because they get old. The irony is, it happens to everyone.
Denying you’re on this journey has serious financial implications. Retirement’s long and most are unprepared. Twenty years. Maybe thirty (or more once AI steals your job). It takes a long time to get ready to retire, and apparently we’re getting worse at it. Lots of people – accountants, actuaries, advisors, bankers, economists (but not many politicians) – worry we’re headed for a retirement crisis is epic proportions.
There are five reasons that gobs of people are pooched. And they don’t yet know.
First, realize what’s going on. For decades we knew a demographic timebomb was embedded in our midst. And it’s about to blow.
Here’s an NIA report (“Perspectives on Growing Older in Canada”) that found a quarter of people over 50 – still working – don’t make enough money now to cover living expenses. Another 40% say they can get by, but set aside nothing. Obviously they’re saving zippo for the future. Meanwhile the fastest growing cohort in society is people between 75 and 79. Breathing down their necks are the 85-year-olds.
So will you have enough to live a good life between, say, sixty and eighty-five? Obviously CPP and OAS won’t do it. They were never designed to support you. And never will, unless you live frugal, cheap and denied.
It’s coming, In seven years Canada will join Japan as a ‘super aged’ society, where more than 25% of the population are seniors. Besides ballooning OAS payments so they become the greatest single expenditure of government, consider health care. Today about a fifth of the population are over 65. But these same people consumer half of all the health care. By 2040 the wrinklies will account for 71% of all health expenditures. Just imagine what they might do to personal taxes (for those still working then – today’s Millennials, Zs and Alphas).
Gulp.
A major survey by accounting firm Deloitte found 86% of people 50 to 64 are at financial risk that would see them running out of money in retirement. Of people just entering retirement, more than half (55%) have to downscale their lifestyles in order to avoid outliving their capital. These are solidly middle-class folks. They’re not in the 31% of retirees trying to live solely on government assistance. And they’re not the 14% who are ‘retirement ready’. There are only 429,000 of them in Canada, and 2.5 million who are not.
Here’s is the graphic Deloitte uses to show the sorry state of current retiring Canadians.
Source: Deloitte. Click to enlarge.
This a mess. And while we have cabinet minsters in charge of diversity and inclusion, families and children and rural economic development (plus 37 more), there’s nobody in charge of getting ready for the demographic tidal wave that will whack the economy, topple society and Hoover the treasury. So, you’re on your own.
And what is this happening?
First, we live too long. Life expectancy is headed for 84 years. It used to be that men retired at 65 and croaked two years later (the ladies lasted longer – still do). Now we need to finance decades without a paycheque.
Second, workplace pensions are fading fast. Only a third are in some kind of plan, compared with half fifty years ago. Defined benefit pensions are available mostly to government workers, while other plans are defined-contribution in nature, the bulk of which are stuffed in crappy mutual funds.
Third, we suck at retirement savings. RRSP contributions have been falling for a decade. Almost 80% of the money in TFSAs is in savings accounts, low-yield GICs or other near-cash assets – lacking the growth so clearly needed. Deloitte found a third of all working Canadians, including one in five people close to retirement age, have never saved anything for the future. Nothing.
So, fourth, it’s financial illiteracy which is endangering the years to come. Too many Canadians are labouring under the false assumption ‘the government’ will look after them in retirement, or that their living costs will plunge once they stop working, or that ‘the market’ is too scary and risky to invest in, or they’re simply unaware of how to budget, where to grow money or how to use the tools they’re given, like tax shelters.
And, yes, consuming vast amounts of income and burying millions in lifelong debt payments, is residential real estate. It is the beast feeding on retirement, when most people think it’s their only ticket out of penury.
We now owe $2.1 trillion in mortgages alone, increasing by $12.6 billion per year. Every conceivable aspect of home ownership is getting more expensive, from property tax to utilities, online connectivity, insurance, all the stuff at Home Depot and the levies, fees and commissions real estate generates. Lately the housing market has flatlined. If rates don’t fall, the economy stutters or confidence fades, Canada could easily have a housing crisis. Then what?
So, it’s choice time. You can plan on being a happy, secure old snort. Or you can be the ageist grasshopper. But nobody gets out of here alive.
About the picture: “Here is Doodles enjoying the beach side,” writes Delusional Gus. “He loves to go on self guided tours around Mystic beach BC, but not to worry, he always returns home. Thanks for your insights, after your Dr.Garth post we’ve sold the condo, maxed out the TFSA, opened a TFSA for baby girl to start compounding and will open a FHSA to purchase a house in the future. Trying our best to have a B&D and retire before 60 with the same income we have now! Rented a 3bd in Vic’s outskirts and have space, and no debt, still paying less than the condo mortgage if counting the taxes and strata. Good job, hopefully you can rescue more people.”
To be in touch or send a picture of your beast, email to ‘garth@garth.ca’.
Ideas: Humboldt's Ghost, Pt 2: The meaning of education
IDEAS continues to explore Wilhelm von Humboldt’s public education system with guests, including acclaimed author Gabor Maté, who is a former English teacher. Is this 200-year-old system equipped to meet the challenging demands of the 21st century? And does it still reflect Humboldt’s ideals, especially at the university level? *This is part two of a two-part series.
Disquiet: “Some Time Back”
I was talking, some time back, with a friend of mine about my fascination with buffers in the making of music, with the way digital memory access has become a normal function of sound production. One doesn’t simply play the sound of the moment, with the pluck of a string or the touch of a key on keyboard; one can reach back into the recent past and play something that has already occurred. Furthermore, if we gain a sense of ease in that prior moment, we can linger there, essentially inhabit that pre-moment moment for the length of the performance, and occasionally reach into the future to play that which has, in effect, not yet happened.
My friend, Mahlen Morris, has been developing virtual synthesizer modules for the freely available VCV Rack program. He does so under the splendid name Stochastic Telegraph. He got to thinking about what we were discussing, and began crafting not just one module but a suite of (currently) four modules that can be combined as one sees fit in order to create the memory-access tool of that best suits one’s imagination.
This video is a test run I made of Mahlen’s new tools. The source audio is a sample from a sample set by Lullatone, just a glistening tonal loop that plays on repeat. (It’s the first track off their Bowed Glockenspiel sample set, released back in September 2021.) That loop, 49 seconds long, is housed in that narrow little module to the left of the module labeled Memory. Memory and the five modules to its right are the ones that Mahlen is developing.
In a brief and far from comprehensive summary:
- “Memory” contains the audio
- “Depict” shows the waveform that represents not just the recording but the play heads (left hand horizontal lines) and record heads (right hand horizontal lines)
- “Ruminate” accesses and plays the audio (there are three modules doing that work here)
- “Embelish” is the record head.
Even though I have checked in with Mahlen during his development work, I am still myself in the early stages of using these, so I am probably describing some of this incorrectly. (And they are capable of far more than I do or describe here.)
In this video, two of the play heads, the red and blue ones, are traveling at twice the speed of the third play head, which is yellow. This creates an octave gap. For the first 30 seconds, that’s all that is happening. The Embellish module (the purple line on the right side) is recording to the buffer continuously from the Lullatone sample, and those three heads (red, blue, yellow) are accessing it in different ways. The lowest pitched of the play heads, the yellow one, is in “bounce” mode, meaning it plays backwards when it reaches the top. The others start again at the start — though to be clear, the buffer here isn’t constant; it’s being written over from the sample, which itself is looping.
At 30 seconds, I click the start button on the trigger sequencer, called “Algorhythm,” and it plays a simple eight-bar beat in which the third and sixth beats are silent. Each triggered moment causes the red bar to briefly play. Previously it was playing continuously; henceforth it will just play for a split second when triggered. Because it’s always accessing the same source sample, just in different places, it ends up producing a little melody where all the pieces are in tune with each other.
At 1:08, having set a melody of sorts into motion, thanks to the rhythmic consistency, I hit the random button on the Algorhythm module, which makes the remainder of the piece more abstract than what came earlier.
That’s it, three stages of the source audio: first the playback heads on their own, then the introduction of those precise little notes, and then the further randomization of the rhythmic appearance of those notes.
The other modules employed are rudimentary. “Clock” sets the pace. “RND” is a random trigger that sets where the little red play back head lands. “Push” sets the sample running (the player loops continuously — or, in the module’s compressed terminology, “cycle”s it continuously). The “Mixer” combines the three stereo channels. The “Audio” sends the sound out my laptop’s speaker. And the “Record” let me record this video.
Mahlen’s modules aren’t available yet, but they will be soon.
The Universe of Discourse: Try it and see
I thought about this because of yesterday's article about the person who needed to count the 3-colorings of an icosahedron, but didn't try constructing any to see what they were like.
Around 2015 Katara, then age 11, saw me writing up my long series of articles about the Cosmic Call message and asked me to explain what the mysterious symbols meant. (It's intended to be a message that space aliens can figure out even though they haven't met us.)
I said “I bet you could figure it out if you tried.” She didn't believe me and she didn't want to try. It seemed insurmountable.
“Okay,” I said, handing her a printed copy of page 1. “Sit on the chaise there and just look at it for five minutes without talking or asking any questions, while I work on this. Then I promise I'll explain everything.”
She figured it out in way less than five minutes. She was thrilled to discover that she could do it.
I think she learned something important that day: A person can accomplish a lot with a few minutes of uninterrupted silent thinking, perhaps more than they imagine, and certainly a lot more than if they don't try.
I think there's a passage somewhere in Zen and the Art of Motorcycle Maintenance about how, when you don't know what to do next, you should just sit with your mouth shut for a couple of minutes and see if any ideas come nibbling. Sometimes they don't. But if there are any swimming around, you won't catch them unless you're waiting for them.
Planet Haskell: Mark Jason Dominus: Try it and see
I thought about this because of yesterday's article about the person who needed to count the 3-colorings of an icosahedron, but didn't try constructing any to see what they were like.
Around 2015 Katara, then age 11, saw me writing up my long series of articles about the Cosmic Call message and asked me to explain what the mysterious symbols meant. (It's intended to be a message that space aliens can figure out even though they haven't met us.)

I said “I bet you could figure it out if you tried.” She didn't believe me and she didn't want to try. It seemed insurmountable.
“Okay,” I said, handing her a printed copy of page 1. “Sit on the chaise there and just look at it for five minutes without talking or asking any questions, while I work on this. Then I promise I'll explain everything.”
She figured it out in way less than five minutes. She was thrilled to discover that she could do it.
I think she learned something important that day: A person can accomplish a lot with a few minutes of uninterrupted silent thinking, perhaps more than they imagine, and certainly a lot more than if they don't try.
I think there's a passage somewhere in Zen and the Art of Motorcycle Maintenance about how, when you don't know what to do next, you should just sit with your mouth shut for a couple of minutes and see if any ideas come nibbling. Sometimes they don't. But if there are any swimming around, you won't catch them unless you're waiting for them.
Penny Arcade: The Pittsburgh Stealers
In the modern era of course, Gabe is a petrol-huffing speed demon. In Wheel Saint, he made me anodize his filthy carnography with a Catholoid sheen. But even if we weren't obsessives in the past, we usually kept up with the big franchises because there was a lot of fun metaphors they could bang into unique gameplay. Burnout is the, I don't know… racing platformer, I guess? Need for Speed: Hot Pursuit was a really fun version of tag. We grabbed The Crew back in the day, sometimes called a "CaRPG," and Ubisoft allowed it to live and breathe and develop a unique audience. An audience they would scourge at the beginning of the month by seizing access to the game they bought.
Penny Arcade: Ubisoft Is On Drugs
There is no universe in which I purchase the new Ubisoft Star Wars game for $70 much less $200 now that they just delete games you bought from your library. This is especially frustrating considering I’ve been playing a lot of old games recently, specifically racing ones. Going back and playing these decade old games made me realize how much I dislike the new “festival” design for these sorts of racers. The Crew Motorfest and Horizon both want me to believe that I’m participating in some kind of sanctioned event and compared to games like NFS or even the original Crew it’s just super boring. I’m having a blast with NFS Payback and NFS 2015 right now which sadly is another of these Always Online games meaning that EA could pull the plug on it at anypoint. It’s wild because they still look and play better than many modern racing games. Just because a game is 10 years old doesn’t mean it’s no good anymore especially when you look at the current state of triple A games.
CreativeApplications.Net: gr1dflow – Exploring recursive ontologies

gr1dflow is a collection of artworks created through code, delving into the world of computational space. While the flowing cells and clusters showcase the real-time and dynamic nature of the medium, the colours and the initial configuration of the complex shapes are derived from blockchain specific metadata associated with the collection.
Submitted by: 0xStc
Category: Member Submissions
Tags: audiovisual / blockchain / generative / glsl / NFT / realtime / recursion
People: Agoston Nagy
Saturday Morning Breakfast Cereal: Saturday Morning Breakfast Cereal - Lit

Click here to go see the bonus panel!
Hovertext:
Written after enjoying Children's Fantasy Literature, by Levy and Menlesohn.
Today's News:
Michael Geist: The Law Bytes Podcast, Episode 199: Boris Bytensky on the Criminal Code Reforms in the Online Harms Act

The Online Harms Act – otherwise known as Bill C-63 – is really at least three bills in one. The Law Bytes podcast tackled the Internet platform portion of the bill last month in an episode with Vivek Krishnamurthy and then last week Professor Richard Moon joined to talk about the return of Section 13 of the Canada Human Rights Act. Part three may the most controversial: the inclusion of Criminal Code changes that have left even supporters of the bill uncomfortable.
Boris Bytensky of the firm Bytensky Shikhman has been a leading Canadian criminal law lawyer for decades and currently serves as President of the Criminal Lawyers’ Association. He joins the podcast to discuss the bill’s Criminal Code reforms as he identifies some of the practical implications that have thus far been largely overlooked in the public debate.
The podcast can be downloaded here, accessed on YouTube, and is embedded below. Subscribe to the podcast via Apple Podcast, Google Play, Spotify or the RSS feed. Updates on the podcast on Twitter at @Lawbytespod.
Credits:
W5, A Shocking Upsurge of Hate Crimes in Canada
The post The Law Bytes Podcast, Episode 199: Boris Bytensky on the Criminal Code Reforms in the Online Harms Act appeared first on Michael Geist.
Ideas: Humboldt's Ghost, Pt 1: Origins of our 200 year-old public education system
Two hundred years ago, Wilhelm von Humboldt created the public education system as we know it today. At the heart of his philosophy of education was the concept of Bildung — reaching one's inner potential. Yet over the years, as his public education system was adopted, Bildung may well have been the critical piece left out. *This is part one of a two-part series.
Tea Masters: Another puerh comparison: Yiwu from 2003 vs. DaYi purple cake from 2003
 |
| Yiwu 2003 vs DaYi purple 2003 |
Conclusion: During the CNNP era, tea drinkers didn't have much choice. There were only few puerh factories and they produced almost exclusively cakes that were mixed leaves. A few years later, in 2003, more choice became available. Those who trusted my advice back then have been rewarded with a puerh that has remained superior in quality over the years and that still tastes more harmonious than the Purple Da Yi of 2003.
Project Gus: Unremarkable Kona Progress
I've been holding off posting as I haven't had any major breakthroughs with the Kona Electric reversing project. However, I haven't sat totally idle...
On-car testing
Last post the Kona motor started to spin, but without a load attached it was spinning out of control! Even in Neutral, the motor …
Disquiet: Haring 1984 Boombox

A Keith Haring boombox illustration from 1984, displayed as part of the Urban Art Evolution exhibit at the Nassau County Museum of Art through July 7, 2024
The Shape of Code: Average lines added/deleted by commits across languages
Are programs written in some programming language shorter/longer, on average, than when written in other languages?
There is a lot of variation in the length of the same program written in the same language, across different developers. Comparing program length across different languages requires a large sample of programs, each implemented in different languages, and by many different developers. This sounds like a fantasy sample, given the rarity of finding the same specification implemented multiple times in the same language.
There is a possible alternative approach to answering this question: Compare the size of commits, in lines of code, for many different programs across a variety of languages. The paper: A Study of Bug Resolution Characteristics in Popular Programming Languages by Zhang, Li, Hao, Wang, Tang, Zhang, and Harman studied 3,232,937 commits across 585 projects and 10 programming languages (between 56 and 60 projects per language, with between 58,533 and 474,497 commits per language).
The data on each commit includes: lines added, lines deleted, files changed, language, project, type of commit, lines of code in project (at some point in time). The paper investigate bug resolution characteristics, but does not include any data on number of people available to fix reported issues; I focused on all lines added/deleted.
Different projects (programs) will have different characteristics. For instance, a smaller program provides more scope for adding lots of new functionality, and a larger program contains more code that can be deleted. Some projects/developers commit every change (i.e., many small commit), while others only commit when the change is completed (i.e., larger commits). There may also be algorithmic characteristics that affect the quantity of code written, e.g., availability of libraries or need for detailed bit twiddling.
It is not possible to include project-id directly in the model, because each project is written in a different language, i.e., language can be predicted from project-id. However, program size can be included as a continuous variable (only one LOC value is available, which is not ideal).
The following R code fits a basic model (the number of lines added/deleted is count data and usually small, so a Poisson distribution is assumed; given the wide range of commit sizes, quantile regression may be a better approach):
alang_mod=glm(additions ~ language+log(LOC), data=lc, family="poisson")
dlang_mod=glm(deletions ~ language+log(LOC), data=lc, family="poisson")
Some of the commits involve tens of thousands of lines (see plot below). This sounds rather extreme. So two sets of models are fitted, one with the original data and the other only including commits with additions/deletions containing less than 10,000 lines.
These models fit the mean number of lines added/deleted over all projects written in a particular language, and the models are multiplicative. As expected, the variance explained by these two factors is small, at around 5%. The two models fitted are (code+data):
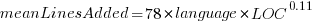 or
or 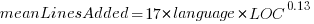 , and
, and 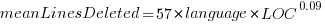 or
or 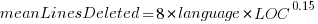 , where the value of
, where the value of  is listed in the following table, and
is listed in the following table, and  is the number of lines of code in the project:
is the number of lines of code in the project:
Original 0 < lines < 10000
Language Added Deleted Added Deleted
C 1.0 1.0 1.0 1.0
C# 1.7 1.6 1.5 1.5
C++ 1.9 2.1 1.3 1.4
Go 1.4 1.2 1.3 1.2
Java 0.9 1.0 1.5 1.5
Javascript 1.1 1.1 1.3 1.6
Objective-C 1.2 1.4 2.0 2.4
PHP 2.5 2.6 1.7 1.9
Python 0.7 0.7 0.8 0.8
Ruby 0.3 0.3 0.7 0.7
These fitted models suggest that commit addition/deletion both increase as project size increases, by around  , and that, for instance, a commit in Go adds 1.4 times as many lines as C, and delete 1.2 as many lines (averaged over all commits). Comparing adds/deletes for the same language: on average, a Go commit adds
, and that, for instance, a commit in Go adds 1.4 times as many lines as C, and delete 1.2 as many lines (averaged over all commits). Comparing adds/deletes for the same language: on average, a Go commit adds 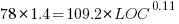 lines, and deletes
lines, and deletes 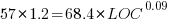 lines.
lines.
There is a strong connection between the number of lines added/deleted in each commit. The plot below shows the lines added/deleted by each commit, with the red line showing a fitted regression model 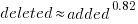 (code+data):
(code+data):
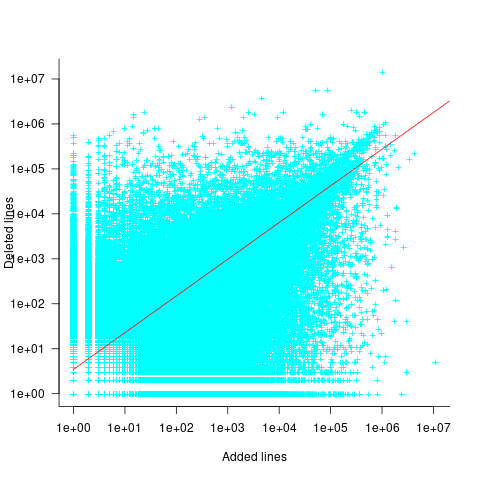
What other information can be included in a model? It is possible that project specific behavior(s) create a correlation between the size of commits; the algorithm used to fit this model assumes zero correlation. The glmer function, in the R package lme4, can take account of correlation between commits. The model component (language | project) in the following code adds project as a random effect on the language variable:
del_lmod=glmer(deletions ~ language+log(LOC)+(language | project), data=lc_loc, family=poisson)
It takes around 24hr of cpu time to fit this model, which means I have not done much experimentation...
Saturday Morning Breakfast Cereal: Saturday Morning Breakfast Cereal - Pain

Click here to go see the bonus panel!
Hovertext:
That one guy is actually a robot designed to look like a human, so it's cool.
Today's News:
The Universe of Discourse: Stuff that is and isn't backwards in Australia
I recently wrote about things that are backwards in Australia. I made this controversial claim:
The sun in the Southern Hemisphere moves counterclockwise across the sky over the course of the day, rather than clockwise. Instead of coming up on the left and going down on the right, as it does in the Northern Hemisphere, it comes up on the right and goes down on the left.
Many people found this confusing and I'm not sure our minds met on this. I am going to try to explain and see if I can clear up the puzzles.
“Which way are you facing?” was a frequent question. “If you're facing north, it comes up on the right, not the left.”
(To prevent endless parenthetical “(in the Northern Hemisphere)” qualifications, the rest of this article will describe how things look where I live, in the northern temperate zones. I understand that things will be reversed in the Southern Hemisphere, and quite different near the equator and the poles.)
Here's what I think the sky looks like most of the day on most of the days of the year:
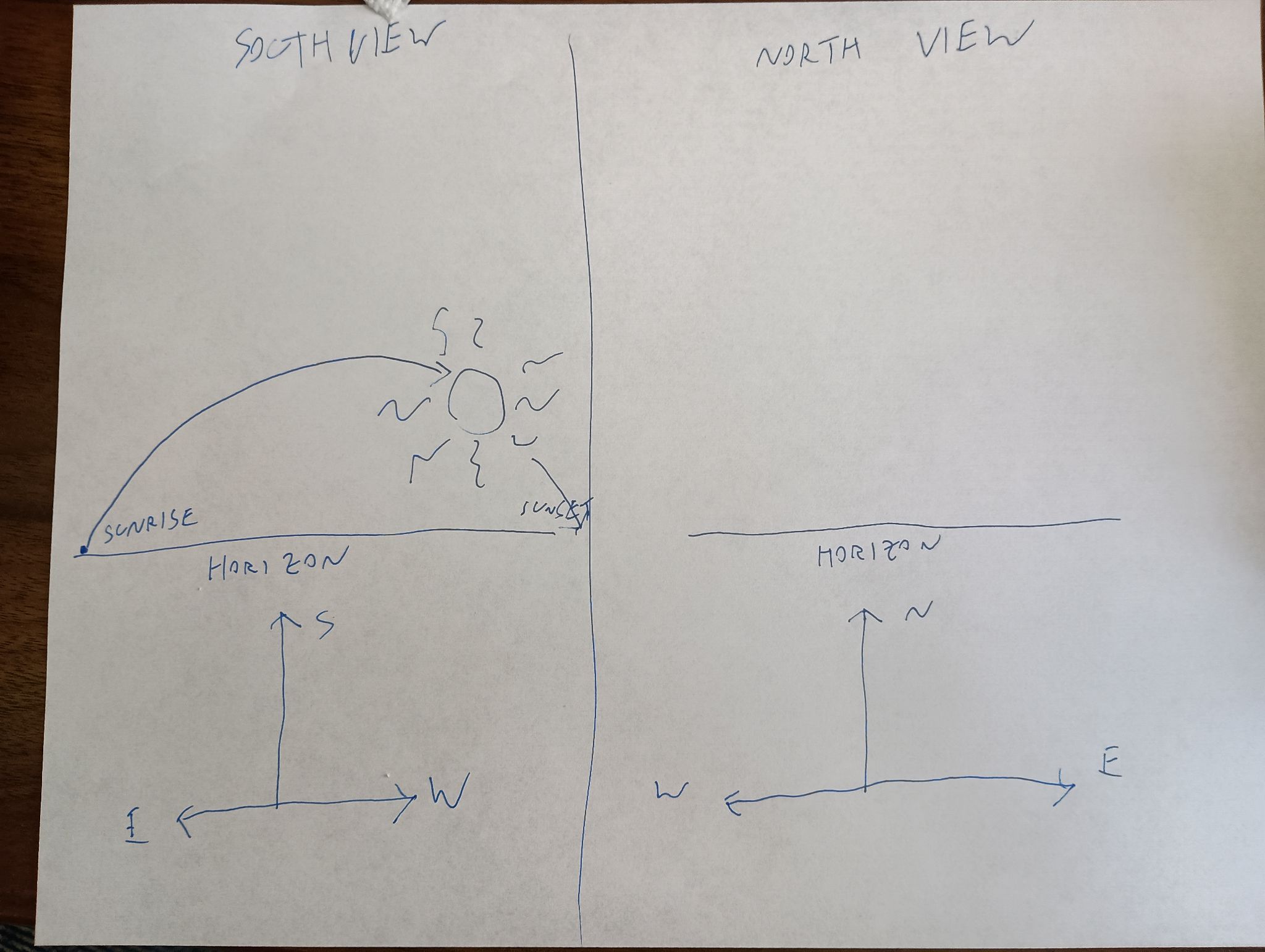
The sun is in the southern sky through the entire autumn, winter, and spring. In summer it is sometimes north of the celestial equator, for up to a couple of hours after sunrise and before sunset, but it is still in the southern sky most of the time. If you are watching the sun's path through the sky, you are looking south, not north, because if you are looking north you do not see the sun, it is behind you.
Some people even tried to argue that if you face north, the sun's path is a counterclockwise circle, rather than a clockwise one. This is risible. Here's my grandfather's old grandfather clock. Notice that the hands go counterclockwise! You study the clock and disagree. They don't go counterclockwise, you say, they go clockwise, just like on every other clock. Aha, but no, I say! If you were standing behind the clock, looking into it with the back door open, then you would clearly see the hands go counterclockwise! Then you kick me in the shin, as I deserve.
Yes, if you were to face away from the sun, its path could be said to be counterclockwise, if you could see it. But that is not how we describe things. If I say that a train passed left to right, you would not normally expect me to add “but it would have been right to left, had I been facing the tracks”.
At least one person said they had imagined the sun rising directly ahead, then passing overhead, and going down in back. Okay, fair enough. You don't say that the train passed left to right if you were standing on the tracks and it ran you down.
Except that the sun does not pass directly overhead. It only does that in the tropics. If this person were really facing the sun as it rose, and stayed facing that way, the sun would go up toward their right side. If it were a train, the train tracks would go in a big curve around their right (south) side, from left to right:
Mixed gauge track (950 and 1435mm) at Sassari station, Sardinia, 1996 by user Afterbrunel, CC BY-SA 3.0 DEED, via Wikimedia Commons. I added the big green arrows.
After the train passed, it would go back the other way, but they wouldn't be able see it, because it would be behind them. If they turned around to watch it go, it would still go left to right:
And if they were to turn to follow it over the course of the day, they would be turning left to right the whole time, and the sun would be moving from left to right the whole time, going up on the left and coming down on the right, like the hands of a clock — “clockwise”, as it were.
One correspondent suggested that perhaps many people in technologically advanced countries are not actually familiar with how the sun and moon move, and this was the cause of some of the confusion. Perhaps so, it's certainly tempting to dismiss my critics as not knowing how the sun behaves. The other possibility is that I am utterly confused. I took Observational Astronomy in college twice, and failed both times.
Anyway, I will maybe admit that “left to right” was unclear. But I will not recant my claim that the sun moves clockwise. E pur si muove in senso orario.
Sundials
Here I was just dead wrong. I said:
In the Northern Hemisphere, the shadow of a sundial proceeds clockwise, from left to right.
Absolutely not, none of this is correct. First, “left to right”. Here's a diagram of a typical sundial:

It has a sticky-up thing called a ‘gnomon’ that casts a shadow across the numbers, and the shadow moves from left to right over the course of the day. But obviously the sundial will work just as well if you walk around and look at it from the other side:

It still goes clockwise, but now clockwise is right to left instead of left to right.
It's hard to read because the numerals are upside down? Fine, whatever:

Here, unlike with the sun, “go around to the other side” is perfectly reasonable.
Talking with Joe Ardent, I realized that not even “clockwise” is required for sundials. Imagine the south-facing wall of a building, with the gnomon sticking out of it perpendicular. When the sun passes overhead, the gnomon will cast a shadow downwards on the wall, and the downward-pointing shadow will move from left to right — counterclockwise — as the sun makes its way from east to west. It's not even far-fetched. Indeed, a search for “vertical sundials” produced numerous examples:

Sundial on the Moot Hall by David Dixon, CC BY 2.0 https://creativecommons.org/licenses/by/2.0, via Wikimedia Commons and Geograph.
Winter weather on July 4
Finally, it was reported that there were complaints on Hacker News that Australians do not celebrate July 4th. Ridiculous! All patriotic Americans celebrate July 4th.
The Universe of Discourse: Stuff that is backwards in Australia
I thought at first was going to be kind of a dumb article, because it was just going to be a list of banal stuff like:
- When it's day here, it's night there, and vice versa
but a couple of years back I was rather startled to realize that in the Southern Hemisphere the sun comes up on the right and goes counterclockwise through the sky instead of coming up on the left and going clockwise as I have seen it do all my life, and that was pretty interesting.
Then more recently I was thinking about it more carefully and I was stunned when I realized that the phases of the moon go the other way. So I thought I'd should actually make the list, because a good deal of it is not at all obvious. Or at least it wasn't to me!
When it's day here, it's night there, and vice versa. (This isn't a Southern Hemisphere thing, it's an Eastern Hemisphere thing.)
When it's summer here, it's winter there, and vice versa. Australians celebrate Christmas by going to the beach, and July 4th with sledding and patriotic snowball fights.
Australia's warmer zones are in the north, not the south. Their birds fly north for the winter. But winter is in July, so the reversals cancel out and birds everywhere fly south in September and October, and north in March and April, even though birds can't read.
The sun in the Southern Hemisphere moves counterclockwise across the sky over the course of the day, rather than clockwise. Instead of coming up on the left and going down on the right, as it does in the Northern Hemisphere, it comes up on the right and goes down on the left.
In the Northern Hemisphere, the shadow of a sundial proceeds clockwise, from left to right. (This is the reason clock hands also go clockwise: for backward compatibility with sundials.) But in the Southern Hemisphere, the shadow on a sundial goes counterclockwise.
In the Southern Hemisphere, the designs on the moon appear upside-down compared with how they look in the Northern Hemisphere. Here's a picture of the full moon as seen from the Northern Hemisphere. The big crater with the bright rays that is prominent in the bottom half of the picture is Tycho.

In the Southern Hemisphere the moon looks like this, with Tycho on top:

Australians see the moon upside-down because their heads are literally pointing in the opposite direction.
For the same reason, the Moon's phases in the Southern Hemisphere sweep from left to right instead of from right to left. In the Northern Hemisphere they go like this as the month passes from new to full:





And then in the same direction from full back to new:





But in the Southern Hemisphere the moon changes from left to right instead:





And then:





Unicode U+263D and U+263E are called
FIRST QUARTER MOON☽ andLAST QUARTER MOON☾ , respectively, and are depicted Northern Hemisphere style. (In the Southern Hemisphere, ☽ appears during the last quarter of the month, not the first.) Similarly the emoji U+1F311 through U+1F318, 🌑🌒🌓🌔🌕🌖🌗🌘 are depicted in Northern Hemisphere order, and have Northern Hemisphere descriptions like “🌒 waxing crescent moon”. In the Southern Hemisphere, 🌒 is actually a waning crescent.In the Northern Hemisphere a Foucault pendulum will knock down the pins in clockwise order, as shown in the picture. (This one happens to be in Barcelona.) A Southern Hemisphere Foucault pendulum will knock them down in counterclockwise order, because the Earth is turning the other way, as viewed from the fulcrum of the pendulum.
Northern Hemisphere tornadoes always rotate counterclockwise. Southern Hemisphere tornadoes always rotate clockwise.
Dishonorable mention
As far as I know the thing about water going down the drain in one direction or the other is not actually true.
Addendum 20240414
Several people took issue with some of the claims in this article, and the part about sundials was completely wrong. I wrote a followup.
new shelton wet/dry: Acme Klein Bottles

Employee Sneaks His Own Painting Onto the Walls of a German Museum
Cash incentives for weight loss work only for males
Sleeping more flushes junk out of the brain
Patterns of Verbal and Nonverbal Communication During Sex […] most preferred to communicate pleasure nonverbally. Some participants reported a tendency to communicate pain or dislike verbally.
Why do some people always get lost? Research suggests that experience may matter more than innate ability when it comes to a sense of direction
NUS scientists uncover a missing link between poor diet and higher cancer risk — methylglyoxal, which is a chemical produced when our cells break down glucose to create energy, can cause faults in our DNA that are early warning signs of cancer development
Louisiana High Court: Priests Have a “Property Right” Not to Be Sued For Sexual Abuse
AI Could Explain Why We’re Not Meeting Any Aliens Previously: where might this Great Filter be located?
The goal is to put a robot in the most dangerous spot on the battlefield instead of a 19-year-old private fresh out of basic training. […] The robots don’t have peripheral vision; they can’t look left or look right like a human soldier can by simply turning their head. And the Army’s outdated network can’t always keep hundreds of drones aloft at the same time, or even tell U.S. troops which of the unpiloted aircraft are friend or foe. [But] Army leaders believe that almost every U.S. Army unit, down to the smallest foot patrols, will soon have drones in the sky to sense, protect, and attack. And it won’t be long before the United States is deploying ground robots into battle in human-machine teams. […] Today, the Army might have three platoons deployed in a basic attack: one to fix the enemy in place, another to maneuver on them, and then one more in reserve. Put robots into that group of soldiers […] “Then you have basically three platoons entirely freed up”
In 2023, the average cost of attending law school reached $220,335 over three years—$146,484 of which goes to tuition alone. The fancier the school, the higher the sticker price: At Columbia Law School, the current cost of attendance is $118,357 per year, with tuition alone coming in at just under $80,000 annually. At Harvard Law, the annual cost of attendance is $116,00, or $348,000 over the course of a J.D. Although law school has never been considered cheap, these numbers represent a dramatic increase in recent years. In 2002, tuition at private law schools averaged $24,193 per year; in 2022, just 20 years later, that average had gone up to $54,070. […] Law school is getting more expensive and less useful to students. The Federalist Society is happy to fill the void.
Stamp prices in the U.S. and other countries
Postcards Revolutionized Pornography
Clifford Stoll is currently the sole proprietor and sole employee of Acme Klein Bottles. […] A Klein bottle is what mathematicians call a “non-orientable surface,” a one-sided plane that, when traversed, brings the traveler back to their starting point, while also flipping them upside-down. […] Its inside is its outside; you can’t tell which side you are on.
Let us look at how depictions of Odysseus and the Sirens change, depending on location, local tradition, a given society’s fashions, and popular tastes. […] So far I have found no images of a ‘syrinx’ – the pan-flute or panpipes – being played by Sirens on Greek vases, or otherwise in Greek art.
Planet Lisp: Paolo Amoroso: Testing the Practical Common Lisp code on Medley
When the Medley Interlisp Project began reviving the system around 2020, its Common Lisp implementation was in the state it had when commercial development petered out in the 1990s, mostly prior to the ANSI standard.
Back then Medley Common Lisp mostly supported CLtL1 plus CLOS and the condition system. Some patches submitted several years later to bring the language closer to CLtL2 needed review and integration.
Aside from these general areas there was no detailed information on what Medley missed or differed from ANSI Common Lisp.
In late 2021 Larry Masinter proposed to evaluate the ANSI compatibility of Medley Common Lisp by running the code of popular Common Lisp books and documenting any divergences. In March of 2024 I set to work to test the code of the book Practical Common Lisp by Peter Seibel.
I went over the book chapter by chapter and completed a first pass, documenting the effort in a GitHub issue and a series of discussion posts. In addition I updated a running list of divergences from ANSI Common Lisp.
Methodology
Part of the code of the book is contained in the examples in the text and the rest in the downloadable source files, which constitute some more substantial projects.
To test the code on Medley I evaluated the definitions and expressions at a Xerox Common Lisp Exec, noting any errors or differences from the expected outcomes. When relevant source files were available I loaded them prior to evaluating the test expressions so that any required definitions and dependencies were present. ASDF hasn't been ported to Medley, so I loaded the files manually.
Adapting the code
Before running the code I had to apply a number of changes. I filled in any missing function and class definitions the book leaves out as incidental to the exposition. This also involved adding appropriate function calls and object instantiations to exercise the definitions or produce the expected output.
The source files of the book needed adaptation too due to the way Medley handles pure Common Lisp files.
Skipped code
The text and source files contain also code I couldn't run because some features are known to be missing from Medley, or key dependencies can't be fulfilled. For example, a few chapters rely on the AllegroServe HTTP server which doesn't run on Medley. Although Medley does have a XNS network stack, providing the TCP/IP network functions AllegroServe assumes would be a major project.
Some chapters depend on code in earlier chapters that uses features not available in Medley Common Lisp, so I had to skip those too.
Findings
Having completed the first pass over Practical Common Lisp, my initial impression is Medley's implementation of Common Lisp is capable and extensive. It can run with minor or no changes code that uses most basic and intermediate Common Lisp features.
The majority of the code I tried ran as expected. However, this work did reveal significant gaps and divergences from ANSI.
To account for the residential environment and other peculiarities of Medley, packages need to be defined in a specific way. For example, some common defpackage keyword arguments differ from ANSI. Also, uppercase strings seem to work better than keywords as package designators.
As for the gaps the loop iteration macro, symbol-macrolet, the #p reader macro, and other features turned out to be missing or not work.
While the incompatibilities with ANSI Common Lisp are relativaly easy to address or work around, what new users may find more difficult is understanding and using the residential environment of Medley.
Bringing Medley closer to ANSI Common Lisp
To plug the gaps this project uncovered Larry ported or implemented some of the missing features and fixed a few issues.
He ported a loop implementation which he's enhancing to add missing functionality like iterating over hash tables. Iterating over packages, which loop lacks at this time, is trickier. More work went into adding #p and an experimental symbol-macrolet.
Reviewing and merging the CLtL2 patches is still an open issue, a major project that involves substantial effort.
Future work and conclusion
When the new features are ready I'll do a second pass to check if more of the skipped code runs. Another outcome of the work may be the beginning of a test suite for Medley Common Lisp.
Regardless of the limitations, what the project highlighted is Medley is ready as a development environment for writing new Common Lisp code, or porting libraries and applications of small to medium complexity.
Discuss... Email | Reply @amoroso@fosstodon.org
MattCha's Blog: 1999-2003 Mr Chen’s JiaJi Green Mark
This 1999-2003 Mr Chen’s JaiJi Green Ink sample came free with the purchase of the 1999 Mr Chen Daye ZhengShan MTF Special Order. I didn’t go to the site so blind to the price and description and tried it after a session of the ZhongShan MTF Special Order…
Dry leaves have a dry woody dirt faint taste.
Rinsed leaves have a creamy sweet odour.
First infusion has a sweet watery onset there is a return of sweet woody slight warm spice. Sweet, simple, watery and clean in this first infusion.
Second infusion has a sweet watery simple woody watery sweet taste. Slight woody incense and slight fresh fruity taste. Cooling mouth. Sweet bread slight faint candy aftertaste. Slight drying mouthfeel.
Third infusions has a woody dry wood onset with a dry woody sweet kind of taste. The return is a bready candy with sweet aftertaste. Tastes faintly like red rope licorice. Dry mouthfeeling now. Somewhat relaxing qi. Mild but slight feel good feeling. Mild Qi feeling.
Fourth infusion is left to cool and is creamy sweet watery with a faint background wood and even faint incense. Simple sweet clean tastes. Thin dry mouthfeel.
Fifth infusion is a slight creamy sweet watery slight woody simple sweet pure tasting. left to cool is a creamy sweet some lubricant watery sweetness.
Sixth has an incense creamy sweet talc woody creamy more full sweetness initially. Creamy sweetness watery mild Qi. Enjoyable and easy drinking puerh.
Seventh has a sweet woody leaf watery taste with an incense woody watery base. The mouthfeel is slightly dry and qi is pretty mild and agreeable.
Eighth infusion is a woody watery sweet with subtle incense warm spice. Mild dry mouthfeel.
Ninth infusion has a woody incense onset with sweet edges. Dry flat mouthfeel and mild qi.
Tenth I put into long mug steepings… it has a dirt woody bland slight bitter taste… not much for sweetness anymore.
Overnight infusion has a watery bland, slight dirt, slight sweet insipid taste.
This is a pretty simple and straightforward dry stored aged sheng. Sweet woody incense taste with mild dry and mild relaxing feel good qi. On a busy day at work I appreciated its steady aged simplicity. I go to the site and look at the price and description and I couldn’t really agree more. The price is a bit lower than I thought and the description is dead on!
Vs 1999 Mr Chen’s Daye ZhengShan MTF Special Order- despite coming from the same collector, being both dry stored, and being the same approx age these are very different puerh. The MTF special order is much more complex in taste, very very sweet and has much more powerful space out Qi. This JaiJi Green ink is satisfying enough but not so fancy complex or mind-bending. It’s more of an aged dry storage drinker.
After a session of the 1999 Mr Chen Daye ZhengShan I did a back to back with 2001 Naked Yiwu from TeasWeLike but they are also completely differ puerh… the Nake Yiwu was much more condensed, present, and powerful in taste with sweet tastes, resin wood, and smoke incense. It’s more aggressive and forward and feels less aged than the 1999 ZhengShan MTF Special Order but in the same way it can be more satisfying especially for the price which seems like a pretty good deal. I suppose all three of these are good value dispite the totally different vibes of each.
Pictured is Left 2001 Naked Yiwu from TeasWeLike, Middle 1999 Mr Chen’s Daye ZhengShan MTF, Right 2001-1999 Me Chen’s JiaJi Green Ink.
Peace
Daniel Lemire's blog: Science and Technology links (April 13 2024)
-
-
- Our computer hardware exchange data using a standard called PCI Express. Your disk, your network and your GPU are limited by what PCI Express can do. Currently, it means that you are limited to a few gigabytes per second of bandwidth. PCI Express is about to receive a big performance boost in 2025 when PCI Express 7 comes out: it will support bandwidth of up to 512 GB/s. That is really, really fast. It does not follow that your disks and graphics are going to improve very soon, but it provides the foundation for future breakthroughs.
- Sperm counts are down everywhere and the trend is showing no sign of slowing down. There are indications that it could be related to the rise in obesity.
- A research paper by Burke et al. used a model to predict that climate change could reduce world GPD (the size of the economy) by 23%. For reference, world GDP grows at a rate of about 3% a year (+/- 1%) so that a cost of 23% is about equivalent to 7 to 8 years without growth. It is much higher than prior predictions. Barket (2024) questions these results:
It is a complicated paper that makes strong claims. The authors use thousands of lines of code to run regressions containing over 500 variables to test a nonlinear model of temperature and growth for 166 countries and forecast economic growth out to the year 2100. Careful analysis of their work shows that they bury inconvenient results, use misleading charts to confuse readers, and fail to report obvious robustness checks. Simulations suggest that the statistical significance of their results is inflated. Continued economic growth at levels similar to what the world has experienced in recent years would increase the level of future economic activity by far more than Nordhaus’ (2018) estimate of the effect of warming on future world GDP. If warming does not affect the rate of economic growth, then the world is likely to be much richer in the future, with or without warming temperatures.
- The firm McKinsey reports finding statistically significant positive relations between the industry-adjusted earnings and the racial/ethnic diversity of their executives. Green and Hand (2024) fail to reproduce these results. They conclude: despite the imprimatur given to McKinsey’s studies, their results should not be relied on to support the view that US publicly traded firms can expect to deliver improved financial performance if they increase the racial/ethnic diversity of their executives.
- Corinth and Larrimore (2024) find that after adjusting for hours worked, Generation X and Millennials experienced a greater intergenerational increase in real market income than baby boomers.
-
Daniel Lemire's blog: Greatest common divisor, the extended Euclidean algorithm, and speed!
We sometimes need to find the greatest common divisor between two integers in software. The fastest way to compute the greatest common divisor might be the binary Euclidean algorithm. In C++20, it can be implemented generically as follows:
template <typename int_type> int_type binary_gcd(int_type u, int_type v) { if (u == 0) { return v; } if (v == 0) { return u; } auto shift = std::countr_zero(u | v); u >>= std::countr_zero(u); do { v >>= std::countr_zero(v); if (u > v) { std::swap(u, v); } v = v - u; } while (v != 0); return u << shift; }
The std::countr_zero function computes the “number of trailing zeroes” in an integer. A key insight is that this function often translates into a single instruction on modern hardware.
There are many variations that might be more efficient. I like an approach proposed by Paolo Bonzini which is simpler as it avoid the swap:
int_type binary_gcd_noswap(int_type u, int_type v) { if (u == 0) { return v; } if (v == 0) { return u; } auto shift = std::countr_zero(u | v); u >>= std::countr_zero(u); do { int_type t = v >> std::countr_zero(v); if (u > t) v = u - t, u = t; else v = t - u; } while (v != 0); return u << shift; }
The binary Euclidean algorithm is typically faster than the textbook Euclidean algorithm which has to do divisions (a slow operation), although the resulting code is pleasantly short:
template <typename int_type> int_type naive_gcd(int_type u, int_type v) { return (u % v) == 0 ? v : naive_gcd(v, u % v); }
I found interesting that there is a now a std::gcd function in the C++ standard library so you may not want to implement your own greatest-common-divisor if you are programming in modern C++.
For the mathematically inclined, there is also an extended Euclidean algorithm. It also computes the greatest common divisor, but also the Bézout coefficients. That is, given two integers a and b, it finds integers x and y such that x * a + y * b = gcd(a,b). I must admit that I never had any need for the extended Euclidean algorithm. Wikipedia says that it is useful to find multiplicative inverses in a module space, but the only multiplicative inverses I ever needed were computed with a fast Newton algorithm. Nevertheless, we might implement it as follows:
template <typename int_type> struct bezout { int_type gcd; int_type x; int_type y; }; // computes the greatest common divisor between a and b, // as well as the Bézout coefficients x and y such as // a*x + b*y = gcd(a,b) template <typename int_type> bezout<int_type> extended_gcd(int_type u, int_type v) { std::pair<int_type, int_type> r = {u, v}; std::pair<int_type, int_type> s = {1, 0}; std::pair<int_type, int_type> t = {0, 1}; while (r.second != 0) { auto quotient = r.first / r.second; r = {r.second, r.first - quotient * r.second}; s = {s.second, s.first - quotient * s.second}; t = {t.second, t.first - quotient * t.second}; } return {r.first, s.first, t.first}; }
There is also a binary version of the extended Euclidean algorithm although it is quite a bit more involved and it is not clear that it is can be implemented at high speed, leveraging fast instructions, when working on integers that fit in general-purpose registers. It is may beneficial when working with big integers. I am not going to reproduce my implementation, but it is available in my software repository.
To compare these functions, I decided to benchmark them over random 64-bit integers. I found interesting that the majority of pairs of random integers (about two thirds) were coprime, meaning that their greatest common divisor is 1. Mathematically, we would expect the ratio to be 6/pi2 which is about right empirically. At least some had non-trivial greatest common divisors (e.g., 42954).
Computing the greatest common divisor takes hundreds of instructions and hundreds of CPU cycle. If you somehow need to do it often, it could be a bottleneck.
I find that the std::gcd implementation which is part of the GCC C++ library under Linux is about as fast as the binary Euclidean function I presented. I have not looked at the implementation, but I assume that it might be well designed. The version that is present on the C++ library present on macOS (libc++) appears to be the naive implementation. Thus there is an opportunity to improve the lib++ implementation.
The extended Euclidean-algorithm implementation runs at about the same speed as a naive regular Euclidean-algorithm implementation, which is what you would expect. My implementation of the binary extended Euclidean algorithm is quite a bit slower and not recommended. I expect that it should be possible to optimize it further.
| function | GCC 12 + Intel Ice Lake | Apple LLVM + M2 |
|---|---|---|
| std::gcd | 7.2 million/s | 7.8 million/s |
| binary | 7.7 million/s | 12 million/s |
| binary (no swap) | 9.2 million/s | 14 million/s |
| extended | 2.9 million/s | 7.8 million/s |
| binary ext. | 0.7 million/s | 2.9 million/s |
It may seem surprising that the extended Euclidean algorithm runs at the same speed as std::gcd on some systems, despite the fact that it appears to do more work. However, the computation of the Bézout coefficient along with the greatest common divisor is not a critical path, and can be folded in with the rest of the computation on a superscalar processor… so the result is expected.
As part of the preparation of this blog post, I had initially tried writing a C++ module. It worked quite well on my MacBook. However, it fell part under Linux with GCC, so I reverted it back. I was quite happy at how using modules made the code simpler, but it is not yet sufficiently portable.
Credit: Thanks to Harold Aptroot for a remark about the probability of two random integers being prime.
The Universe of Discourse: 3-coloring the vertices of an icosahedron
I don't know that I have a point about this, other than that it makes me sad.
A recent Math SE post (since deleted) asked:
How many different ways are there to color the vertices of the icosahedron with 3 colors such that no two adjacent vertices have the same color?
I would love to know what was going on here. Is this homework? Just someone idly wondering?
Because the interesting thing about this question is (assuming that the person knows what an icosahedron is, etc.) it should be solvable in sixty seconds by anyone who makes the least effort. If you don't already see it, you should try. Try what? Just take an icosahedron, color the vertices a little, see what happens. Here, I'll help you out, here's a view of part of the end of an icosahedron, although I left out most of it. Try to color it with 3 colors so that no two adjacent vertices have the same color, surely that will be no harder than coloring the whole icosahedron.
The explanation below is a little belabored, it's what OP would have discovered in seconds if they had actually tried the exercise.
Let's color the middle vertex, say blue.
The five vertices around the edge can't be blue, they must be the other two colors, say red and green, and the two colors must alternate:
Ooops, there's no color left for the fifth vertex.
The phrasing of the question, “how many” makes the problem sound harder than it is: the answer is zero because we can't even color half the icosahedron.
If OP had even tried, even a little bit, they could have discovered this. They didn't need to have had the bright idea of looking at a a partial icosahedron. They could have grabbed one of the pictures from Wikipedia and started coloring the vertices. They would have gotten stuck the same way. They didn't have to try starting in the middle of my diagram, starting at the edge works too: if the top vertex is blue, the three below it must be green-red-green, and then the bottom two are forced to be blue, which isn't allowed. If you just try it, you win immediately. The only way to lose is not to play.
Before the post was deleted I suggested in a comment “Give it a try, see what happens”. I genuinely hoped this might be helpful. I'll probably never know if it was.
Like I said, I would love to know what was going on here. I think maybe this person could have used a dose of Lower Mathematics.
Just now I wondered for the first time: what would it look like if I were to try to list the principles of Lower Mathematics? “Try it and see” is definitely in the list.
Then I thought: How To Solve It has that sort of list and something like “try it and see” is probably on it. So I took it off the shelf and found: “Draw a figure”, “If you cannot solve the proposed problem”, “Is it possible to satisfy the condition?”. I didn't find anything called “fuck around with it and see what you learn” but it is probably in there under a different name, I haven't read the book in a long time. To this important principle I would like to add “fuck around with it and maybe you will stumble across the answer by accident” as happened here.
Mathematics education is too much method, not enough heuristic.
MattCha's Blog: Complex Sweet Dry Storage: 1999 Mr Chen’s Daye ZhengShan MTF Special Order
Dry leaves have a sweet slight marsh peat odour to them.
Rinsed leaf has a leaf slight medicinal raison odour.
First infusion has a purfume medicinal fruity sweetness. There are notes of fig, cherries, longgan fruit nice complex onset with a were dry leaf base.
Second infusion has a woody slight purfume medical sweet cherry and fig taste. Nice dry storage base of slight mineral and leaf taste. Mouthfeel is a bit oily at first but slight silty underneath. There is a soft lingering sweetness returning of fruit with a woody base taste throughout. Slight warm chest with spacy head feeling.
Third infusion has a leafy woody maple syrup onset that gets a bit sweeter on return the sweetness is syrupy like stewed fruity with a leaf dry woody background that is throughout the profile. A more fruity pop of taste before some cool camphor on the breath. A silty almost dry mouthfeeling emerges after the initial slight oily syrup feeling. Slight warm chest and spacey mind slowing Qi.
Fourth infusion has a leaf medical onset with a slow emerging sweet taste that is quite sweet fruit on returning and sort of slowly builds up next to dry woody leaf and syrup medical taste. The cooled down infusion is a sweet creamy sweet syrupy. Spaced out Qi feeling.
5th infusion has a syrupy sweet woody medicinal creamy sweet with some fruity and maple syrup. Silty mouthfeel. Space out qi. The cooled down liquor is a woody maple sweet taste. Nice creamy almost fruity returning sweetness. Pear plum tastes underneath.
6th has a creamy oily watery sweetness with faint medicinal incense but mainly oily sweet taste. Fruity return with a slightly drier silty mouthfeel. Slight warming with nice space out Qi.
7th infusion has a woody pear leaf onset with an overall sweet pear oily onset.
8th has a soft pear woody leaf taste faint medicinal incense. Soft fading taste. Faint warmth and spacy mind.
9th has a mellow fruity sweetness with an oily texture and some incense medicinal mid taste. There is a woody leaf base. Mainly mild sweet no astringency or bitter. Oily watery mouthfeel.
10 this a long thermos steeping of the spent leaf.. it. Comes out oily and sweet with a strawberry sweetness subtle woody but mainly just fruity strawberry sweetness.
The overnight steeping is a sweet strawberry pure slight lubricating taste. Still sweet and lubricating. Very Yummy!
Peace
Tea Masters: Le Jinxuan 2024 annonce de bonnes récoltes de printemps
Avec une récolte le 28 mars, ce Jinxuan d'Alishan est à la fois précoce et particulièrement frais, car peu oxydé!La belle taille des feuilles du Jinxuan accentue l'impression de thé de haute montagne. Leur cueillette à la main est aussi ce qui explique la douceur de l'infusion. En effet, les Oolongs récoltés à la machine (en plaine) ont des saveurs plus astringentes du fait des coupures.
Les feuilles sont tendres et l'infusion ne devient pas amère, mais quand on la pousse plus fort que d'habitude.
Son prix est aussi particulièrement attractif. Non seulement, il n'augmente pas par rapport au Jinxuan de 2022, mais il est même un peu moins cher! Dans notre monde où l'inflation touche beaucoup les produits alimentaires, c'est important de le noter!
Ideas: The 2000 CBC Massey Lectures: The Rights Revolution by Michael Ignatieff
In his 2000 Massey Lectures on The Rights Revolution, Michael Ignatieff confronted the conflicted rise of human rights language in Canadian and global politics. "Has the rights revolution brought us closer together as a nation, or driven us further apart?" he asks in his final Massey lecture. We revisit this talk, as part of our series marking the 60th anniversary of Massey College.
new shelton wet/dry: whorearchy
96% of US hospital websites share visitor info with Meta, Google, data brokers. Could have been worse – last time researchers checked it was 98.6%
He went to the gate for the Delta flight to Austin, and used his phone to take pictures of the boarding passes of other passengers without their knowledge. He then boarded the aircraft using the barcode on another passenger’s boarding pass. […] he boarded and then tried to hide in the lavatory. The goal was to let everyone else board, and then take whatever empty seat was left. The problem is, there were no empty seats on the flight.
blinking does more than wet the eye, it also helps with vision
Students have submitted more than 22 million papers that may have used generative AI in the past year, new data released by plagiarism detection company Turnitin shows
Why Birds Survived, and Dinosaurs Went Extinct, After an Asteroid Hit Earth
CreativeApplications.Net: Filigree – Matt Deslauriers

Category: NFT
Tags: generative
People: Matt DesLauriers
CreativeApplications.Net: WÆVEFORM – Paul Prudence

Category: NFT
Tags: generative
People: Paul Prudence
Daniel Lemire's blog: A simple algorithm to compute the square root of an integer, byte by byte
A reader asked me for some help in computing (1 – sqrt(0.5)) to an arbitrary precision, from scratch. A simpler but equivalent problem is to compute the square root of an integer (e.g., 2). There are many sophisticated algorithms for such problems, but we want something relatively simple. We’d like to compute the square root bit by bit…
For example, the square root of two is…
- 5 / 4
- 11 / 8
- 22 / 16
- 45 / 32
- 90 / 64
- 181 / 128
- …
More practically, 8-bit by 8-bit, we may want to compute it byte by byte…
- 362 / 256
- 92681 / 65536
- 23726566 / 16777216
- …
How can we do so?
Intuitively, you could compute the integer part of the answer by starting with 0 and incrementing a counter like so:
x1 = 0 while (x1+1)**2 <= M: x1 += 1
Indeed, the square of the integer part cannot be larger than the desired power.
You can repeat the same idea with the fractional part… writing the answer as x1+x2/B+... smaller terms.
x2 = 0 while (x1*B + x2 + 1)**2 <= M*B**2: x2 += 1
It will work, but it involves squaring ever larger numbers. That is inefficient.
We don’t actually need to compute powers when iterating. If you need to compute x**2, (x+1)**2, (x+2)**2, etc. You can instead use a recursion: if you have computed (x+n)**2 and you need the next power, you just need to add 2(x+n) + 1 because that’s the value of (x+n+1)**2 – (x+n)**2.
Finally, we get the following routine (written in Python). I left the asserts in place to make the code easier to understand:
B = 2**8 # or any other basis like 2 or 10 x = 0 power = 0 limit = M for i in range(10): # 10 is the number of digits you want limit *= B**2 power *= B**2 x*=B while power + 2*x + 1 <= limit: power += 2*x + 1 x += 1 assert(x**2 == power) assert(x**2 <= limit) # x/B**10 is the desired root
You can simplify the code further by not turning the power variable into a local variable within the loop. We subtract it from the power variable.
B = 2**8 x = 0 limit = M for i in range(10): limit *= B**2 power = 0 x*=B while power + 2*x + 1 <= limit: power += 2*x + 1 x += 1 limit -= power # x/B**10 is the desired root
The algorithm could be further optimized if you needed more efficiency. Importantly, it is assumed that the basis is not too large otherwise another type of algorithm would be preferable. Using 256 is fine, however.
Obviously, one can design a faster algorithm, but this one has the advantage of being nearly trivial.
Further reading: A Spigot-Algorithm for Square-Roots: Explained and Extended by Mayer Goldberg
Credit: Thanks to David Smith for inspiring this blog post.
new shelton wet/dry: O.J. grabbed Nicole’s crotch and said, ‘This is where babies come from and this belongs to me.’

Kardashian and Simpson first met around 1967 while both of them were at USC and became close friends. Simpson was the best man at Kardashian and Kris Houghton’s wedding in 1978. He had four children with his first wife, Kris Kardashian: Kourtney, Kim, Khloé, and Rob.
Following the June 12, 1994, murder of Nicole Brown Simpson and Ronald Goldman, Simpson stayed in Kardashian’s house to avoid the media. Kardashian was the man seen carrying Simpson’s garment bag the day that Simpson flew back from Chicago. Prosecutors speculated that the bag may have contained Simpson’s bloody clothes or the murder weapon.
Simpson was charged with the murders and subsequently acquitted of all criminal charges in a controversial criminal trial.
Kardashian had let his license to practice law become inactive before the Simpson case but reactivated it to aid in Simpson’s defense as a volunteer assistant on his legal team, alongside Simpson’s main defense attorneys, Robert Shapiro and Johnnie Cochran.
As one of Simpson’s lawyers and a member of the defense “Dream Team”, Kardashian could not be compelled or subpoenaed to testify against Simpson in the case, which included Simpson’s past history and behavior with his ex-wife Nicole, and as to the contents of Simpson’s garment bag. He sat by Simpson throughout the trial.
video { CNN’s coverage of O.J. Simpson’s infamous white Bronco chase in 1994 }
new shelton wet/dry: corn in your gas tank
Polish priest jailed for throwing wild orgy where male prostitute died after overdosing on erectile dysfunction pills. In a similar incident, an Italian priest was sentenced to three years in prison in late 2021 for stealing nearly $120K from the church to buy drugs for gay sex parties he hosted.
Esketamine injection just after childbirth reduces depression in new mothers
Ketamine is a dissociative anesthetic approved in the United States for inducing and maintaining anesthesia via intravenous infusion or intramuscular injection. It is not indicated for major depressive disorder (MDD) or TRD, although it is frequently used off-label for these indications. Esketamine, the (S) enantiomer of racemic ketamine, is FDA-approved for adults with TRD and adults with MDD with suicidal thoughts or actions in combination with an oral antidepressant. […] The United States has experienced a rapid proliferation of ketamine clinics to treat depression that operate with little, to no, regulation. Some clinics are now prescribing ketamine lozenges that patients take at home.
How Hackers Can Hijack Two-factor authentication Calls with Sneaky Call Forwarding
Amazon, Microsoft, and Google are the biggest winners of government contracts, according to a report from Tussel. Amazon hosts the data of the National Security Agency with a $10 billion contract, and gets hundreds of millions from other governments. […] In 2023, the US Department of Defense awarded the Joint Warfighter Cloud Capability contract to Microsoft, Amazon, Google, and Oracle. The contract is worth up to $9 billion and provides the Department of Defense with cloud services. […] Most people still think of tech companies as free-enterprise rebels. It’s not true. […] In this framework, we might also tag the agricultural sector, which is dominated by cartels that have driven out family farms. It’s a government plan and massive subsidies that determine what is produced and in what quantity. It’s not because of consumers that your Coke is filled with a scary product called “high fructose corn syrup,” why your candy bar and danish have the same, and why there is corn in your gas tank. This is entirely the product of government agencies and budgets.
A Reading List on Fermentation — Somewhere in the grey zone between science and magic, the controlled addition of bacteria to food transforms it — mostly to our delight. Here are five pieces exploring these transitions (and their products).
new shelton wet/dry: ‘This is civilization. We have inherited it. We love the glitter. It is growing dark and trees crowd the sky.’ –Susan Griffin

Press reports in April 2019 and December 2021 stated that China might be developing a YJ-18 launcher that can be packaged inside a standard commercial shipping container

Tea Masters: Puerh comparison: Purple Da Yi from 2003 vs '7542' Menghai from 1999
What I found interesting is that the color of the cakes shows the 2003 Da Yi to be darker or redder than the 1999 cake. It's strange that a younger cake would look darker.
However, the colors of the brews is much more in line with what one would expect:
And now, surprise, the spent leaves of the Da Yi look greener!What about scents and taste?
The scent profile has similarities, which suggest a continuity in the 7542 recipe that has helped establish the fame of Menghai/Da Yi. But the tobacco/leather scent is absent from the 2003 brew. This is a scent that is typical of the traditional CNNP era. And while it's still present, and nicely balanced, in the 1999 brew, it has disappeared from the 2003.
Conclusion: The customer who inspired this comparison wrote to me that "there are many fake puerhs, especially Da Yi". So, buyers beware, especially with the high-end aged puerh. My recommendation is to get more experience by tasting samples and making similar comparisons!
Tea Masters: Les boissons et leur signification dans l'Iliade de Homère
Homère ne parle pas de thé dans l'Iliade. C'est normal, puisqu'on date son œuvre du huitième ou septième siècle avant JC, et que le thé n'a vraiment pris son essor en Chine que sous les Tang au huitième siècle après JC, et qu'il faudra encore près de mille ans pour qu'il arrive en Europe. Mais j'ai relevé 55 mentions d'un autre breuvage dans cet ouvrage. Or, dans la culture chinoise, le thé lui est souvent substitué, à tel point qu'on le servait dans les mêmes coupes chez les Tang. L'étude de cette boisson chez Homère peut probablement nous éclairé sur la fonction symbolique de cette boisson ou du thé dans une culture plus ancienne et archaïque. Il s'agit du 'vin', mentionné directement 37 fois. Homère en parle aussi indirectement avec les 'libations' (8 mentions), les coupes (9 mentions) et l'ambroisie (2 mentions).
Voici quelques passages représentatifs:
1. Chant I, Vers 470: "Lors donc qu'on a chassé la soif et l'appétit, les jeunes gens remplissent jusqu'au bord les cratères, puis à chacun, dans sa coupe, ils versent de quoi faire libation aux dieux. Et, tout le jour, en chœur, les fils des Achéens, pour apaiser le dieu, chantent le beau péan et célèbrent le Préservateur."
Commentaire: Le mot 'cratère' revient souvent dans le texte et il convient de définir ce qui est un objet chez les Grecs (et non la trace de l'impact d'un objet tombé sur le sol). Le cratère est large bol, souvent métallique, dans lequel on mélange le vin et l'eau. Il est plus qu'intéressant de noter que ce mélange a lieu dans un cadre religieux, après avoir chassé la soif et pour rendre hommage à Apollon (le Préservateur). Pourquoi mélangeait-on le vin à l'eau chez les Grecs? Mes recherches proposent plusieurs raisons:
a. Ce serait pour désinfecter l'eau ou la rendre plus agréable à boire. Dans ce contexte religieux, cette explication ne tient pas debout. Les jeunes gens ne boivent pas par soif, mais pour exécuter un rite.
b. Une autre explication dit simplement que boire du vin non dilué serait 'barbare', c'est-à-dire non civilisé. Cette explication va dans le sens de Nietzsche qui fait une distinction entre Dionysos, le dieu du vin et de l'ivresse et Apollon qui représente l'ordre et la raison. Faire un mélange des deux, c'est essayer de concilier ces deux pôles antagonistes. Mais l'éclairage de René Girard est probablement encore plus parlant. En effet, dans mes derniers articles, j'ai montré comment, selon Girard, la violence et le sacré sont liés. Le fait religieux est la tentative archaïque de l'homme de canaliser la violence qui nait lors des crises de désir mimétique. Or, il est très facile de comprendre que des fortes doses de vin ont souvent provoqué des bagarres parmi les hommes ivres dans l'antiquité. En désinhibant les désirs, le vin peut servir de catalyseur aux crises. Le vin est donc dangereux, 'barbare' et la solution est que la religion s'en empare pour mieux réguler son emploi (de préférence quand on n'a plus soif) et d'abaisser son degré d'alcoolémie en le mélangeant avec de l'eau!
2.et 3. Chant I, Vers 584 et 593: "il (Héphaestos) met la coupe à deux anses aux mains de sa mère (Héré)" (...) "elle reçoit la coupe que lui offre son fils. Lui, cependant, à tous les autres dieux, va sur sa droite versant le doux nectar, qu'il puise dans le cratère."Commentaire: Dans ce passage, les dieux agissent comme les hommes avec le vin. Eux aussi mélangent leur nectar et le boivent en fin de banquet. Il y a à la fois "brusquement un rire inextinguible (qui) jaillit parmi les Bienheureux" qui fait penser à l'ivresse dionysiaque, mais aussi un bonheur raffiné, civilisé où 'leur cœur n'a pas à se plaindre du repas (...) ni de la cithare, superbe, que tiennent les mains d'Apollon, ni des Muses, dont les belles voix résonnent en chants alternés."
La grille de lecture girardienne nous permet de remarquer une imitation mimétique entre hommes et dieux. Pour donner envie aux hommes de se comporter de manière civilisée, le récit leur montre une telle scène chez les dieux afin de stimuler leur désir d'imitation.
4. Chant II, vers 342 "Au feu alors tous les desseins, tous les projets des hommes, et le vin pur des libations, et les mains qui se sont serrées, tout ce en quoi nous avions foi!"
Commentaire: Le vin est clairement sacralisé dans ce passage. Son importance ne provient pas du plaisir qu'on en tire, mais de sa fonction lors des cérémonies d'offrandes aux dieux. En théorie, la libation consiste à répandre un liquide (huile ou vin) à l'intention d'une divinité. Dans des temps plus reculés, le liquide de la discorde, le vin, était certainement répandu par terre afin d'empêcher l'ivresse des hommes. D'ailleurs, certaines religions ont effectivement décrété le vin et tout alcool comme interdits. Le mélange avec de l'eau par les Grecs fut une approche plus pragmatique pour relâcher la pression sur l'interdit.
On remarquera aussi le lien entre le symbole de non-violence que sont des mains serrées et le sacré des libations. Le vin sacré est lié à la paix.
5. Chant III, vers 246: "Les hérauts cependant portent par la ville ce qui doit servir au pacte royal, deux agneaux, et, dans une outre de peau de chèvre, le vin joyeux, fruit de la terre. Le héraut Idée porte, lui, un brillant cratère, ainsi que des coupes d'or."
Commentaire: L'adjectif 'joyeux' rappelle la face dionysiaque du vin. Ici, ce pacte doit permettre de trouver une solution au conflit entre les Grecs et les Troyens. De causeur de troubles, le vin devient faiseur de paix par l'intermédiaire du religieux. Quant aux agneaux, ils remplacent les sacrifices humains. Leur chair étant particulièrement succulente, elle devait être l'objet de convoitise et de rivalités. C'est probablement pourquoi l'agneau peut remplir cette fonction sacrificielle, comme le vin, à mon avis, en appliquant une analyse girardienne.
6. Chant III, vers 270: "Ils (les hérauts) font dans le cratère le mélange du vin, et ils versent l'eau sur les mains des rois."
Commentaire: La suite du texte nous décrit en détail la cérémonie qui scelle ce pacte lors duquel les agneaux sont tués. Toute cette cérémonie a pour but de faire respecter la parole donnée en y associant les dieux. "Châtiez les parjures à un pacte" est l'injonction aux dieux. C'est encore plus explicite dans la prochaine citation.
7. Chant III, vers 298: ""Ô Zeus, très glorieux, très grand! et vous tous, dieux immortels ! quel que soit celui des deux peuples qui le premier viole ce pacte, tout comme je répands ce vin, que soit répandue à terre la cervelle de tous les siens, pères et enfants, tandis que leurs femmes subiront un maître étranger!""
Commentaire: Pour cette cérémonie solennelle, la libation consiste bien à répandre le vin par terre et non à le consommer. Mais l'histoire de l'Iliade montrera que ce pacte sera rompu, mais par la faute d'une déesse, Aphrodite. Or, les dieux ne sont pas tenus par les pactes des hommes...
8. Chant IV, vers 48: "Jamais mon autel n'y manque d'un repas où tous ont leur part, des libations ni du fumet de graisse qui sont notre apanage à tous."
Commentaire: Zeus explique à Héré qu'il n'a pas de raison d'en vouloir aux Troyens, car ils l'honorent comme il se doit avec repas, vin et graisse. Ce récit incitait les Grecs à la piété et aux respect des rites envers les dieux afin d'obtenir leurs faveurs.
9. Chant IV, vers 158: "Non, le pacte juré n'est pas encore réduit à rien, pas plus que le sang des agneaux, le vin pur des libations, les mains qui se sont serrées, tout ce en quoi nous avions foi!"
Commentaire: Cette phrase fait référence au pacte royal du chant III. Pour Agamemnon, les Troyens sont les bénéficiaires actuels du pacte rompu, mais ils devront en payer le prix ultime et leur défaite est quasi certaine, même si la guerre durera encore longtemps!
10. Chant IV, vers 257: "Idoménée, il n'est personne que je prise autant que toi, parmi les Danaens aux prompts coursiers, que ce soit à la guerre ou à toute autre tâche - ou même au festin, quand les chefs argiens mélangent dans les cratères un vin d'honneur aux sombres feux. Alors, si tous les autres Achéens chevelus boivent la part qui leur est faite, ta coupe à toi, comme ma propre coupe, est toujours tenue pleine, de façon que tu puisses boire aussi souvent que ton cœur t'y invite."
Commentaire: Dans ce passage, il n'est pas question de libations, mais de vin consommé lors d'un festin. Il est intéressant de noter que ce sont les chefs qui officient au mélange du vin et de l'eau dans les cratères. Le vin n'est donc pas une boisson comme une autre, même quand elle est simplement bue lors d'un festin. De plus, les chefs distribuent à chaque homme la part qui lui revient, mais les plus méritants ont droit à plus. C'est au chef qu'incombe la responsabilité du partage au mérite.
11. Chant IV, vers 347: ""Vous avez plaisir à manger des viandes rôties et à vider des coupes de vin délicieux, tout autant que vous en voulez: et maintenant vous verriez volontiers dix colonnes achéennes passer devant vous, pour aller se battre, le bronze implacable à la main!""
Commentaire: Agamemnon utilise l'adjectif 'délicieux' de manière ironique. Il accuse Ménesthée et Ulysse de s'adonner aux plaisirs de la table et d'en négliger leurs devoirs guerriers. En insistant sur le fait qu'eux peuvent boire autant qu'ils le veulent, ce qui n'est pas le cas des soldats ordinaires (cf. note précédente), Agamemnon veut mettre le peuple de son côté en suscitant la jalousie, puisque les soldats ont le désir mimétique de pouvoir boire autant que les héros.
12. Chant V, vers 342: "c'est l''ichôr', tel qu'il coule aux veines des divinités bienheureuses, ne mangeant pas le pain, ne buvant pas le vin aux sombres feux, elles n'ont point de sang et sont appelées immortelles.
Commentaire: Ce passage semble en contradiction avec les mentions 2 et 3 où les dieux boivent également une boisson puisée dans un cratère et dont les effets sont les mêmes que le vin pour les hommes. Or, une relecture attentive nous permet de comprendre la subtilité lexicale des Grecs. En effet, si les dieux ne boivent pas de vin (comme les mortels), ils boivent un 'nectar' qu'on appelle aussi 'ambroisie'. C'est cela qui permet à Homère de dire que les Grâces ne boivent pas de vin.
13. Chant V, vers 772: "Autant d'espace brumeux se laisse embrasser du regard par l'homme assis sur une guette qui surveille une mer aux teintes de lie de vin".
Analyse: Nous avions déjà vu Au Bord de l'Eau que le thé pouvait aider à définir une couleur. Homère utilise ce même procédé pour décrire la couleur inhabituelle de la mer.
14. Chant VIII, vers 185: "Xanthe, Podarge, Ethon, et toi, divin Lampos, voici l'heure venue de me revaloir ces soins qu'à maintes reprises vous a prodigués Andromaque, la fille du magnanime Eétion, en vous servant le doux froment, en mélangeant pour vous le vin, quand votre cœur vous invitait à boire, cela avant de me servir moi-même, moi qui me flatte d'être son jeune et bel époux."
Commentaire: Même entre amis, le vin tient une place importante dans ces attentions qu'on peut prodiguer. De plus, l'aspect cérémonial ne disparait pas. Non seulement c'est Andromaque qui mélange le vin, mais Hector, son mari lui demande de servir ses amis avant lui, ce qui est une grande marque de politesse venant de la part du fils du roi Priam.
15. Chant VIII, vers 229: "Où sont donc allées vos vantardises? Nous étions preux, à nous croire, quand, à Lemnos, vous nous décerniez de vaines louanges, tout en mangeant force filets de bœufs aux cornes droites, en vidant des cratères remplis de vin à pleins bords."
Commentaire: Agamemnon s'emploie à motiver ses troupes pour le combat. Il commence par piquer leur amour propre en leur rappelant qu'ils s'étaient tous vanter de ne faire qu'une bouchée des Troyens lors des dîners avant leur départ. On pourrait y voir une critique du vin, bu à profusion, qui vous fait dire des choses qu'on ne pense pas vraiment. Mais pour Agamemnon, au contraire, ces paroles publiques engageaient chaque convive. In vino veritas diront les Romains. Le vin n'est pas une excuse pour mentir, mais doit être un moyen de sceller un engagement, selon Agamemnon.
16 et 17. Chant VIII, vers 506 et vers 538: "Et munissez-vous aussi de doux vin, et de pains pris dans vos maisons.(...) Ils amènent de la ville des bœufs et de gros moutons - vite ; ils se munissent de doux vin et de pain pris dans leurs maisons"
Commentaire: Pour passer la nuit et garder la plaine après une journée de combats, Hector demande à ses soldats de préparer le repas du soir. Le vin est une récompense et un réconfort incontournable pour les combattants Troyens.
17. Chant IX, vers 175: "Sans tarder, les hérauts versent l'eau sur les mains ; les jeunes gens remplissent jusqu'aux bords les cratères ; puis à chacun dans sa coupe, ils versent de quoi faire libation aux dieux. Les libations finies et la soif satisfaite, les envoyés sortent de la baraque d'Agamemnon, le fils d'Atrée."
Commentaire: On retrouve ici le même rite qu'à la mention #6. On apprend cette fois-ci que lors de cette libation, le vin est bu au lieu d'être répandu par terre (contrairement à la mention #7 qui semble donc être une version plus ancienne ou plus formelle qu'ici.)
18. Chant IX, vers 202: (Achille dit:) "Dispose un plus grand cratère, fils de Ménœtios, et fais un mélange plus fort ; prépare ensuite des coupes pour chacun : ce sont des amis très chers qui aujourd'hui sont sous mon toit."
Commentaire: Achille est le plus fort guerrier dans cette guerre. Il n'est pas étonnant qu'il tienne particulièrement bien l'alcool. Ce passage confirme que le mélange du vin avec de l'eau n'était pas fait selon un ratio constant, mais qu'il était adapté aux circonstances et aux personnes invitées.
19. Chant IX, vers 470 et 490:"force vin se buvait, pris aux caves du vieux (....) il fallait alors que je te prisse sur mes genoux, pour te couper la viande, t'en gaver, t'approcher le vin des lèvres. Et que de fois tu as trempé le devant de ma tunique, en le recrachant, ce vin!"
Commentaire: Le tuteur d'Achille nous révèle cette anecdote sur l'enfance du héros. Elle explique, peut-être, pourquoi Achille tient si bien l'alcool: car il en buvait déjà, enfant!
20. Chant IX, vers 656: "Il dit ; eux, tour à tour, prennent la coupe à deux anses, pour offrir leurs libations, puis s'en vont le long des nefs."
Commentaire: Tout comme à la mention #2, la coupe a deux anses. Or, la première coupe à 2 anses était celle des dieux. Dans ce passage, c'est la coupe qu'Achille passe aux autres héros, Ajax et Ulysse. Cela peut suggérer que ces héros sont presque des dieux, mais les deux passages sont trop éloignés l'un de l'autre pour que l'auditeur moyen fasse le rapprochement. L'explication plus logique était que les coupes à deux anses étaient le style le plus fréquent. Or, si l'on considère les cérémonies religieuses comme des moyens pour canaliser et réduire la violence (selon Girard), alors 2 anses sont logiques. En effet, ces deux anses obligent de tenir la coupe avec les deux mains. Cela empêche de garder une arme cachée dans une main (placée derrière le dos, par exemple). Faire les gestes de cérémonie avec deux mains visibles est une manière de se montrer inoffensif et paisible.
21. Chant IX, vers 705: "Pour l'heure, allez dormir ; vos cœurs ont pu se satisfaire de pain, de vin ; là sont la fougue et la vaillance."
Commentaire: La complémentarité du pain et du vin remonte est bien plus ancienne que la Cène de Jésus et des apôtres la veille de sa crucifixion.
22. Chant X, vers 579: "Après quoi, bien baignés, largement oints d'huile, ils s'assoient pour dîner, et puisant au cratère plein, ils offrent à Athéné des libations de doux vin.
Commentaire: Ici, la libation fait partie du repas. Elle nous fait penser au 'loyal toast', cette tradition britannique toujours en vogue qui consiste à offrir le premier toast des repas officiels, avant le dessert, à la santé du monarque.
Note: le premier Oolong de haute montagne (Alishan) du printemps 2024 est disponible ici!Michael Geist: AI Spending is Not an AI Strategy: Why the Government’s Artificial Intelligence Plan Avoids the Hard Governance Questions

The government announced plans over the weekend to spend billions of dollars to support artificial intelligence. Billed as “securing Canada’s AI Advantage”, the plan includes promises to spend $2 billion on an AI Compute Access Fund and a Canadian AI Sovereign Compute Strategy that is focused on developing domestic computing infrastructure. In addition, there is $200 million for AI startups, $100 million for AI adoption, $50 million for skills training (particularly those in the creative sector), $50 million for an AI Safety Institute, and $5.1 million to support the Office of the AI and Data Commissioner, which would be created by Bill C-27. While the plan received unsurprising applause from AI institutes that have been lobbying for the money, I have my doubts. There is unquestionably a need to address AI policy, but this approach appears to paper over hard questions about AI governance and regulation. The money may be useful – though given the massive private sector investment in the space right now a better case for public money is needed – but tossing millions at each issue is not the equivalent of grappling with AI safety, copyright or regulatory challenges.
The $2 billion on compute infrastructure is obviously the biggest ticket item. Reminiscent of past initiatives to support connectivity in Canada, there may well be a role for government here. However, the private sector is already spending massive sums globally with estimates of $200 billion on AI by next year, leaving doubts about whether there is a private sector spending gap that necessitates government money. If so, government needs to make the case. Meanwhile, the $300 million for AI startups and adoption has the feel of the government’s failed $4 billion Digital Adoption Program with vague policy objectives and similar doubts about need.
But it is the smallest spending programs that may actually be the most troubling as each appear to rely on spending instead of actual policy. The $50 million for creative workers – seemingly more money for Canadian Heritage to dole out – is premised on the notion that the answer to the disruption from AI is skills development. In the context of the creative sector, it is not. Rather, there are hard questions about the use and outputs of copyrighted works by generative AI systems. I’m not convinced that this requires immediate legislative reform given that these issues are currently before the courts, but the solution will not be found in more government spending. There is a similar story with the $50 million for the AI Safety Institute, which absent actual legislation will have no power or significant influence on global AI developments. It is the sort of thing you create when you want to be seen to be doing something, but are not entirely sure what to do.
Most troubling may the smallest allocation of $5.1 million for the Office of the AI and Data Commissioner. First, this office does not exist as it would only be formed if Bill C-27 becomes law. That bill is still stuck in committee after the government instead prioritized Bills C-11 and C-18, letting the privacy and AI bill languish for a year before it began to move in the House of Commons. It could become law in 2025, though there remains considerable opposition to the AI provisions in the bill, which received little advance consultation. Second, $5.1 million is not a serious number for creating a true enforcement agency for the legislation. In fact, the Office of the Privacy Commissioner of Canada estimates it alone needs an additional $25 million. Third, backing enforcement (however meagrely) places the spotlight on the juxtaposition of providing billions in new AI funding while pursuing AI regulation in Bill C-27. Major tech companies have warned that the bill is too vague and costly, mirroring the opposition in Europe, where both France and Germany sought to water down legislation when it became apparent the proposed rules would undermine their domestic AI industries. These are hard legislative choices that have enormous economic and social consequences with government forced to ask to how balance competing objectives and consider which will matter more to AI companies: Canadian government spending or the cost of regulation?
Canada wants to be seen as a global AI leader consistent with its early contributions to the field. But the emerging AI plan sends mixed signals with billions in government spending, legislation that may discourage private sector investment, and avoidance of the hard governance issues. That isn’t a strategy and it isn’t likely to secure an AI advantage.
The post AI Spending is Not an AI Strategy: Why the Government’s Artificial Intelligence Plan Avoids the Hard Governance Questions appeared first on Michael Geist.
OCaml Weekly News: OCaml Weekly News, 09 Apr 2024
- moonpool 0.6
- sqids 0.1.0
- OCaml Retreat at Auroville, India (March 10th - March 15th)
- Miou, a simple scheduler for OCaml 5
- OCaml.org Newsletter: March 2024
- Opam 102: Pinning Packages, by OCamlPro
- dune 3.15
- Ocsigen: summary of recent releases
- Js_of_ocaml 5.7
- Eio Developer Meetings
- Ocaml developer at Routine, Paris
- dream-html 3.0.0
- Other OCaml News
Jesse Moynihan: Tarot Cards are gone
Charles Petzold: Interactive Graphical Arithmetic
CreativeApplications.Net: Spectron – Simon De Mai

Category: NFT
Tags: video
People: Simon De Mai
CreativeApplications.Net: Event Horizon – Kim Asendorf

Category: NFT
Tags: generative
People: Kim Asendorf
Michael Geist: The Law Bytes Podcast, Episode 198: Richard Moon on the Return of the Section 13 Hate Speech Provision in the Online Harms Act

The public debate surrounding Bill C-63, the Online Harms Act, has focused primarily on Human Rights Act and Criminal Code reforms. The Human Rights Act changes include the return of Section 13 on hate speech, which was repealed by the Harper government after criticisms that it unduly chilled freedom of expression. To help understand the history of Section 13 and its latest iteration, this week Professor Richard Moon, Distinguished University Professor and Professor of Law at the University of Windsor joins the Law Bytes podcast. The Canadian Human Rights Commission asked Professor Moon to conduct a study on Section 13 in 2008 and his report is the leading source on its history and application. In this episode, we discuss that history and consider the benefits and risks of inserting it into Bill C-63.
The podcast can be downloaded here, accessed on YouTube, and is embedded below. Subscribe to the podcast via Apple Podcast, Google Play, Spotify or the RSS feed. Updates on the podcast on Twitter at @Lawbytespod.
Credits:
Brent Rathgeber, MP Discussing Section 13 of the Canada Human Rights Act
The post The Law Bytes Podcast, Episode 198: Richard Moon on the Return of the Section 13 Hate Speech Provision in the Online Harms Act appeared first on Michael Geist.
The Shape of Code: Software companies in the UK
How many software companies are there in the UK, and where are they concentrated?
This question begs the question of what kinds of organization should be counted as a software company. My answer to this question is driven by the available data. Companies House is the executive agency of the British Government that maintains the register of UK companies, and basic information on 5,562,234 live companies is freely available.
The Companies House data does not include all software companies. A very small company (e.g., one or two people) might decide to save on costs and paperwork by forming a partnership (companies registered at Companies House are required to file audited accounts, once a year).
When registering, companies have to specify the business domain in which they operate by selecting the appropriate Standard Industrial Classification (SIC) code, e.g., Section J: INFORMATION AND COMMUNICATION, Division 62: Computer programming, consultancy and related activities, Class 62.01: Computer programming activities, Sub-class 62.01/2: Business and domestic software development. A company’s SIC code can change over time, as the business evolves.
Searching the description associated with each SIC code, I selected the following list of SIC codes for companies likely to be considered a ‘software company’:
62011 Ready-made interactive leisure and entertainment
software development
62012 Business and domestic software development
62020 Information technology consultancy activities
62030 Computer facilities management activities
62090 Other information technology service activities
63110 Data processing, hosting and related activities
63120 Web portals
There are 287,165 companies having one of these seven SIC codes (out of the 1,161 SIC codes currently used); 5.2% of all currently live companies. The breakdown is:
All 62011 62012 62020 62030 62090 63110 63120
5,562,234 7,217 68,834 134,461 3,457 57,132 7,839 8,225
100% 0.15% 1.2% 2.4% 0.06% 1.0% 0.14% 0.15%
Only one kind of software company (SIC 62020) appears in the top ten of company SIC codes appearing in the data:
Rank SIC Companies
1 68209 232,089 Other letting and operating of own or leased real estate
2 82990 213,054 Other business support service activities n.e.c.
3 70229 211,452 Management consultancy activities other than financial management
4 68100 194,840 Buying and selling of own real estate
5 47910 165,227 Retail sale via mail order houses or via Internet
6 96090 134,992 Other service activities n.e.c.
7 62020 134,461 Information technology consultancy activities
8 99999 130,176 Dormant Company
9 98000 118,433 Residents property management
10 41100 117,264 Development of building projects
Is the main business of a company reflected in its registered SIC code?
Perhaps a company started out mostly selling hardware with a little software, registered the appropriate non-software SIC code, but over time there was a shift to most of the income being derived from software (or the process ran in reverse). How likely is it that the SIC code will change to reflect the change of dominant income stream? I have no idea.
A feature of working as an individual contractor in the UK is that there were/are tax benefits to setting up a company, say A Ltd, and be employed by this company which invoices the company, say B Ltd, where the work is actually performed (rather than have the individual invoice B Ltd directly). IR35 is the tax legislation dealing with so-called ‘disguised’ employees (individuals who work like payroll staff, but operate and provide services via their own limited company). The effect of this practice is that what appears to be a software company in the Companies House data is actually a person attempting to be tax efficient. Unfortunately, the bulk downloadable data does not include information that might be used to filter out these cases (e.g., number of employees).
Are software companies concentrated in particular locations?
The data includes a registered address for each company. This address may be the primary business location, or its headquarters, or the location of accountants/lawyers working for the business, or a P.O. Box address. The latitude/longitude of the center of each address postcode is available. The first half of the current postcode, known as the outcode, divides the country into 2,951 areas; these outcode areas are the bins I used to count companies.
Are there areas where the probability of a company being a software company is much higher than the national average (5.265%)? The plot below shows a heat map of outcode areas having a higher than average percentage of software companies (36 out of 2,277 outcodes were at least a factor of two greater than the national average; BH7 is top with 5.9 times more companies, then RG6 with 3.7 times, BH21 with 3.6); outcodes having fewer than 10 software companies were excluded (red is highest, green lowest; code+data):
The higher concentrations are centered around the country’s traditional industrial towns and cities, with a cluster sprawling out from London. Cambridge is often cited as a high-tech region, but its highest outcode, CB4, is ranked 39th, at twice the national average (presumably the local high-tech is primarily non-software oriented).
Which outcode areas contain the most software companies? The following list shows the top ten outcodes, by number of registered companies (only BN3 and CF14 are outside London):
Rank Outcode Software companies
1 WC2H 10,860
2 EC1V 7,449
3 N1 6,244
4 EC2A 3,705
5 W1W 3,205
6 BN3 2,410
7 CF14 2,326
8 WC1N 2,223
9 E14 2,192
10 SW19 1,516
I’m surprised to see west-central London with so many software companies. Perhaps these companies are registered at their accountants/lawyers, or they are highly paid contractors who earn enough to afford accommodation in WC2. East-central London is the location of nearly all the computer companies I know in London.
Daniel Lemire's blog: C++ web app with Crow: early scalability results
Last year, I looked at writing small “hello world” web applications in various programming languages (Go, JavaScript, Nim…). Go, using nothing but the standard library, did well.
In these benchmarks, I am just programming an HTTP route that returns a small string (e.g., ‘hello world’). The query is from the host itself. The intent behind such a benchmark is to measure how well an web application might scale in the best of cases. I call such a benchmark ‘simplistic’ because nobody only ever returns just a short string and you do not usually query the server from the host.
At the time, I had wanted to compare with a C++ library, and I ended up trying the lithium framework which scaled very well.
Jake Arkinstall pointed out that he uses Crow, to build web applications in C++. So I decided to take Crow out on a spin.
My simplistic application has only few lines:
#include "crow.h" int main() { crow::SimpleApp app; app.loglevel(crow::LogLevel::Warning); CROW_ROUTE(app, "/simple")([](){ return "Hello world"; }); app.port(18080).multithreaded().run(); }
This allows the server to use all threads. You can limit the server to fewer threads by replacing multithreaded() by concurrency(32) to limit (e.g.) the server to 32 threads.
To build it, I use a standard CMakeLists.txt file:
cmake_minimum_required(VERSION 3.15) project(funserver CXX) find_package(Crow REQUIRED) add_executable(server src/server.cpp) target_link_libraries(server Crow::Crow)
And I use a conan file to specify the dependency:
[requires] crowcpp-crow/1.1.0 [generators] CMakeDeps CMakeToolchain
That is all. Then to build, I issue the following commands in shell:
conan profile detect --force conan install . --output-folder=build --build=missing cmake -B build -DCMAKE_TOOLCHAIN_FILE=conan_toolchain.cmake -DCMAKE_BUILD_TYPE=Release cmake --build build ./build/server
I assumes that you have C++ compiler, Conan and CMake, but these are standard tools.
After issuing these commands, my server is then running. I use bombardier to hammer the server with requests. On a Linux server with many processors (two Intel Xeon Gold 6338 CPUs, each made of 32 cores) and much memory, I try increasing the number of simultaneous requests (using the tool bombardier) and looking for errors. As the number of simultaneous queries increase, the system has to sustain both a high number of requests and as well as the processing of the server. You can run my benchmark from my source code and instructions. Your numbers will differ.
| simultaneous queries | requests/s | errors (%) |
|---|---|---|
| 10 | 260k | 0% |
| 100 | 315k | 0% |
| 1000 | 380k | 0% |
| 10,000 | 350k | 0.002% |
I filed an issue with the Crow project regarding the errors. They are very uncommon and only occur under intense stress. They may or may not be the result of a bug.
My performance numbers are comparable to a lithium server. Let us rerun the same tests with lithium using 64 threads to verify:
| simultaneous queries | requests/s | errors (%) |
|---|---|---|
| 10 | 90k | 0% |
| 100 | 245k | 0% |
| 1000 | 275k | 0% |
| 10,000 | 240k | 0% |
Though lithium does not cause any errors even at high queries, it has troubles shutting down after being stressed with 10,000 simultaneous queries.
So it seems that Crow offers state-of-the-art performance. Crow offers HTTP/1.1 and WebSocket support, but it has currently no support for the more recent standards. It has a nice Web site.
Appendix. Andrew Johnston invited me to compare these results with a similar server written using Bun, the fast JavaScript runtime. I use the following program.
Bun.serve({ fetch (req) { const url = new URL(req.url); if (url.pathname === "/simple") return new Response("Hello world!"); return new Response('Should return an error!') }, port: Number(Bun.env.PORT || 3000), address: Bun.env.ADDRESS || '127.0.0.1' })
I deliberately do not use multi processes or other tuning. Using the same hardware, and the same test setup, I get the following results with Bun (results will vary):
| simultaneous queries | requests/s | errors (%) |
|---|---|---|
| 10 | 48k | 0% |
| 100 | 53k | 0% |
| 1000 | 54k | 0% |
| 10,000 | 47k | 0% |
The command ps huH p processid |wc -l reveals that it uses about 10 threads, but according to the author of Bun, Jarred Sumner, the server is single threaded. I made a video to illustrate the thread usage. The additional threads are used to by the garbage collector, to recover memory.
In any case, Bun is between 6 to 8 times slower than a pure C++ server written with Crow, in my tests. Your results will vary.
I found it interesting that Bun never caused error, even under stress. The reason is likely that the Bun server never uses many threads, so the system is less likely to be under stress.
Please note that I am not encouraging you to use Crow instead of Bun. I am definitively encouraging you to check Bun out.
s mazuk: online communities are so strange because people slip away so easily. you can be on here for years,…
online communities are so strange because people slip away so easily. you can be on here for years, folding people you’ve never met into the fabric of your daily life, and then they disappear, leaving only ghost posts scattered across tumblr behind. or their blog stays dormant, for weeks, months, years, until you’re only still following them because you remember that they love sunflowers or they were kind to you when they didn’t have to be or the last thing they posted was sad and raw and you still worry about them sometimes.
and sometimes they come back when you least expect it, years later, even, and there’s this sudden rush of relief like there you are, there you are, even though you barely knew each other.
there’s a strange kind of love to it. i don’t know you and i want to hold your hand across miles and time zones and oceans. i can still see the imprint of you in this community you left. you don’t anyone will notice or care when you’re gone, but we notice and we care and we wish you well.
i hope you’re all okay out there. i hope the sun is shining on your face and you are breathing deeply. i miss you.
things magazine: A round-up of things from here and there
Planet Lisp: Joe Marshall: You May Not Need That :around Method
I’ve seen this “anti-pattern” a few times in CLOS
code. A superclass ’super will have a
subclass ’sub and there will be a primary method
specialized to the superclass.
(defmethod foo ((instance super) arg) (format t "~&Foo called on ~s." arg))
Then I’ll see an :around method defined on the
subclass:
(defmethod foo :around ((instance sub) arg) (format t "~&Start foo...~%") (call-next-method) (format t "~&End foo.~%"))The intent here is clearly that code in the method specialized on the subclass is invoked “around” the call to the method specialized on the superclass.
But the :around qualifier is not necessary and
probably doesn’t do what is intended. If we remove
the :around qualifier, then the most specific primary
method will be the foo method specialized
on ’sub. And the (call-next-method)
invokation will chain up to the foo method specialized
on ’super. It will work as was likely intended.
:around methods are useful when
the superclass wants to run a method “around”
the subclass. :around methods are combined from least
specific to most specific — the opposite order of primary
methods — so that the superclass can wrap the call to the
subclass. An good example of where an :around method
would be handy is when you need to sieze a lock around the call to
the method. The superclass would sieze the lock in
an :around method that would run before any of the
subclass primary methods ran.
Ordinary chaining of methods doesn’t need
the :around qualifier. Just chain the methods.
Trivium: 01apr2024
Backdoor in upstream xz/liblzma leading to SSH server compromise, initial writeup of CVE-2024-3094 by Andres Freund.
Everything I Know About the XZ Backdoor, by Evan Boehs.
Timeline of the xz open source attack, by Russ Cox.
xz/liblzma: Bash-stage Obfuscation Explained, by Gynvael Coldwind.
xz backdoor payload analysis, by Filippo Valsorda.
xzbot, exploration of the xz backdoor.
Cloning a laptop over NVME TCP, by copyninja using the Linux
nvemt-tcp module.
RP2040 Boot Sequence, in detail by V. Hunter Adams.
The Mark Williams Company, and the COHERENT operating system.
OldWeb.Today, run ancient browsers in your browser!
Strachey love letter algorithm (1952).
hacklab.to: Junk Independence Day
- Sunday April 14
- 2PM – 7PM
Got some old electronics hiding away at home? Looking for a source of spare parts for a project? Junk Independence Days where people bring in and swap old electronics and e-waste.
Typical / past items included:
- iPods / Mp3 Players / camcorders
- Computers, laptops and parts
- Printers / Scanners
- Stereo amps, speakers
- Traffic walk/don’t walk streetlights!
- Hobby Electronics parts + kits
Not to be forgotten, there are always lots of little chips and bytes for random hacking too. Anything left at the end will be picked up on Monday and responsibly recycled!
House Rules: Items brought in for the Junk Day are not to be disassembled on site. If you want only part of an item, take it home, and bring the rest back next junk day.